Category: CyberDefenseMagazine
The rapid rise of generative AI (GenAI) has brought about both unprecedented opportunities and significant challenges for organizations, particularly in…
The rapid adoption of cloud technology has led to an explosion in complexity and vulnerability within modern infrastructures. In 2022,…
The rapid adoption of AI and Generative AI applications has unlocked tremendous potential, but it has also introduced significant security…
There are events in business and life that put everything else into perspective. Sometimes, these are moments of crisis, yet…
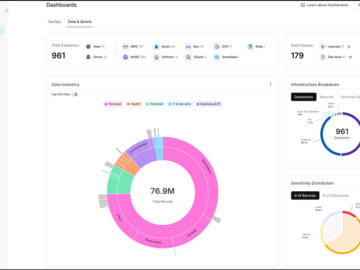
I was thrilled to catch up with Cyera during Black Hat USA 2024. Over 90% of the world’s data was…
I was thrilled to catch up with Cranium during Black Hat USA 2024. CISOs are feeling pressure from their CEOs…
As manufacturing advances into the Industry 4.0 era, the integration of Information Technology (IT) and Operational Technology (OT) necessitates a…
I was thrilled to catch up with Bedrock Security during Black Hat USA 2024. The surge in data volume from…
In November 2022, ChatGPT launched, bringing new possibilities and challenges. As AI and GenAI have grown in popularity and use,…
The vast majority of organisations are well aware of the perils of cybersecurity attacks, whether they take the form of financial, operational, or reputational penalties, and…
I was thrilled to catch up with ForAllSecure during Black Hat USA 2024. ForAllSecure is an organization of hackers, developers,…
If your organization doesn’t already make security a pillar of its culture, this could be the year to start. That’s…