Category: CyberSecurity-Insiders
The digital landscape is evolving rapidly, with it, the threats we face online. As cyberattacks grow in sophistication, so must…
In today’s digital landscape, data privacy and security are top concerns for users, especially those relying on smartphones, as these…
For the past five years, Google, the undisputed titan of the internet, has found itself embroiled in a series of…
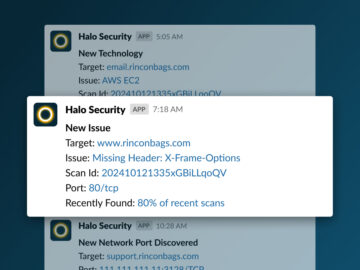
MIAMI, Florida, November 21st, 2024, CyberNewsWire Halo Security, a leader in external attack surface management and penetration testing, has announced…
In recent years, data breaches and the exposure of sensitive information have become a common occurrence, impacting millions of records…
The unfortunate reality is that – for the safety of the people attending – security measures are now an absolute…
SailPoint Technologies, Inc., a recognized leader in enterprise identity security, has unveiled an ambitious new vision for the future of…
In recent years, job postings in the software and IT sectors have become commonplace, with companies constantly searching for skilled…
LockBit Ransomware Breach Exposes Sensitive Data of 21K Equinox Customers Equinox, a prominent healthcare service provider based in New York,…
Businesses are facing increasingly sophisticated threats from ransomware groups, hacktivists, and individual attackers. The 2024 Arctic Wolf Security Operations Report…
Human beings are without doubt the single biggest cybersecurity threat to organizations. About two-thirds of breaches stem from a simple,…
Helldown Ransomware Targets Linux and VMware Server Environments A new variant of ransomware called Helldown, which emerged earlier this year,…