Category: CyberSecurityNews
Active Directory (AD) remains the foundation of authentication and authorization in Windows environments. Threat actors targeting the NTDS.dit database can harvest…
CISA has issued an Emergency Directive mandating immediate action to mitigate two critical zero-day vulnerabilities, CVE-2025-20333 and CVE-2025-20362, actively exploited against Cisco Adaptive Security…
In late 2024, a new wave of cyber espionage emerged targeting global telecommunications infrastructure. Operating under the moniker Salt Typhoon,…
Cybercriminals have launched a sophisticated supply chain attack targeting cryptocurrency developers through malicious Rust crates designed to steal digital wallet…
Cisco warns of a Critical remote code execution flaw in web services across multiple Cisco platforms. Tracked as CVE-2025-20363 (CWE-122),…
Cybersecurity authorities are urging organizations to take immediate action following the discovery of a sophisticated espionage campaign targeting Cisco Adaptive…
Cybercriminals are increasingly turning to artificial intelligence to enhance their attack capabilities, as demonstrated in a sophisticated phishing campaign recently…
Cisco has issued an emergency security advisory warning of active exploitation of a critical zero-day vulnerability in its Secure Firewall…
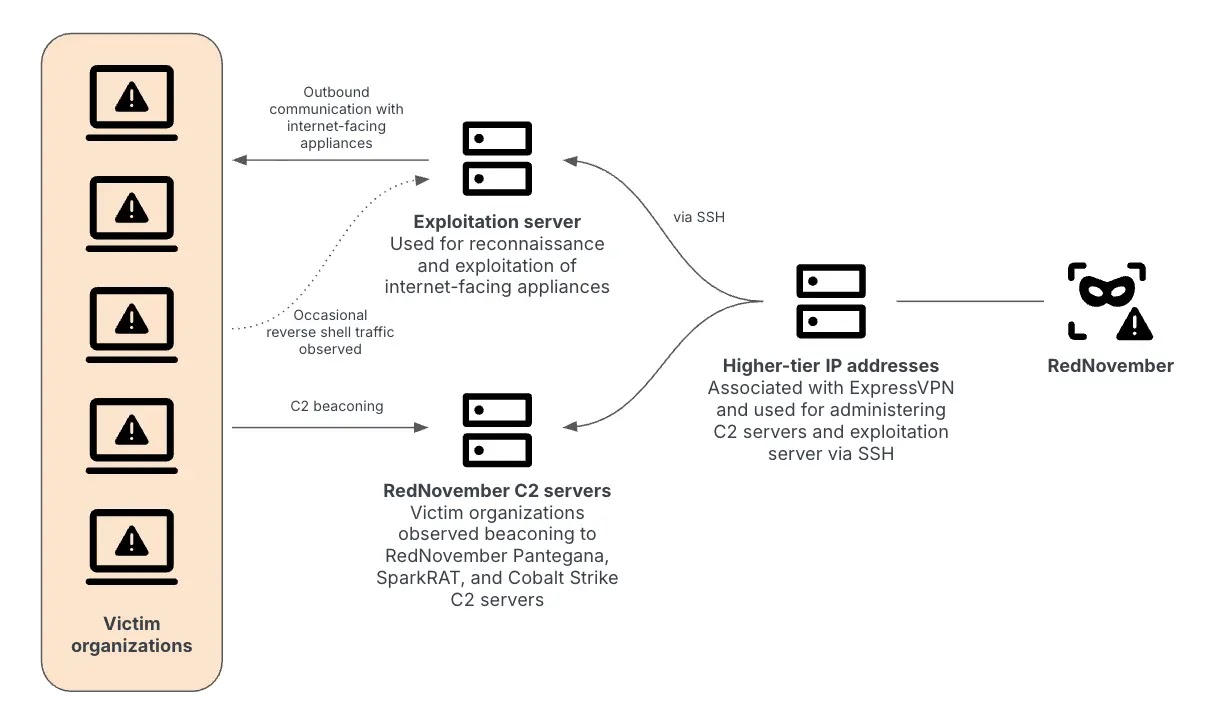
In mid-2024, cybersecurity professionals began observing a surge of targeted intrusions against government, defense, and technology organizations worldwide. These incidents…
A sophisticated phishing campaign has emerged targeting maintainers of packages on the Python Package Index (PyPI), employing domain confusion tactics…
A sophisticated malware campaign orchestrated by the Vietnamese Lone None threat actor group has been leveraging fraudulent copyright infringement takedown…
A sophisticated malware campaign targeting WordPress websites has been discovered employing advanced steganographic techniques and persistent backdoor mechanisms to maintain…