Category: CyberDefenseMagazine
We’ve got a hard truth to share with you, and you might not like it: You are not your software…
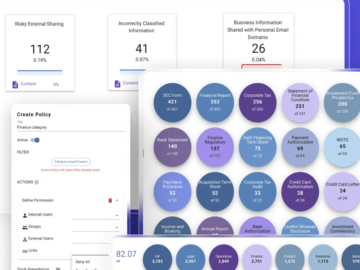
Data security is more critical than ever as organizations manage vast amounts of sensitive information across cloud and on-premises environments….
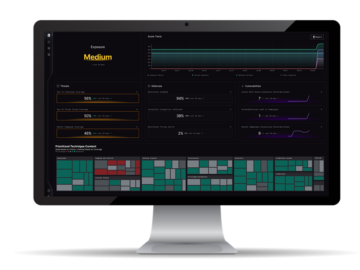
In the current cybersecurity landscape, the focus has shifted from merely managing vulnerabilities to strategically orchestrating defenses against targeted threats….
The ongoing prevalence (and rise) of software supply chain attacks is enough to keep any software developer or security analyst…
I was thrilled to catch up with Proofpoint top executives, recently, to discuss Proofpoint’s AI-powered solution and critical issues including…
Artificial intelligence (AI) has many applications in cybersecurity. Automated fraud detection is one of the most impactful of these use…
The modern Security Operations Center (SOC) has morphed and matured since its infancy in the early 1990s. The primary responsibility…
In today’s rapidly evolving digital landscape, organizations are increasingly reliant on complex networks of identities to power their operations. From…
More than 70 percent of enterprises have prioritized SaaS security by establishing dedicated teams to secure SaaS applications, a trend…
In recent years, third-party breaches have gained significant attention, with high-profile incidents such as the Okta and MOVEit hacks highlighting…
Security testing plays a critical role in ensuring that applications are protected against vulnerabilities and attacks. In times when cyber…
On July 1st, 2024, the cybersecurity community was rocked by the discovery of a critical Remote Code Execution (RCE) vulnerability…