Category: CyberSecurityNews
A critical vulnerability in Axis Communications’ Autodesk Revit plugin has exposed Azure Storage Account credentials, creating significant security risks for…
Scattered Lapsus$ Hunters, a threat group previously associated with high-profile data thefts, recently claimed responsibility for exfiltrating over one billion…
The cybersecurity landscape witnessed a concerning development as threat actors discovered a novel attack vector targeting Microsoft Edge’s Internet Explorer…
Linus Torvalds has announced the release of Linux 6.18-rc1, marking the start of the release candidate phase for the upcoming…
North Korean state-sponsored threat actors have intensified their supply chain attacks against software developers through a sophisticated campaign dubbed “Contagious…
Security researchers have identified a sophisticated malware campaign that exploits WhatsApp’s messaging platform to deploy banking trojans targeting Brazilian financial…
A critical vulnerability in Lenovo’s Dispatcher drivers has come under the spotlight after researchers released a proof-of-concept exploit that demonstrates…
A critical vulnerability in AMD’s Secure Encrypted Virtualization with Secure Nested Paging (SEV-SNP), a cornerstone of confidential computing deployed by…
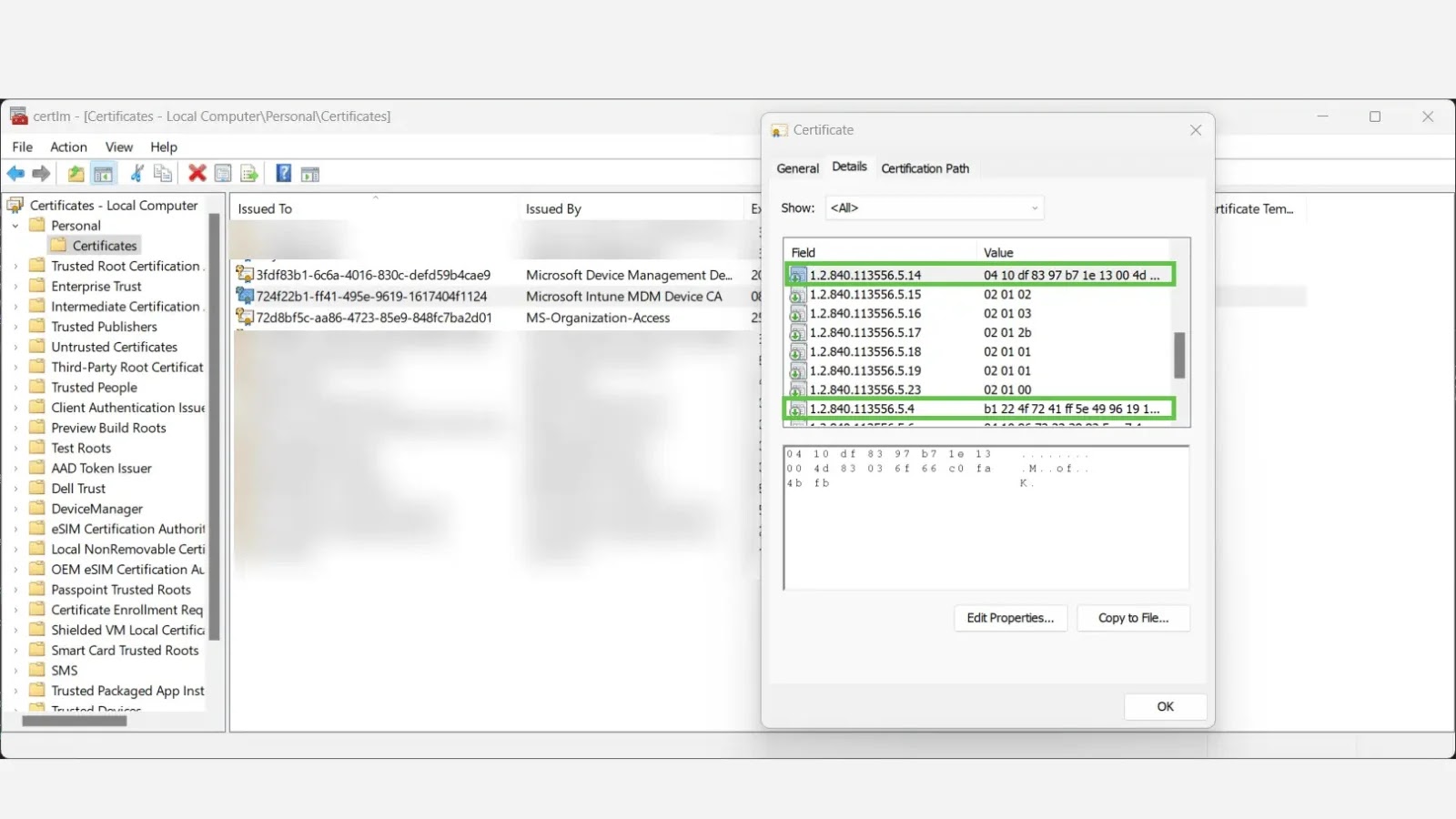
New research uncovers valuable insights hidden within Microsoft Intune’s Mobile Device Management (MDM) certificates, offering a more reliable way to…
A new wave of the Astaroth banking trojan has emerged, leveraging a novel approach to distribute its malicious configuration files….
Cybercriminals have discovered a novel way to co-opt Discord webhooks as surrogate command-and-control (C2) channels across popular language ecosystems. Unlike…
A recent analysis from researcher Itamar Hällström has revealed the technical workings and forensic trail of “EDR-Freeze,” a proof-of-concept technique…