Category: CyberSecurityNews
Pakistan-based threat actor APT36, widely known as Transparent Tribe, has shifted away from carefully crafted tools to a new approach…
Hikvision Multiple Products Vulnerability A severe vulnerability affecting multiple Hikvision products was added to the Known Exploited Vulnerabilities (KEV) catalog…
ExifTool Flaw Malicious Images Trigger Code Execution on macOS A newly discovered vulnerability is challenging the long-held belief that macOS…
CISA Warns macOS and iOS Vulnerabilities Exploit The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical alert regarding…
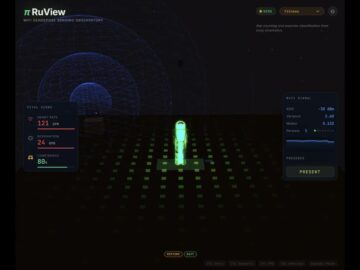
A new open-source edge AI system called π RuView is turning ordinary WiFi infrastructure into a through-wall human-sensing platform detecting…
A threat actor identified as “Kamirmassabi” is allegedly selling a zero-day exploit for a Windows Remote Desktop Services privilege escalation…
Zero-Click Command Injection AVideo Platform Allows Stream Hijacking A critical vulnerability in AVideo, a widely used open-source video hosting and…
Microsoft 365 Outage Hits North America Microsoft is actively investigating a service disruption affecting multiple Microsoft 365 products for users…
Linux rootkits have quietly grown into one of the most dangerous threats facing modern infrastructure. For years, attackers focused primarily…
Artificial intelligence models are rapidly evolving from simple coding assistants into highly capable, autonomous vulnerability researchers. Recently, Anthropic’s Claude Opus…
FBI Investigates Hack The Federal Bureau of Investigation has confirmed a cybersecurity incident targeting a sensitive internal network used to…
Remote Monitoring and Management (RMM) tools are the backbone of modern IT operations. Security professionals rely on them daily to…