Category: CyberSecurityNews
A critical zero-day vulnerability in Oracle E-Business Suite has emerged as a significant threat to enterprise environments, with proof-of-concept (PoC)…
A zero-day vulnerability in the Zimbra Collaboration Suite (ZCS) was actively exploited in targeted attacks earlier in 2025. The flaw,…
Microsoft has announced a significant security enhancement for Outlook users, implementing the retirement of inline SVG image support across Outlook…
Unity Technologies has issued a critical security advisory warning developers about a high-severity vulnerability affecting its widely used game development…
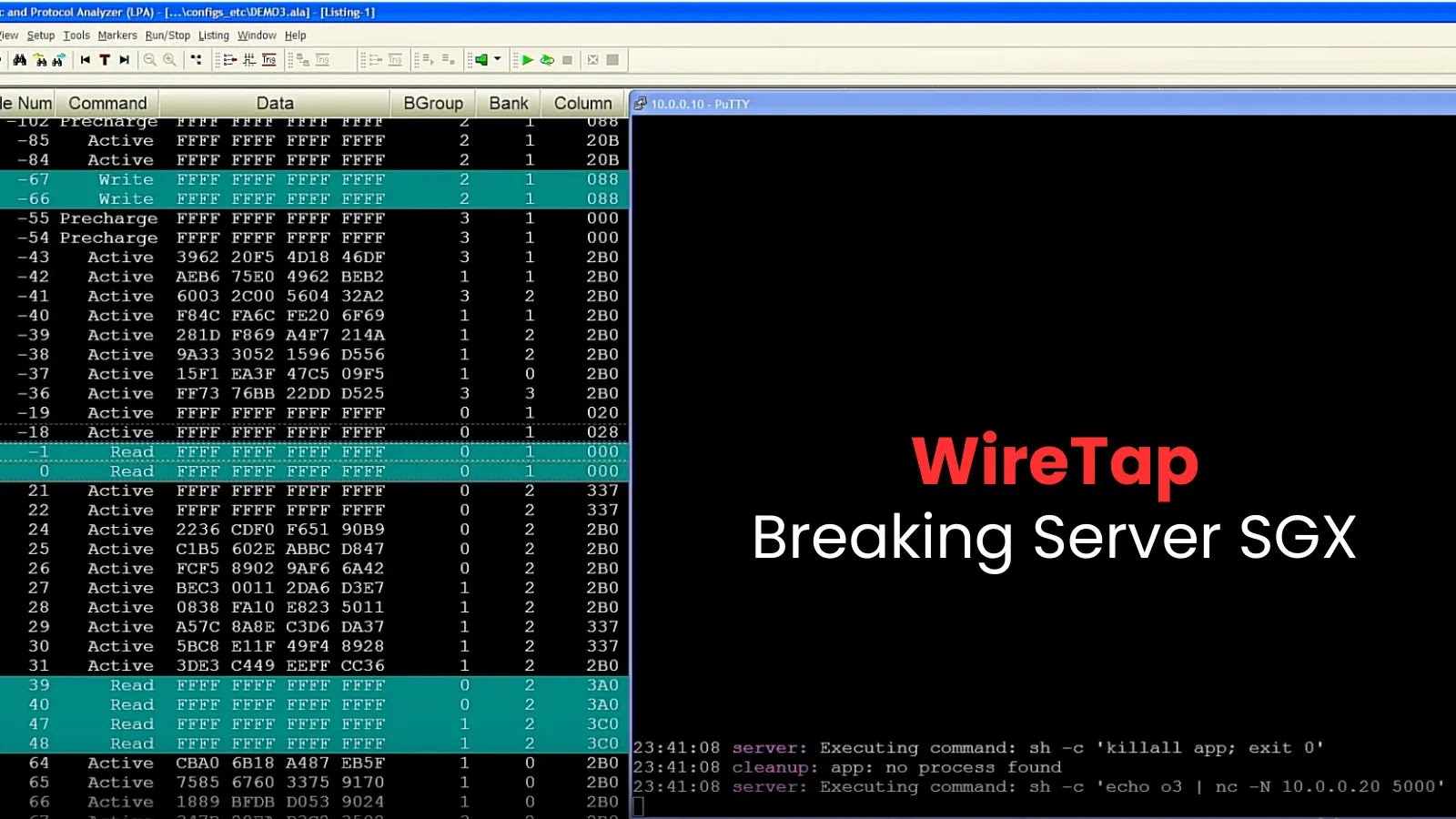
A newly disclosed vulnerability, named the WireTap attack, allows attackers with physical access to break the security of Intel’s Software…
A groundbreaking cybersecurity vulnerability has emerged that transforms Perplexity’s AI-powered Comet browser into an unintentional collaborator for data theft. Security…
A data breach at a third-party customer service provider has exposed the personal data of some Discord users, including names,…
Renault UK has notified customers of a data breach after a cyberattack on one of its third-party service providers resulted…
A cybercrime collective known as Scattered LAPSUS$ Hunters has launched a new data leak site on the dark web, claiming…
Grafana, the popular open-source analytics and visualization platform, has once again become the target of a large‐scale, coordinated exploitation effort. …
An operator known as GhostSocks advertised a novel Malware-as-a-Service (MaaS) on the Russian cybercrime forum XSS.is on October 15, 2023,…
AmCache plays a vital role in identifying malicious activities in Windows systems. This tool allows the identification of both benign…