Category: CyberSecurityNews
Living Security, a global leader in Human Risk Management (HRM), today announced the full speaker lineup for the Human Risk…
A critical vulnerability chain in Salesforce’s Agentforce AI platform, which could have allowed external attackers to steal sensitive CRM data….
A critical vulnerability chain in Salesforce’s Agentforce AI platform, which could have allowed external attackers to steal sensitive CRM data….
Cybercriminals have orchestrated a sophisticated phishing campaign exploiting GitHub’s notification system to impersonate the prestigious startup accelerator Y Combinator, targeting…
A critical vulnerability in the implementation of the TACACS+ protocol for Cisco IOS and IOS XE Software could allow an…
BRICKSTORM has surfaced as a highly evasive backdoor targeting organizations within the technology and legal industries, exploiting trust relationships to…
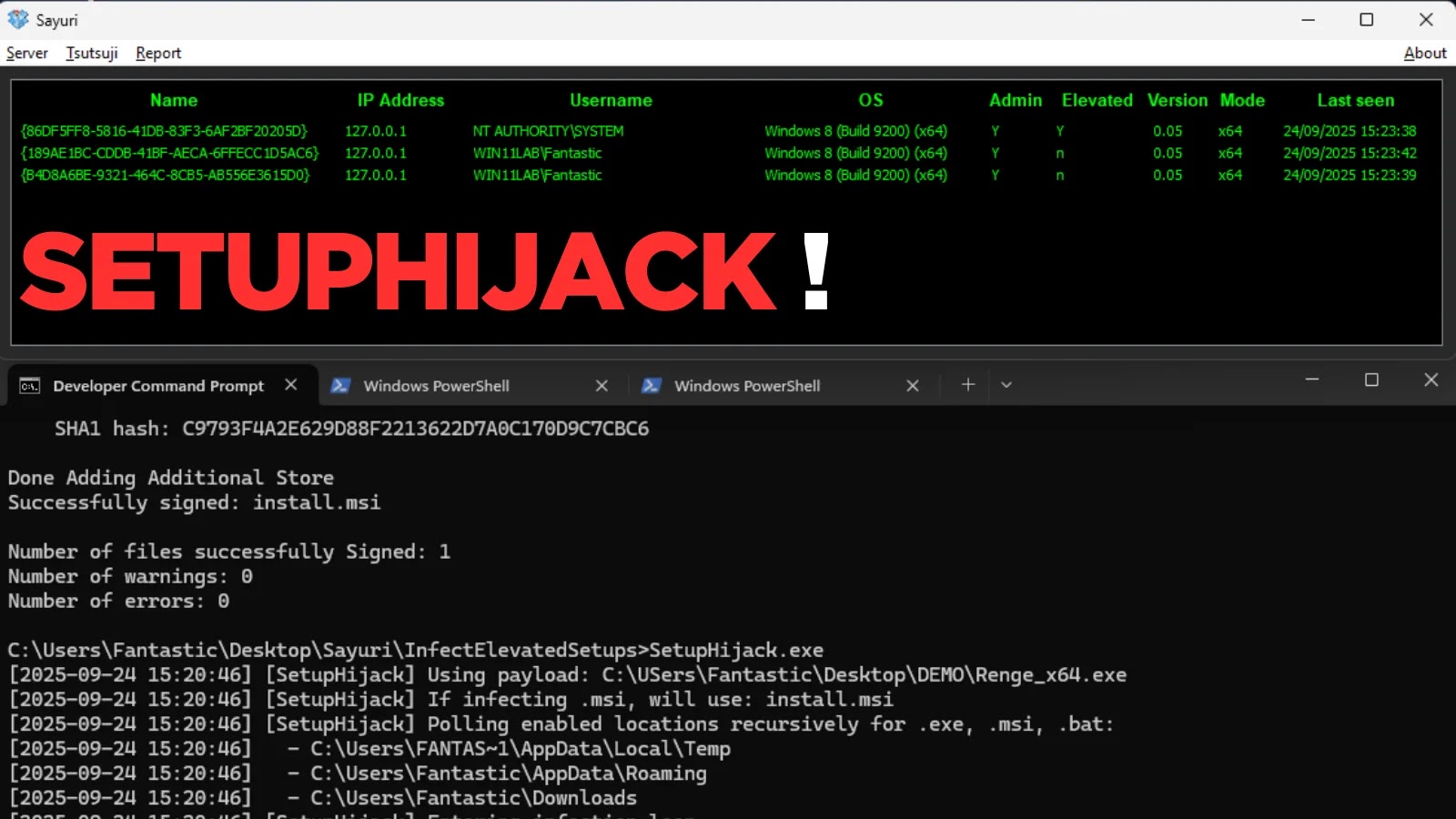
SetupHijack, an open-source research utility, has emerged as a powerful method for red teaming and security research by targeting race…
Following a major law enforcement disruption in February 2024, the notorious LockBit ransomware group has resurfaced, marking its sixth anniversary…
A critical path traversal flaw in ZendTo has been assigned CVE-2025-34508 researchers discovered that versions 6.15–7 and prior enable authenticated…
In recent weeks, security researchers have observed a surge in targeted attacks attributed to the COLDRIVER advanced persistent threat (APT)…
Volvo Group North America has begun notifying employees and associates about a data breach that exposed their personal information, including…
Luxembourg, Luxembourg, September 25th, 2025, CyberNewsWire Gcore, the global edge AI, cloud, network, and security solutions provider, today announced the…