Category: CyberSecurity-Insiders
Cyber Attack Targets Kash Patel Amid FBI Nomination Speculations Kash Patel, a prominent figure linked to Donald Trump and rumored…
In today’s digital age, online accounts have become an integral part of our personal and professional lives. From banking to…
In recent years, we have witnessed a growing trend of surveillance by various entities—ranging from individuals to state actors and…
The United Kingdom’s Ministry of Defense (MoD) has recently made headlines after it was revealed that over 560 staff members’…
Ransomware attacks have become one of the most menacing threats to businesses, governments, and individuals alike. These malicious software programs…
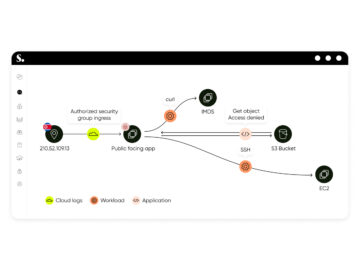
Tel Aviv, ISRAEL, December 3rd, 2024, CyberNewsWire Sweet Security Introduces Evolutionary Leap in Cloud Detection and Response, Releasing First Unified…
Amazon Web Services (AWS), the cloud computing division of Amazon Inc., has introduced a new Security Incident Response service designed…
As Pavel Durov, the founder of Telegram, landed in France, and walked down the stairs of his private jet into…
As Christmas 2024 rapidly approaches, the excitement of holiday shopping is in full swing. While many people have already scored…
Yes, AI can play a significant role in improving the efficiency of detecting and preventing cyberattacks, potentially curbing their impact….
Today’s world is powered by technology. Most day-to-day business operations are underpinned by online systems and digitally stored data. And,…
2025 promises to be a pivotal year for corporate leaders. Technological advancements, geopolitical shifts, and heightened risks demand unprecedented vigilance…