Category: CyberSecurityNews
A critical SQL injection vulnerability in FreePBX has emerged as a significant threat to VoIP infrastructure worldwide, enabling attackers to…
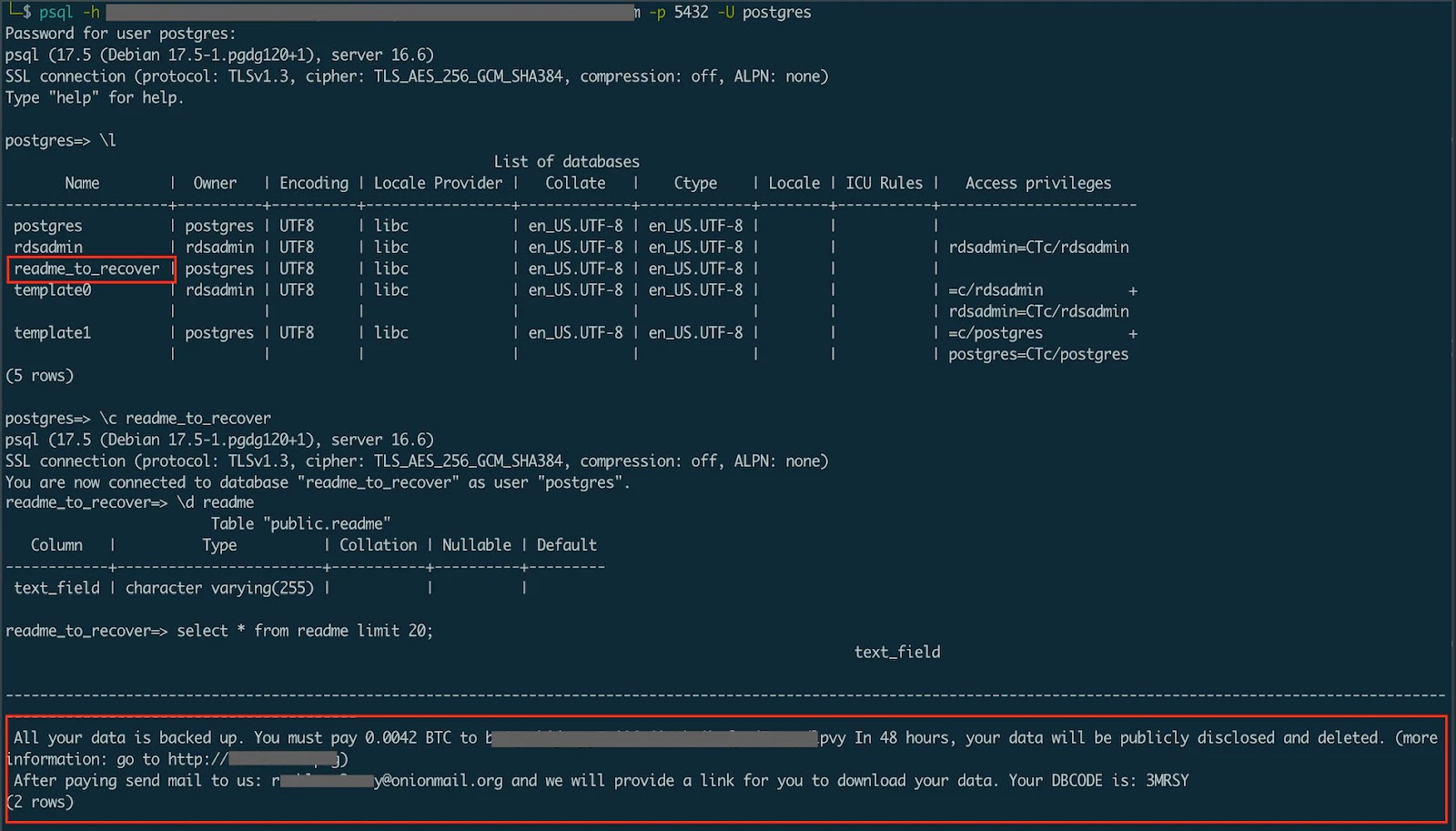
A sophisticated new breed of ransomware attacks is leveraging legitimate database commands to compromise organizations worldwide, bypassing traditional security measures…
The notorious cybercriminal collective known as Scattered Lapsus$ Hunters has escalated their extortion campaign by launching a dedicated leak site…
In recent weeks, cybersecurity analysts have observed a resurgence of the Mustang Panda threat actor deploying a novel DLL side-loading…
Tel Aviv, Israel, October 8th, 2025, CyberNewsWire Miggo Security, pioneer and innovator in Application Detection & Response (ADR) and AI…
Generative AI has gone from a novelty to a foundation of organization efficiency in just a few short years. From…
Security teams are constantly on the move. Alerts never stop coming in, workloads keep piling up, and the pressure to…
A sophisticated cyberattack campaign, active since August 2025, where a China-nexus threat actor has been weaponizing a legitimate server operations…
A critical flaw in the AWS Client VPN for macOS has been disclosed, presenting a local privilege escalation risk to…
Cisco has announced the release of ClamAV 1.5.0, a significant update to the open-source antivirus engine that introduces major security…
Google has introduced CodeMender, a new artificial intelligence-powered agent that automatically enhances software security by identifying and fixing vulnerabilities. This…
A China-aligned advanced persistent threat (APT) group is actively leveraging OpenAI’s ChatGPT platform to develop malware and craft sophisticated spear-phishing…