Category: CyberSecurityNews
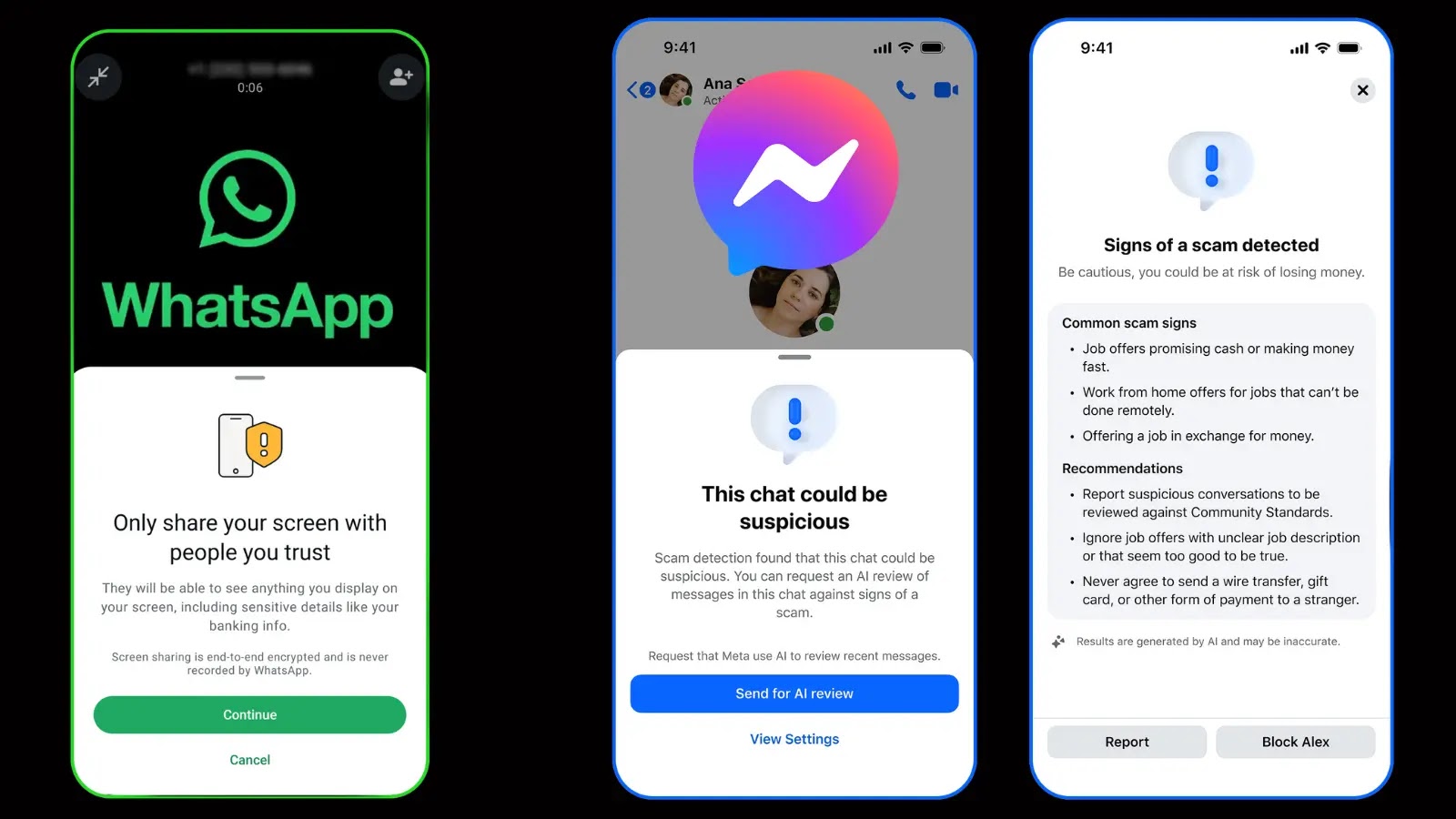
Meta announced innovative tools on Tuesday to shield users of Messenger and WhatsApp from scammers. The updates, revealed during Cybersecurity…
A sophisticated vulnerability in Microsoft 365 Copilot (M365 Copilot) that allows attackers to steal sensitive tenant data, including recent emails,…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a high-priority alert about a critical vulnerability in multiple Apple products….
A severe vulnerability in the popular better-auth library’s API keys plugin enables attackers to generate privileged credentials for any user…
Apache Syncope, an open-source identity management system, has been found vulnerable to remote code execution (RCE) through its Groovy scripting…
Wilmington, Delaware, October 21st, 2025, CyberNewsWire Sendmarc has announced the appointment of Dan Levinson as Customer Success Director – North…
Motex has disclosed a severe remote code execution vulnerability in its LANSCOPE Endpoint Manager On-Premise Edition. Assigned CVE-2025-61932, the flaw…
Over the summer of 2025, a novel malware family emerged following the public disclosure of the LOSTKEYS implant. This new…
Over the past several months, cybersecurity researchers have observed a surge of fraudulent Chrome extensions masquerading as legitimate WhatsApp Web…
Microsoft has disclosed a serious security flaw in ASP.NET Core that enables authenticated attackers to smuggle HTTP requests and evade…
A critical vulnerability in Zyxel’s ATP and USG series firewalls that allows attackers to bypass authorization controls and access sensitive…
A persistent campaign targeting Microsoft Remote Desktop Protocol (RDP) services, with attackers deploying over 30,000 new IP addresses daily to…