Category: CyberSecurity-Insiders
[ This article was originally published here ] The content of this post is solely the responsibility of the author. …
After hearing a lot from the US government over national security fears, TikTok seems to have come up with answers…
[ This article was originally published here ] In the latest of several recent announcements, the U.S. body responsible for…
[ This article was originally published here ] Business Wire We apologize for the inconvenience. Our team is working to…
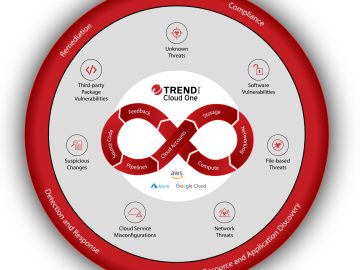
As part of the Cybersecurity Insiders Product Review series, we are today reviewing , a comprehensive and powerful cloud security…
Capita, an internationally acclaimed business processing & outsourcing firm, is experiencing a sudden halt in the operations of its IT…
[ This article was originally published here ] By John Weiler Microsoft patches the “aCropalypse” vulnerability, ChatGPT leaks users’ billing…
Are you one of those who play games by investing real money to earn double or triple the amount in…
Zero trust security has become a buzzword in the cybersecurity world, emphasizing the need for a more robust and reliable…
3CX is urgently working to release a software update in response to the SmoothOperator supply chain attack that targets millions…
Effective Communication with the Board Effective communication is a crucial aspect of delivering a successful cybersecurity presentation to the board…
[ This article was originally published here ] Looking to earn your (ISC)² CISSP certification? Make sure you follow these…