Category: CyberDefenseMagazine
Fraud prevention today is like a game of whack-a-mole. When one fraudster or attack method is stamped out, another arises…
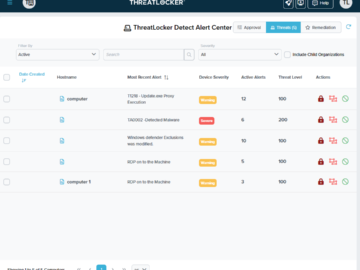
Recent studies have estimated that as many as 90% of successful cyberattacks and 70% of data breaches originate at the endpoint….
As an industry and a society, we are finally making progress in protecting both our digital and physical identities. The…
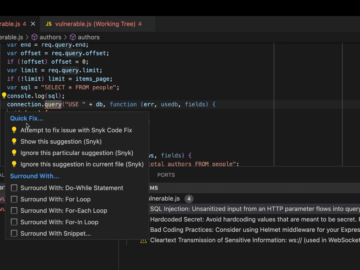
It’s time to give your development process a boost. We’ve all been there staring at a security issue, trying to…
I was thrilled to catch up with Blumira during Black Hat USA 2024. When it comes to resource-constrained businesses, traditional…
At Black Hat 2024, I had the opportunity to speak with Jasson Casey, CEO of Beyond Identity, about their groundbreaking…
Another innovative industry leader I had the pleasure of speaking with was Michael Bargury, Co-Founder and CTO of Zenity, a…
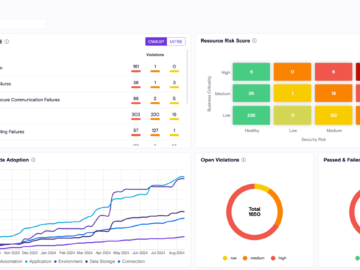
As cloud environments continue to expand, so do the threats targeting them. In today’s fast-paced digital world, attacks on cloud…
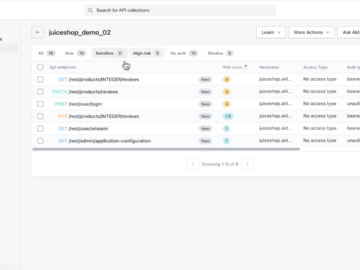
As APIs become the backbone of digital transformation, they also represent one of the biggest security risks to organizations. According…
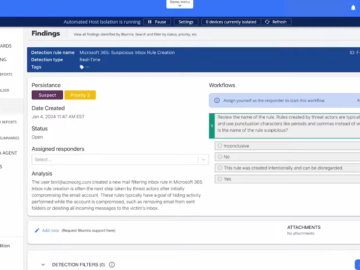
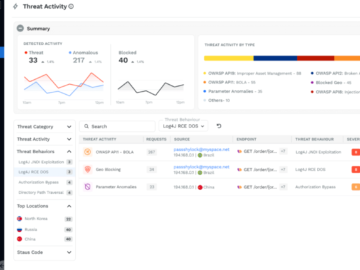
In the rapidly evolving world of cybersecurity, incidents frequently arise when malicious code finds its way into trusted environments. These…
Attending Black Hat 2024 with Cyber Defense Magazine is always an enlightening experience, giving me the opportunity to interview several…
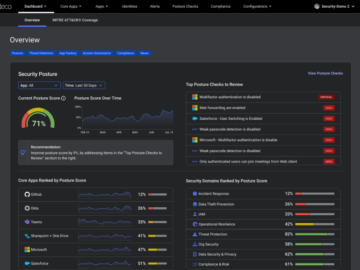
As organizations increasingly rely on SaaS applications, the risk of data breaches and unauthorized access grows significantly. According to a…