Category: CyberSecurityNews
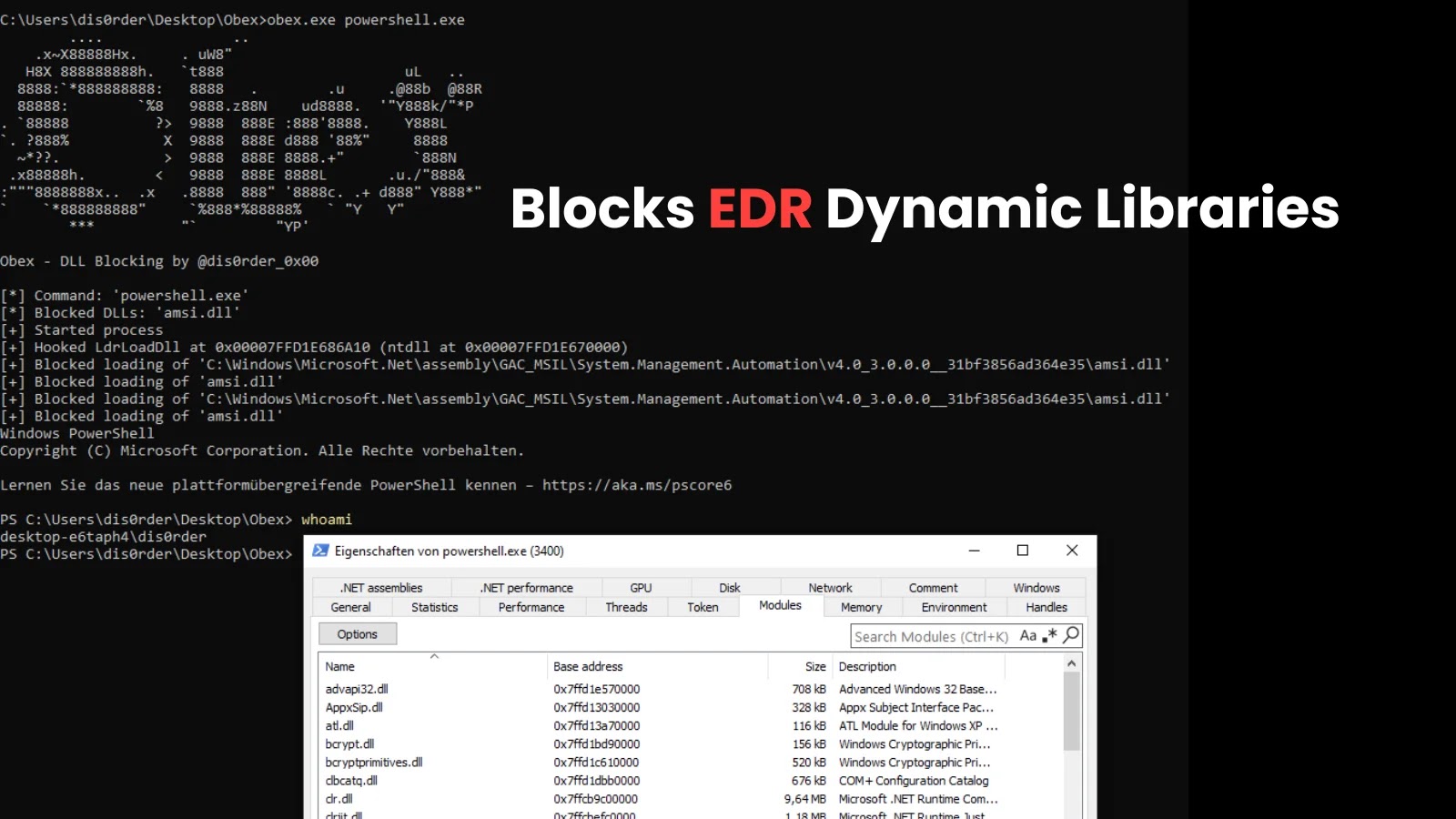
A new proof-of-concept (PoC) tool named Obex has been released, offering a method to prevent Endpoint Detection and Response (EDR)…
An extortion group known as the Crimson Collective claims to have breached Red Hat’s private GitHub repositories, making off with…
Google has released Chrome 141 to address 21 security vulnerabilities, including critical flaws that could allow attackers to crash browsers…
Microsoft has confirmed it is investigating a significant bug in the classic Outlook for Windows desktop client that causes the…
Splunk has released patches for multiple vulnerabilities in its Enterprise and Cloud Platform products, some of which could allow attackers…
Google has published a comprehensive guide aimed at fortifying organizational defenses against UNC6040, a sophisticated threat actor known for targeting…
A sophisticated malicious package has infiltrated the Python Package Index (PyPI), masquerading as a legitimate SOCKS5 proxy tool while harboring…
Ukrainian security agencies have issued an urgent warning regarding a sophisticated malware campaign targeting government and critical infrastructure sectors through…
Cybersecurity researchers have uncovered a sophisticated Android malware campaign targeting seniors through fraudulent travel and social activity promotions on Facebook….
