Category: CyberSecurityNews
A severe vulnerability in the async-tar Rust library and its popular forks, including the widely used tokio-tar. Dubbed TARmageddon and…
The Internet Systems Consortium (ISC) disclosed three high-severity vulnerabilities in BIND 9 on October 22, 2025, potentially allowing remote attackers…
Cloud account takeover attacks have evolved into a sophisticated threat as cybercriminals and state-sponsored actors increasingly weaponize OAuth applications to…
A sophisticated cyberespionage campaign dubbed PassiveNeuron has resurfaced with infections targeting government, financial, and industrial organizations across Asia, Africa, and…
QR codes used to be harmless, now they’re one of the sneakiest ways attackers slip past defenses. Quishing, or QR code phishing, hides malicious…
A critical vulnerability in Smithery.ai, a popular registry for Model Context Protocol (MCP) servers. This issue could have allowed attackers…
A critical argument injection flaw in three unnamed popular AI agent platforms enables attackers to bypass human approval safeguards and…
China-based threat actors have exploited the critical ToolShell vulnerability in Microsoft SharePoint servers to infiltrate networks across multiple continents, targeting…
When users authenticate to Microsoft cloud services, their activities generate authentication events recorded across multiple logging systems. Microsoft Entra sign-in…
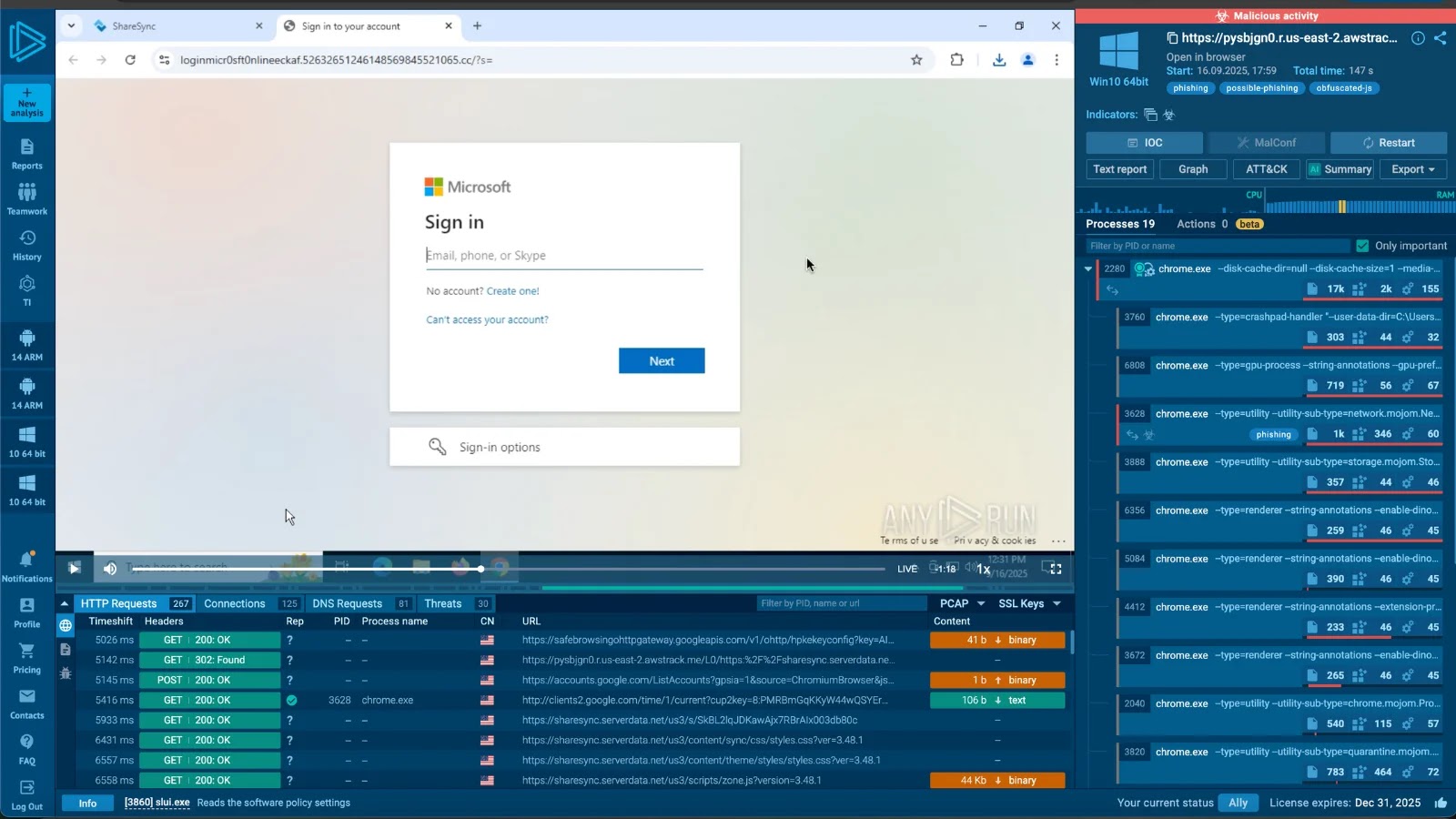
A sophisticated phishing kit dubbed Tykit, which impersonates Microsoft 365 login pages to harvest corporate credentials. First detected in May…
Since its emergence in August 2022, Lumma Infostealer has rapidly become a cornerstone of malware-as-a-service platforms, enabling even unskilled threat…
GitLab has urgently released patch versions 18.5.1, 18.4.3, and 18.3.5 for its Community Edition (CE) and Enterprise Edition (EE) to…