Category: CyberSecurityNews
ValleyRAT has emerged as a sophisticated multi-stage remote access trojan targeting Windows systems, with particular focus on Chinese-language users and…
North Korean threat actors are evolving their attack strategies by leveraging developer-focused tools as infection vectors. Recent security discoveries reveal…
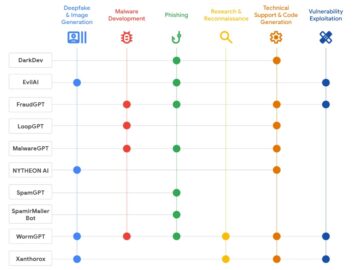
The cybercrime landscape has undergone a dramatic transformation in 2025, with artificial intelligence emerging as a cornerstone technology for malicious…
Security researchers have uncovered a sophisticated new malware family targeting enterprise environments through a supply chain compromise. The malware, tracked…
A sophisticated Remote Access Trojan labeled EndClient RAT has emerged as a significant threat targeting human rights defenders in North…
The Gootloader malware campaign has resurfaced with sophisticated evasion techniques that allow it to bypass automated security analysis. This persistent…
A critical remote code execution (RCE) flaw in three official extensions for Anthropic’s Claude Desktop. These vulnerabilities, affecting the Chrome,…
On November 3, 2025, blockchain security monitoring systems detected a sophisticated exploit targeting Balancer V2’s ComposableStablePool contracts. An attacker executed…
Django, one of the most popular Python web development frameworks, has disclosed two critical security vulnerabilities that could allow attackers…
Cisco has disclosed multiple critical vulnerabilities in Unified Contact Center Express (CCX) that allow unauthenticated remote attackers to execute malicious…
International law enforcement agencies have taken down three sophisticated fraud and money laundering networks in a coordinated operation that uncovered…
Cisco has confirmed that threat actors are actively exploiting a critical remote code execution (RCE) flaw in its Secure Firewall…