Category: CyberSecurityNews
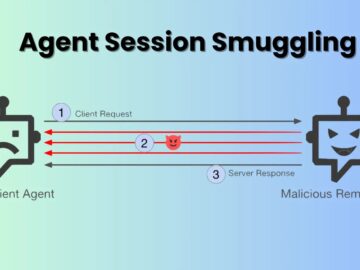
Security researchers have uncovered a sophisticated attack technique that exploits the trust relationships built into AI agent communication systems. The…
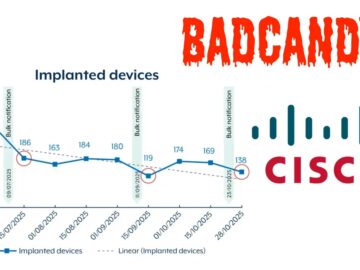
Cybercriminals and state-sponsored actors are ramping up attacks on unpatched Cisco IOS XE devices across Australia, deploying a persistent Lua-based…
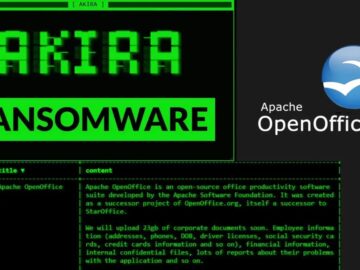
The notorious Akira ransomware group announced on October 29, 2025, that it successfully breached the systems of Apache OpenOffice, exfiltrating…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert about a critical use-after-free vulnerability in the…
Windows Server Update Services (WSUS) vulnerability is actively exploited in the wild. Criminals are using this vulnerability to steal sensitive…
Throughout the first half of 2025, financially motivated threat actors have shifted their approach to intrusions, abandoning traditional implant-heavy methods…
The explosive growth of artificial intelligence has created an unexpected security threat as cybercriminals exploit ChatGPT’s popularity through counterfeit mobile…
In mid-2025, researchers discovered a sophisticated campaign orchestrated by the Chinese state-sponsored threat group BRONZE BUTLER (also known as Tick)…
Google is strengthening its defense against mobile scams with advanced AI-powered protections built directly into Android devices. As cybercriminals become…
Progress Software has released critical security patches addressing a high-severity vulnerability affecting MOVEit Transfer, a widely used enterprise file transfer…
Microsoft has launched Researcher with Computer Use in Microsoft 365 Copilot, marking a significant advancement in autonomous AI technology. This…
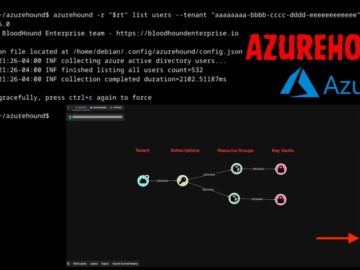
AzureHound, an open-source data collection tool designed for legitimate penetration testing and security research, has become a favored weapon in…