Category: CyberSecurityNews
VMware has disclosed critical security vulnerabilities in vCenter Server and NSX platforms that could allow attackers to enumerate valid usernames…
VMware has released an advisory to address three high-severity vulnerabilities in VMware Aria Operations, VMware Tools, VMware Cloud Foundation, VMware…
A zero-day local privilege escalation vulnerability in VMware Tools and VMware Aria Operations is being actively exploited in the wild….
Western Digital has released security updates for a critical vulnerability affecting multiple My Cloud network-attached storage (NAS) devices. The flaw,…
Apple has rolled out security updates across its operating systems to address a vulnerability in the Font Parser component that…
The cybersecurity community is currently observing a surge in interest around Olymp Loader, a recently unveiled Malware-as-a-Service (MaaS) platform written…
A sophisticated cyber campaign is exploiting the trust users place in popular collaboration software, tricking them into downloading a weaponized…
Luxury department store Harrods has disclosed a significant data breach affecting approximately 430,000 customer records after a third-party provider was…
A sophisticated malware campaign has emerged that weaponizes seemingly legitimate productivity tools to infiltrate systems and steal sensitive information. The…
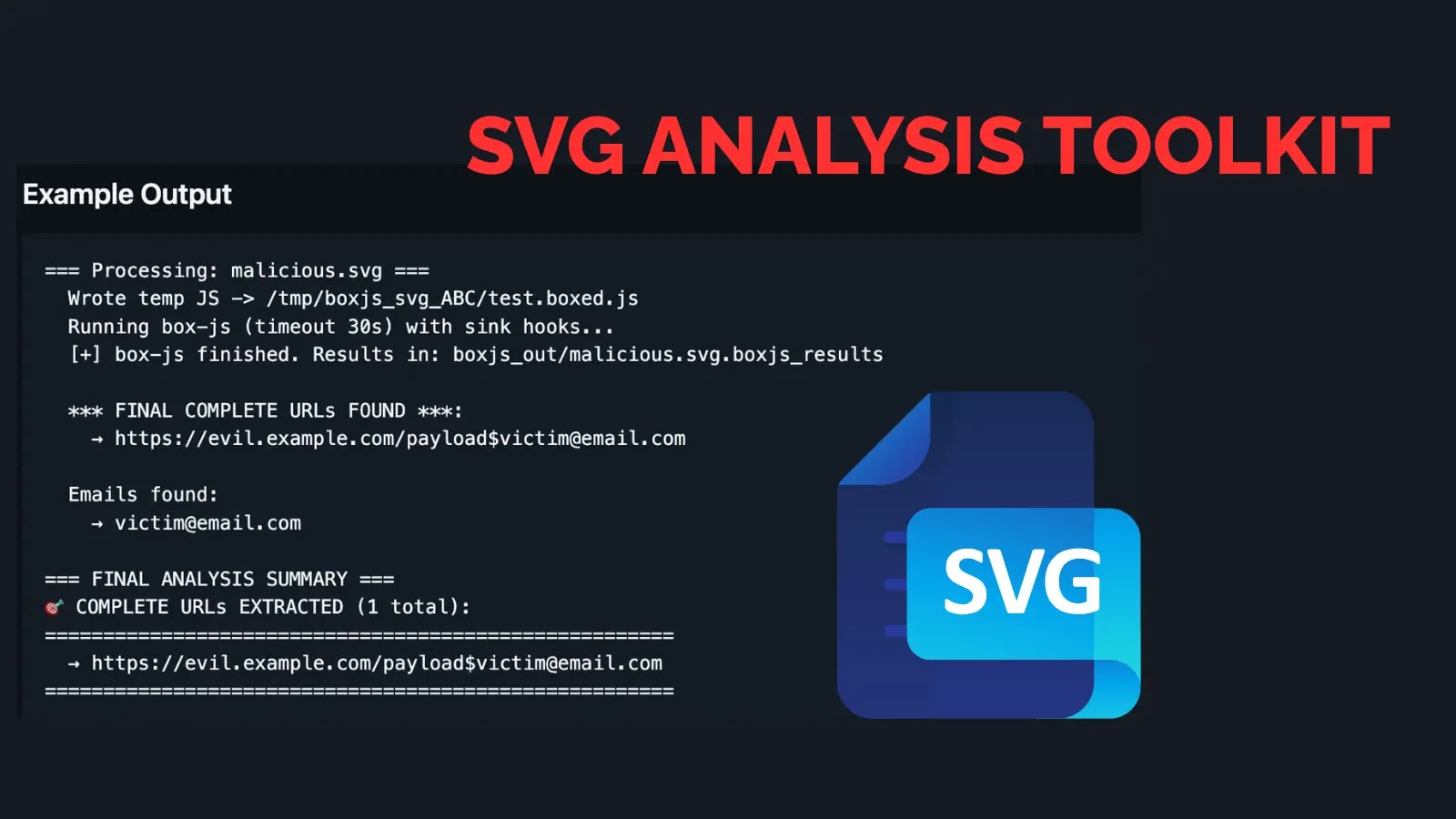
As attackers increasingly leverage Scalable Vector Graphics (SVG) for stealthy code injection, security researchers face mounting challenges in detecting obfuscated…
A newly observed spear-phishing campaign is leveraging sophisticated social engineering lures to distribute DarkCloud, a modular malware suite designed to…
Jaguar Land Rover (JLR) has confirmed it will begin a phased restart of its manufacturing operations in the coming days,…