Category: CyberSecurityNews
Cybercriminals have developed a sophisticated phishing technique that exploits invisible characters embedded within email subject lines to evade automated security…
Security researcher Eaton Zveare has disclosed critical vulnerabilities in Tata Motors’ systems that exposed over 70 terabytes of sensitive data,…
Pentest Copilot is an innovative open-source tool that leverages AI to help ethical hackers streamline penetration testing workflows. This browser-based…
A sophisticated information-stealing malware named Anivia Stealer has emerged on underground forums, marketed by a threat actor known as ZeroTrace….
Cybersecurity researchers have uncovered a sophisticated phishing campaign that combines two emerging attack techniques to bypass conventional security defenses. The…
A sophisticated Android banking trojan dubbed GhostGrab has emerged in the threat landscape, targeting financial institutions across multiple regions with…
A critical remote code execution (RCE) flaw in XWiki, a popular open-source wiki platform, was exploited in the wild to…
The BlueNoroff threat group, also tracked as Sapphire Sleet, APT38, and TA444, has significantly evolved its targeting capabilities with sophisticated…
Mozilla is implementing a significant transparency requirement for Firefox extensions, mandating that all new browser add-ons disclose their data collection…
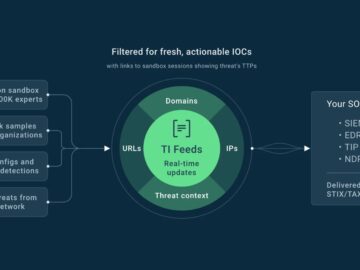
Organizations today face constant threats from malware, including ransomware, phishing attacks, and zero-day exploits. These threats are evolving faster than…
The cybersecurity landscape continues to evolve with increasingly sophisticated distribution mechanisms, and one trend gaining alarming momentum is the delivery…
IPFire 2.29 Core Update 198 marks a significant advancement for users of this open-source firewall, introducing enhanced Intrusion Prevention System…