Category: CyberSecurityNews
Cybercriminals have launched a sophisticated supply chain attack targeting cryptocurrency developers through malicious Rust crates designed to steal digital wallet…
Cisco warns of a Critical remote code execution flaw in web services across multiple Cisco platforms. Tracked as CVE-2025-20363 (CWE-122),…
Cybersecurity authorities are urging organizations to take immediate action following the discovery of a sophisticated espionage campaign targeting Cisco Adaptive…
Cybercriminals are increasingly turning to artificial intelligence to enhance their attack capabilities, as demonstrated in a sophisticated phishing campaign recently…
Cisco has issued an emergency security advisory warning of active exploitation of a critical zero-day vulnerability in its Secure Firewall…
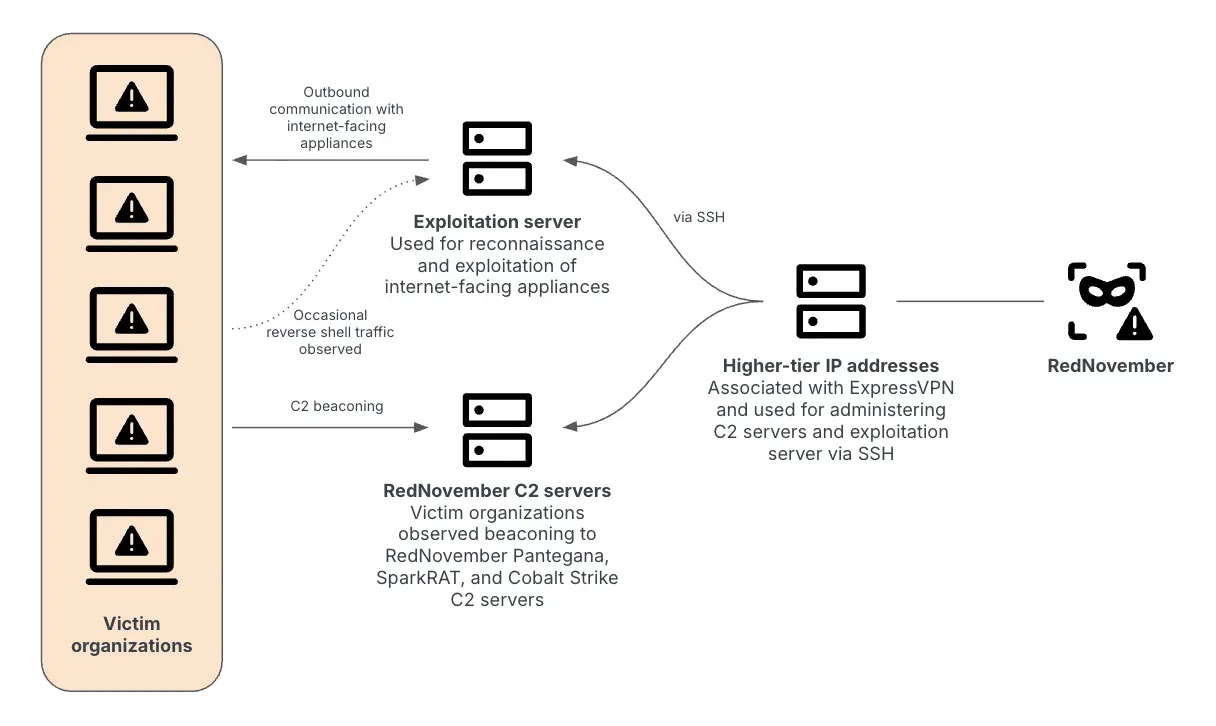
In mid-2024, cybersecurity professionals began observing a surge of targeted intrusions against government, defense, and technology organizations worldwide. These incidents…
A sophisticated phishing campaign has emerged targeting maintainers of packages on the Python Package Index (PyPI), employing domain confusion tactics…
A sophisticated malware campaign orchestrated by the Vietnamese Lone None threat actor group has been leveraging fraudulent copyright infringement takedown…
A sophisticated malware campaign targeting WordPress websites has been discovered employing advanced steganographic techniques and persistent backdoor mechanisms to maintain…
A recent wave of attacks leveraging malicious Windows shortcut files (.LNK) has put security teams on high alert. Emerging in…
Living Security, a global leader in Human Risk Management (HRM), today announced the full speaker lineup for the Human Risk…
A critical vulnerability chain in Salesforce’s Agentforce AI platform, which could have allowed external attackers to steal sensitive CRM data….