Category: CyberDefenseMagazine
As buzz and excitement continues to build around the upcoming 2024 Summer Olympics, it is important to be aware of the…
Payment card data theft remains a huge problem and still accounts for almost a fifth (19%) of breaches, with that…
Ensuring the protection of data and communications is of utmost importance for organisations adapting to the intricacies of the digital…
The importance of internet safety has never been more pronounced than in today’s digital age, where the boundaries between our…
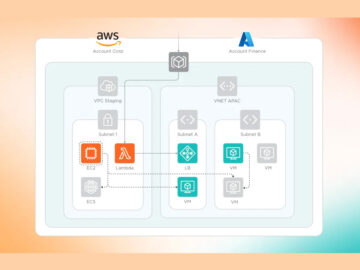
Pioneering Zero Trust Segmentation for Comprehensive Cybersecurity by Samridhi Agarwal, Master’s Student, CMU In today’s rapidly evolving cybersecurity landscape, organizations…
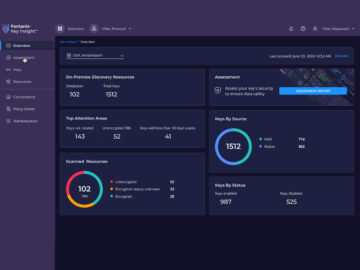
Unveiling Secure Data Practices in a World of AI Risks by Samridhi Agarwal, Master’s Student, CMU In an era where…
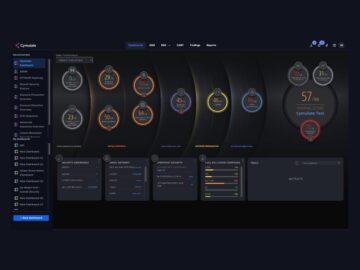
AI Copilot: Revolutionizing Threat Exposure Validation by Samridhi Agarwal, Master’s Student, CMU During BlackHat, Cymulate, a leader in security and…
Recently, the CEO of the world’s biggest advertising group, Mark Read, was the target of a deepfake scam using an AI-based voice…
Prevention is always better than a cure, but no proactive measure is foolproof. Cyberattacks are too frequent and the consequences…
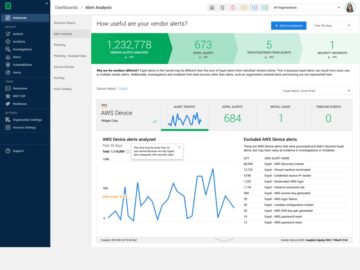
Leading the Charge in Managed Detection and Response by Samridhi Agarwal, Master’s Student, CMU In a conversation with Greg Notch,…
Q&A with OIeria CEO Jim Alkove: Identity is the keystone to the future of cybersecurity and a critical area for…
During my conversation with Lindsay Kaye, VP of Threat Intelligence at HUMAN Security, she emphasized how HUMAN tackles some of…