Category: CyberDefenseMagazine
Federal agencies face a pivotal cybersecurity challenge: prevent unauthorized entities from accessing systems and facilities, while granting authorized federal employees…
In today’s rapidly evolving digital landscape, fear, uncertainty, and doubt have become the dominant emotions for many organizations grappling with…
Integrated Governance, Risk, and Compliance Is Critical Business executives in all sectors place a high premium on security in the…
Artificial Intelligence (AI) is transforming multiple sectors, driving innovation and enhancing productivity and cybersecurity. The AI market is projected to…
Artificial Intelligence (AI) is transforming multiple sectors, driving innovation and enhancing productivity and cybersecurity. The AI market is projected to…
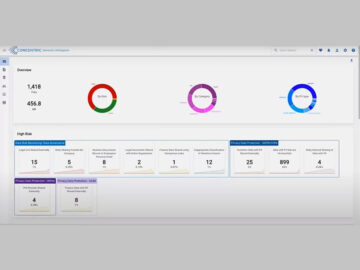
In today’s digital landscape, data security and privacy have become top priorities for organizations of all sizes. According to a…
The recent massive data breach at National Public Data may have exposed anywhere from 1.3 million to 2.9 billion financial records and…
Discussions of insider risk inevitably conjure images of disgruntled IT employees stealing sensitive data from the comfort of an air-conditioned…
1) The Reality of Cybersecurity Threats and Response As technology develops and digitalization progresses, cybersecurity threats are becoming increasingly diverse…
It’s not enough for companies to just discover and monitor sensitive data. They need tools that can proactively fix any…
Arriving on 17th October this year, NIS 2 is the EU’s most stringent cybersecurity Directive so far. Your level of cybersecurity…
It is a tale almost as old as time: users click download, install, and accept as they adopt new software…