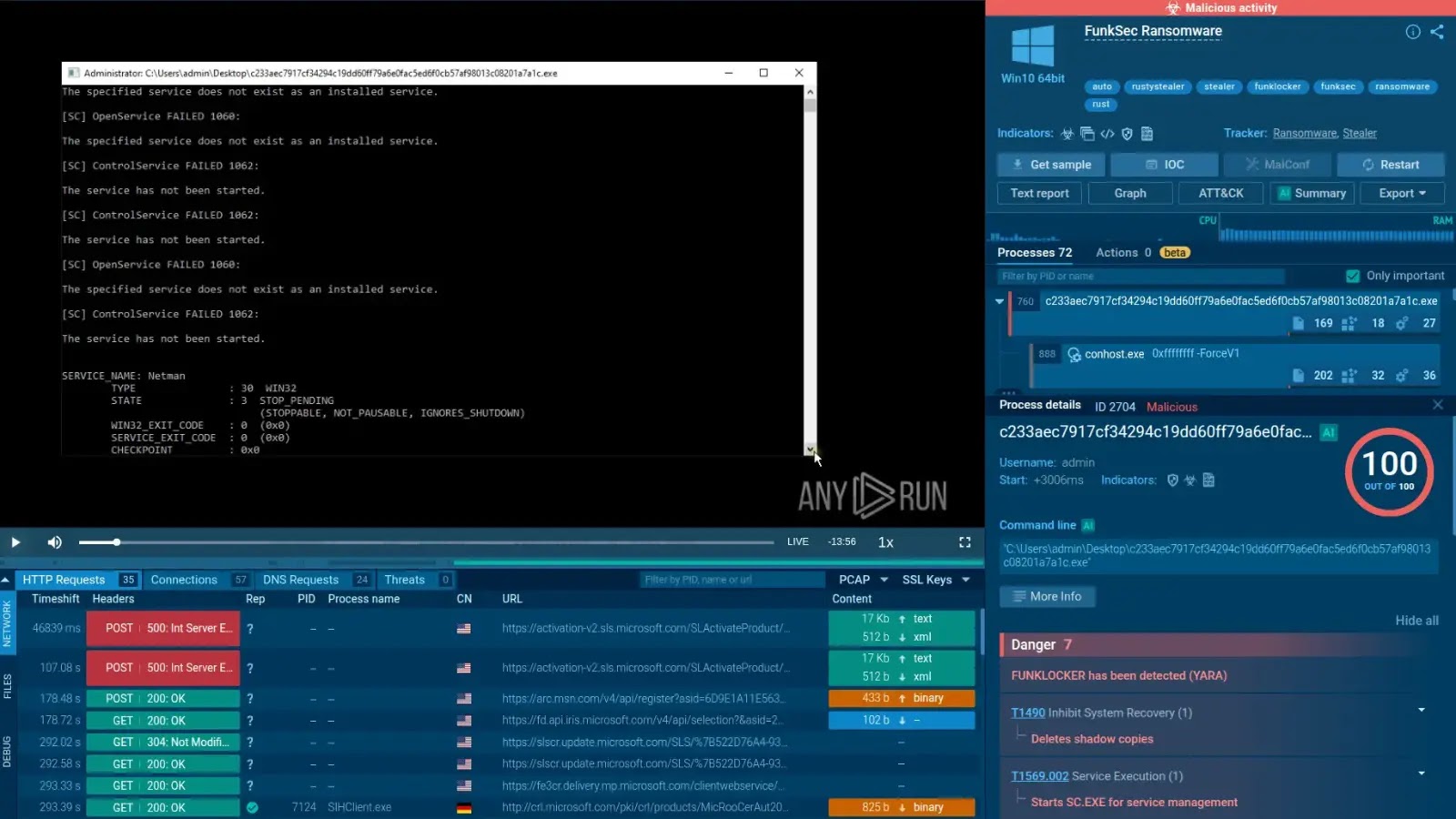
A new ransomware strain, dubbed FunkLocker, is leveraging artificial intelligence to expedite its development, while relying on the abuse of…
In recent weeks, security analysts have observed a new wave of macOS attacks leveraging legitimately issued Extended Validation (EV) certificates…
A sophisticated DNS-based malware campaign has emerged, utilizing thousands of compromised websites worldwide to deliver the Strela Stealer information-stealing malware…