Category: CyberSecurityNews
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned organizations worldwide about active exploitation of a critical remote code…
A sophisticated malware campaign targeting WordPress sites has emerged, utilizing PHP variable functions and cookie-based obfuscation to evade traditional security…
An international ecosystem of sophisticated scam operations has emerged, targeting vulnerable populations through impersonation tactics and fraudulent financial aid promises….
TransparentTribe, a Pakistani-nexus intrusion set active since at least 2013, has intensified its cyber espionage operations targeting Linux-based systems of…
As the festive season approaches, organizations are witnessing a disturbing increase in targeted attacks on digital gift card systems. The…
The cybersecurity landscape experienced a significant shift in July 2025 when threat actors associated with Warlock ransomware began exploiting a…
A sophisticated Python-based remote access trojan has emerged in the gaming community, disguising itself as a legitimate Minecraft client to…
The SideWinder advanced persistent threat group has emerged with a sophisticated new attack methodology that leverages ClickOnce applications to deploy…
At Pwn2Own Ireland 2025 hacking competition, cybersecurity researchers from Team Z3 have withdrawn their high-stakes demonstration of a potential zero-click…
The Advanced Persistent Threat group MuddyWater, widely recognized as an Iran-linked espionage actor, has orchestrated a sophisticated phishing campaign targeting…
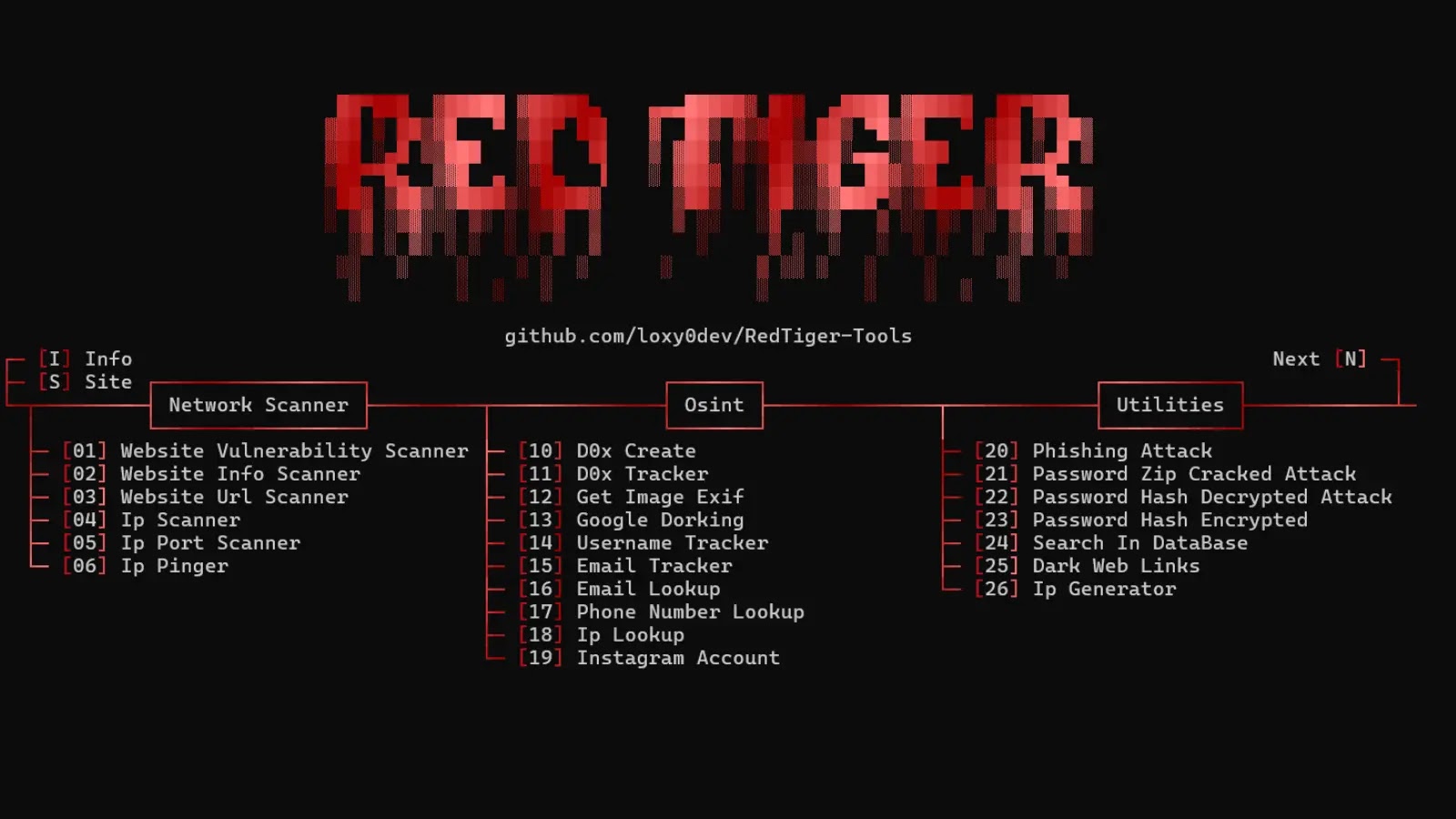
RedTiger is an open-source red-teaming tool repurposed by attackers to steal sensitive data from Discord users and gamers. Released in…
Paris, France, October 24th, 2025, CyberNewsWire Arsen, the cybersecurity company dedicated to helping organizations defend against social engineering, today introduced…