Category: CyberSecurityNews
Amazon Web Services encountered significant operational challenges in its US-EAST-1 region on October 28, 2025, with elevated latencies affecting EC2…
Tel Aviv, Israel, October 29th, 2025, CyberNewsWire Sweet Security Brings Runtime-CNAPP Power to Windows Sweet Security, a leader in Runtime…
Fraudulent investment platforms impersonating cryptocurrency and forex exchanges have emerged as the predominant method used by financially motivated cybercriminals to…
A massive 4TB SQL Server backup file belonging to global accounting giant Ernst & Young (EY) was discovered publicly accessible…
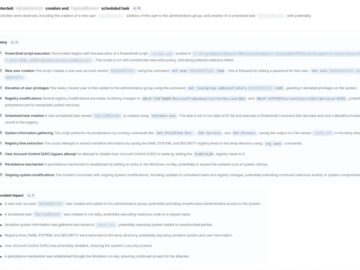
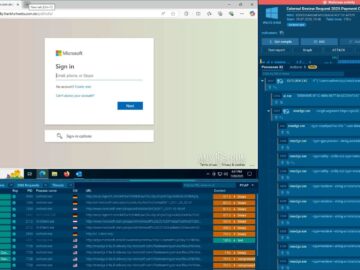
Cybersecurity experts at ANY.RUN recently unveiled alarming trends in how attackers are exploiting everyday technologies to bypass security operations centers…
Ukrainian government organizations continue facing relentless cyber threats from Russian-backed threat actors employing sophisticated evasion techniques to maintain persistent network…
Between August and October 2025, a sophisticated phishing campaign has emerged targeting Colombian and Spanish-speaking users through deceptive emails masquerading…
A newly discovered ransomware-as-a-service platform called Gentlemen’s RaaS has recently emerged on underground hacking forums, offering threat actors a sophisticated…
Microsoft reported a DNS-related outage on October 29, 2025, affecting access to key services, including Microsoft Azure and Microsoft 365….
A groundbreaking security vulnerability has emerged that fundamentally challenges the integrity of modern trusted execution environments across Intel and AMD…
A new open-source tool called HikvisionExploiter has emerged, designed to automate attacks on vulnerable Hikvision IP cameras. Released on GitHub…
The npm ecosystem faces a sophisticated new threat as ten malicious packages have emerged, each designed to automatically execute during…