Category: CyberSecurityNews
A public exploit code demonstrating how attackers could exploit CVE-2025-40778, a critical vulnerability in BIND 9 that enables DNS cache…
Microsoft Exchange servers in Germany are still running without security updates, just weeks after the official end of support for…
Google has announced a significant security initiative that will fundamentally change how Chrome handles unsecured web connections. Beginning with Chrome…
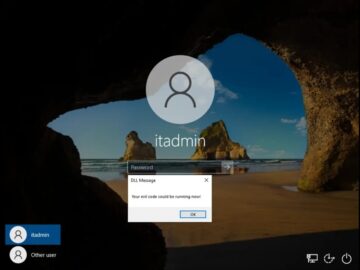
A persistent vulnerability related to DLL hijacking has been identified in the Narrator accessibility tool, which has been a significant…
A persistent vulnerability related to DLL hijacking has been identified in the Narrator accessibility tool, which has been a significant…
The Beast ransomware group has emerged as a significant threat in the cybersecurity landscape, evolving from the Monster ransomware strain…
CISA has added two critical vulnerabilities affecting Dassault Systèmes DELMIA Apriso to its Known Exploited Vulnerabilities catalog, warning that threat…
A threat actor has claimed responsibility for breaching HSBC USA, alleging possession of a vast database containing sensitive customer personal…
A vulnerability in Google Messages on Wear OS devices allows any installed app to silently send SMS, MMS, or RCS…
Australia’s competition regulator has filed legal proceedings against Microsoft for allegedly misleading approximately 2.7 million Australian consumers regarding subscription options…
Microsoft has issued a critical security update for ASP.NET Core to address CVE-2025-55315, a high-severity flaw that enables HTTP request…
Docker Compose, a cornerstone tool for developers managing containerized application harbors a high-severity vulnerability that lets attackers overwrite files anywhere…