Category: CyberSecurityNews
A concerning cybersecurity trend has emerged as threat actors exploit the growing popularity of artificial intelligence tools by distributing malicious…
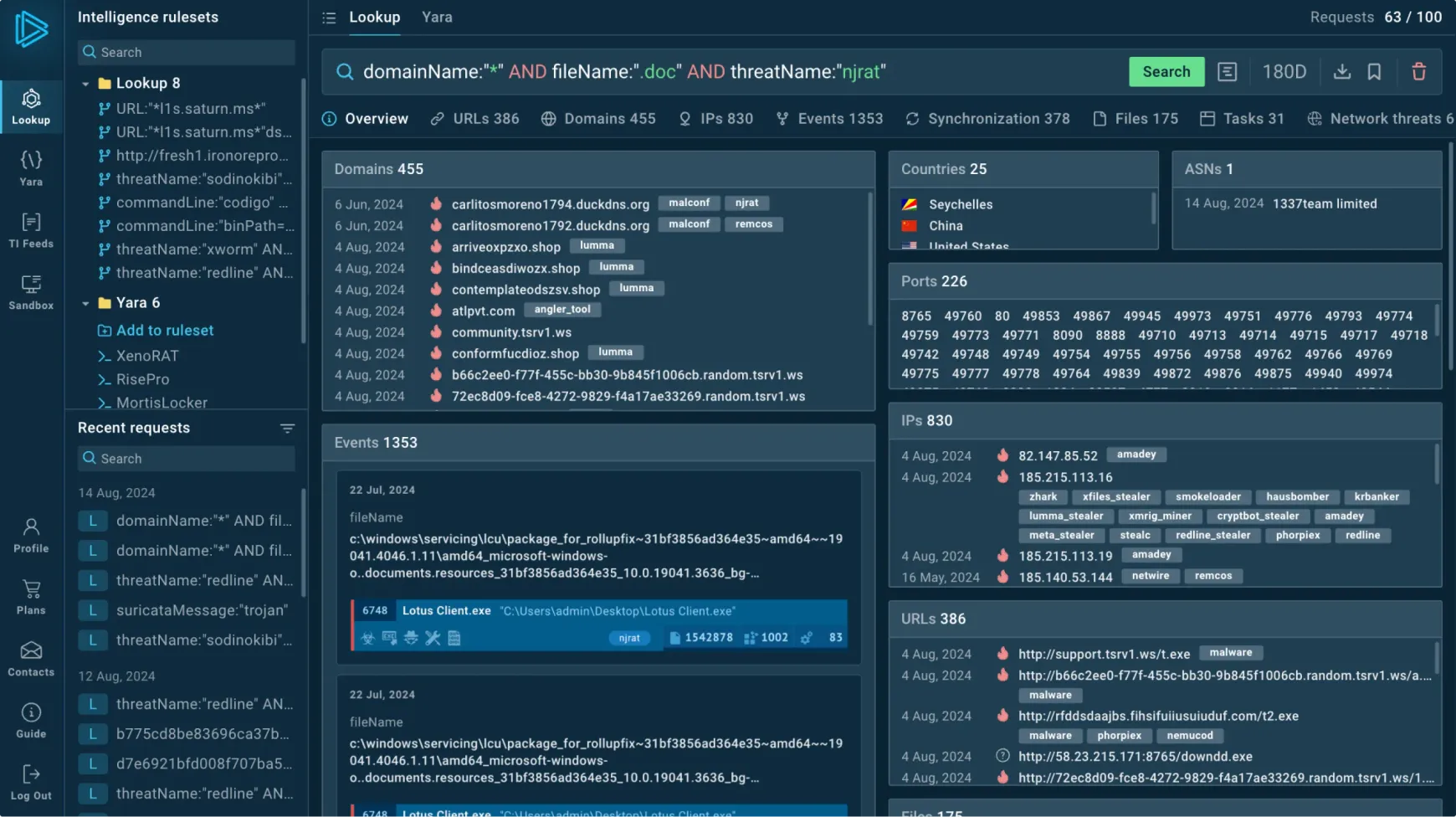
A sophisticated attack campaign targeting improperly managed Microsoft SQL servers has emerged, deploying the XiebroC2 command and control framework to…
In late September 2025, the Cybersecurity and Infrastructure Security Agency (CISA) issued a public alert regarding the active exploitation of…
In recent months, a surge in targeted intrusions attributed to the Iranian-aligned threat group APT35 has set off alarm bells…
Security Operations Centers (SOCs) protect organizations’ digital assets from ongoing cyber threats. To assess their effectiveness, SOCs use key performance…
Veeam Backup & Replication, a cornerstone of many enterprises’ data protection strategy, has reportedly become the focus of a new…
Three new vulnerabilities in Google’s Gemini AI assistant suite could have allowed attackers to exfiltrate users’ saved information and location…
CISA has issued an urgent advisory regarding a critical vulnerability in the Linux and Unix sudo utility CVE-2025-32463 that is…
Linux Torvalds has announced the release of Linux Kernel 6.17, a new version focused on stability and incremental improvements rather…
Security researchers are observing a significant increase in internet-wide scans targeting the critical PAN-OS GlobalProtect vulnerability (CVE-2024-3400). Exploit attempts have…
A security vulnerability in Tesla’s Telematics Control Unit (TCU) allowed attackers with physical access to bypass security measures and gain…
Lunar Spider, a newly observed malware strain, has emerged as a potent threat to Windows environments by compromising systems in…