Category: CyberDefenseMagazine
During my conversation with Lindsay Kaye, VP of Threat Intelligence at HUMAN Security, she emphasized how HUMAN tackles some of…
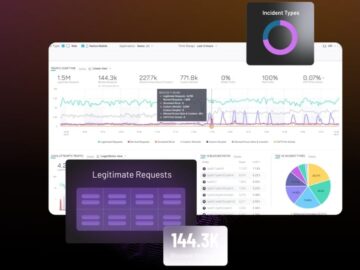
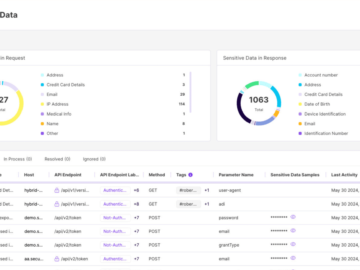
In a world where APIs have become integral to the digital and technical experience, they also represent a significant security…
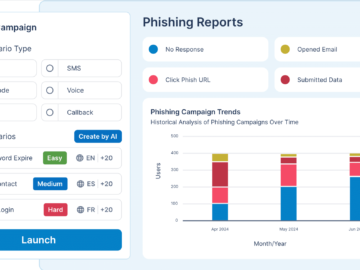
Human error remains one of the most significant vulnerabilities in cybersecurity. Despite advances in technology and automated defenses, employees continue…
During my conversation with Melissa Bischoping, Senior Director of Security & Product Design Research at Tanium, she emphasized how the…
Attending Black Hat 2024 with Cyber Defense Magazine is always an enlightening experience, giving me the opportunity to interview several…
Imagine a world where your inbox isn’t a monster overflowing with junk. A world where you can be confident your…
Artificial intelligence (AI) has rapidly reshaped the cybersecurity landscape and simultaneously presents both exciting advancements while also introducing new challenges….
Among the various factors that contribute to an effective security strategy, threat intelligence collaboration and information sharing play a crucial…
Safeguarding your enterprise’s data operations is more critical than ever. The rise of malicious bot attacks poses a particular threat,…
As cybersecurity threats continue to evolve in the ever-changing cyber landscape, organizations within every industry must implement a comprehensive security…
An All-encompassing Approach to Prevent Breaches Organizations depend deeply on technology and data to run their businesses. The recent transition…
The C-suite drives business strategy and shapes a company’s future. Communication and alignment between key players are paramount, yet silos…