Category: CyberSecurityNews
In recent weeks, cybersecurity teams have observed a surge in malicious GitHub repositories masquerading as legitimate security and financial software….
In recent months, a sophisticated threat actor leveraging North Korean IT worker employment fraud has surfaced, demonstrating how social engineering…
Chromium-based browsers, including Chrome, Edge, and Brave, manage installed extensions via JSON preference files stored under %AppData%GoogleUser DataDefaultPreferences (for domain-joined machines)…
A man in his forties has been arrested in West Sussex, England, in connection with a cyber-attack that has caused…
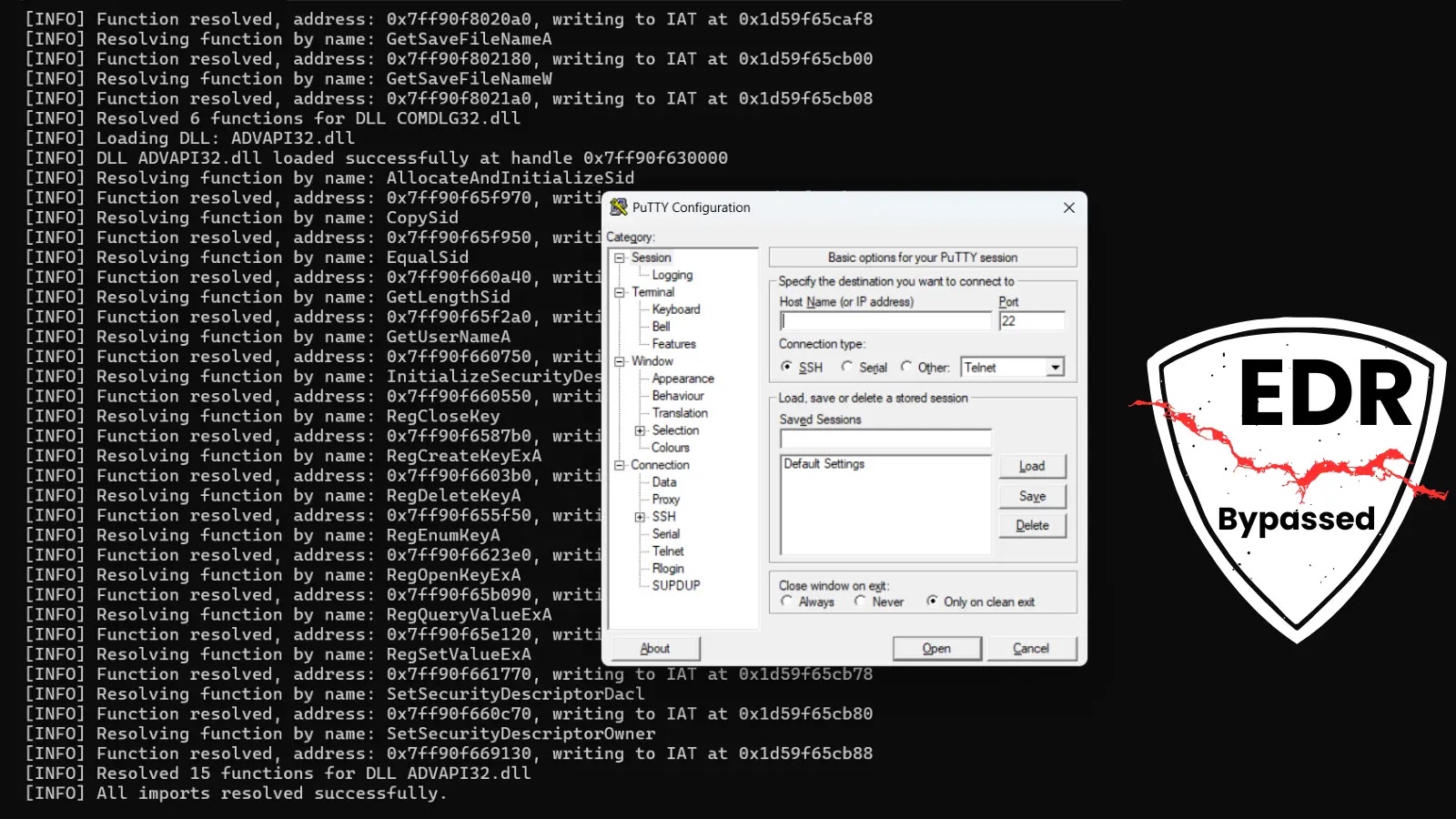
A sophisticated technique that allows attackers to execute malicious code directly in memory is gaining traction, posing a significant challenge…
A severe security vulnerability in OnePlus OxygenOS has been discovered that allows any installed application to read SMS and MMS…
Libraesva has issued an emergency patch for a significant command injection vulnerability in its Email Security Gateway (ESG) after confirming…
A sophisticated cybercrime campaign has emerged that transforms legitimate AWS infrastructure into weaponized attack platforms through an innovative combination of…
A sophisticated new malware family dubbed YiBackdoor has emerged in the cybersecurity landscape, posing a significant threat to organizations worldwide….
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about a high-severity zero-day vulnerability in Google Chrome…
CISA has issued an urgent security Alert in response to a large-scale software supply chain attack on npmjs.com, the world’s…
CISA has released a comprehensive cybersecurity advisory detailing how threat actors successfully compromised a U.S. federal civilian executive branch agency’s…