Category: CyberSecurityNews
A sophisticated spearphishing campaign has emerged targeting humanitarian organizations and Ukrainian government agencies, leveraging weaponized PDF attachments and fake Cloudflare…
The hacking community celebrated the end of Pwn2Own Ireland 2025. Researchers demonstrated their skills by identifying 73 unique zero-day vulnerabilities…
Amazon Web Services (AWS), the backbone for countless websites and services, faced a severe outage last weekend that disrupted operations…
Toys “R” Us Canada has alerted customers to a significant data breach that potentially exposed their personal information, marking another…
Email phishing attacks have reached a critical inflection point in 2025, as threat actors deploy increasingly sophisticated evasion techniques to…
Microsoft has rolled out an out-of-band emergency patch for a remote code execution (RCE) vulnerability affecting the Windows Server Update…
Cybersecurity researchers have identified a sophisticated campaign where threat actors are leveraging compromised credentials to infiltrate Azure Blob Storage containers,…
A sophisticated information-stealing malware written in Golang has emerged, leveraging blockchain technology to establish covert command-and-control channels. SharkStealer represents a…
Microsoft 365 Exchange Online’s Direct Send feature, originally designed to enable legacy devices and applications to send emails without authentication,…
The Bitter APT group, also tracked as APT-Q-37 and known in China as 蔓灵花, has launched a sophisticated cyberespionage campaign…
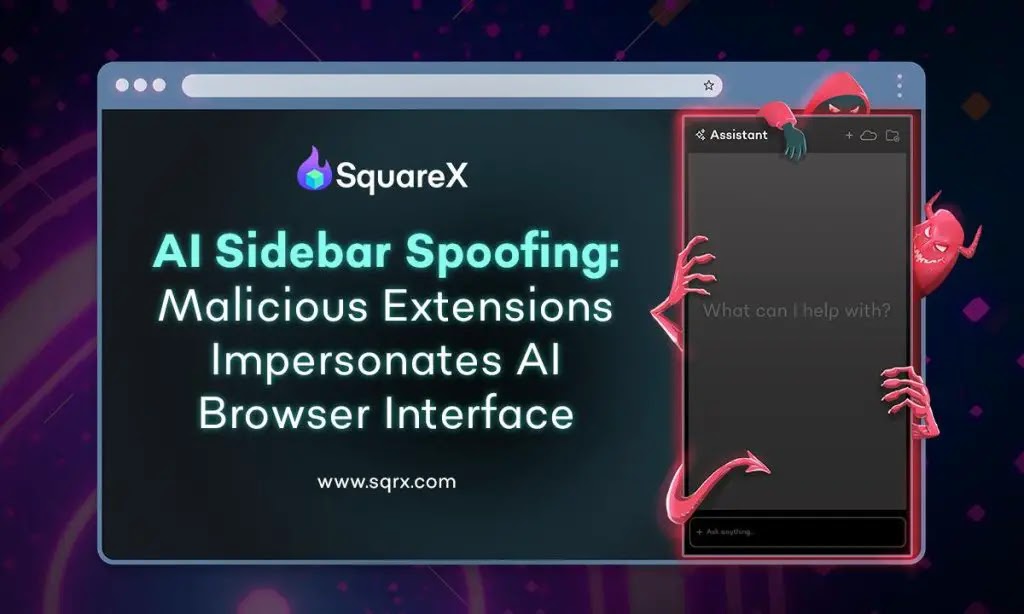
SquareX released critical research exposing a new class of attack targeting AI browsers. The AI Sidebar Spoofing attack leverages malicious…
A new technique allows hackers to extract encrypted authentication tokens from Microsoft Teams on Windows, enabling unauthorized access to chats,…