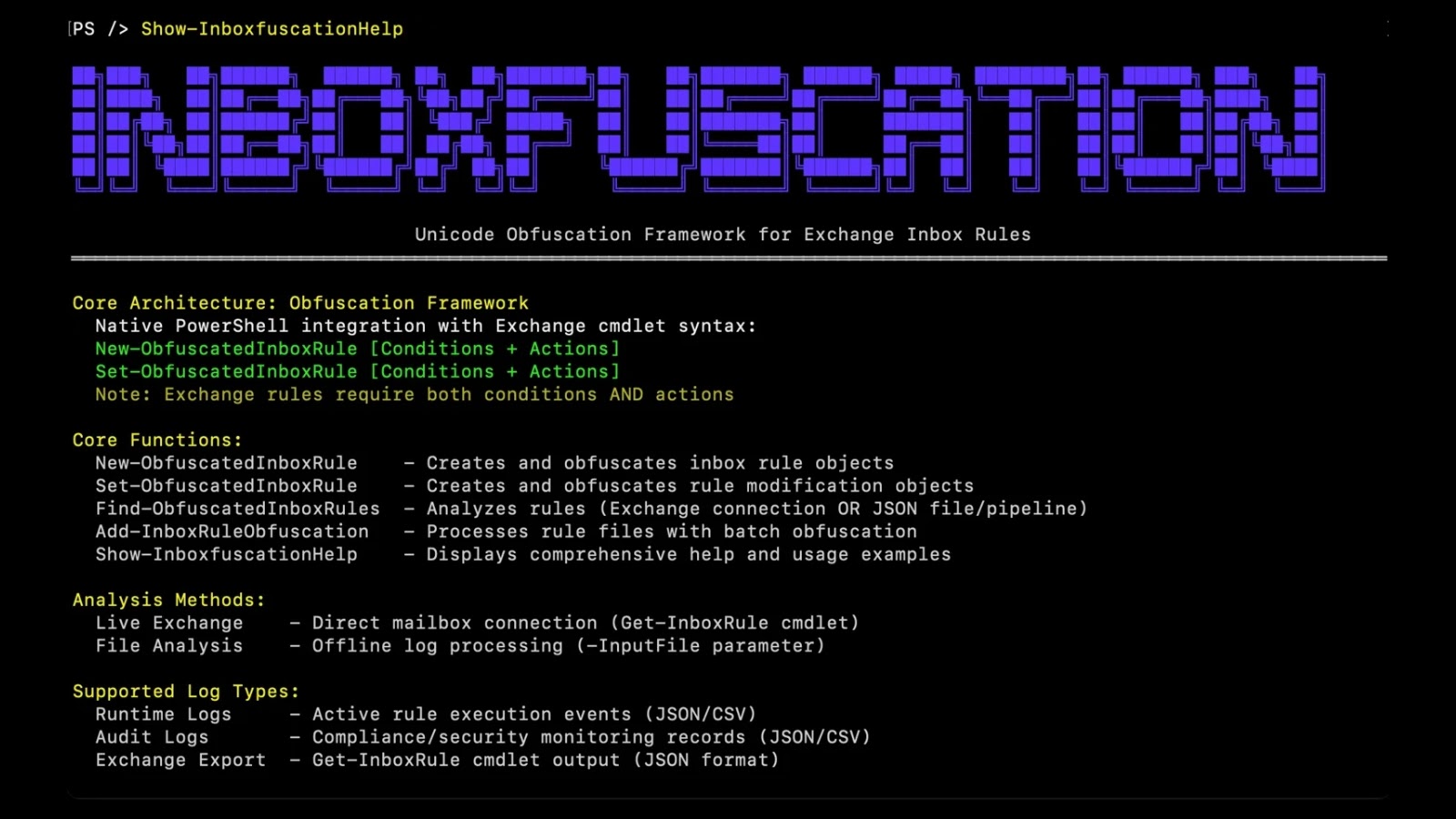
Category: CyberSecurityNews
Attackers increasingly exploit Microsoft Exchange inbox rules to maintain persistence and exfiltrate data within enterprise environments. A newly released tool,…
A sophisticated Iran-nexus espionage group known as Subtle Snail has emerged as a significant threat to European telecommunications, aerospace, and…
A sophisticated new ransomware group has emerged from the shadows, targeting multinational organizations across diverse sectors with precision and systematic…
The cybersecurity landscape faces a growing threat from sophisticated Phishing-as-a-Service (PhaaS) platforms that are democratizing cybercrime by lowering technical barriers…
Three of the cybersecurity industry’s most prominent vendors, Microsoft, SentinelOne, and Palo Alto Networks, have announced they will not participate…
A recent optional update for Windows 11 version 24H2 is causing significant video playback issues for users with certain media…
Automotive giant Stellantis, the parent company of major brands including Citroën, FIAT, Jeep, Chrysler, and Peugeot, has confirmed a data…
Google Chrome’s V8 JavaScript engine has been compromised by a critical type confusion zero-day vulnerability, designated CVE-2025-10585, marking the sixth…
Canada’s law enforcement community has achieved a landmark victory in the fight against illicit finance with the dismantling of TradeOgre,…
A sophisticated spoofing campaign has emerged targeting the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3). Beginning in mid-September…
A previously unseen botnet campaign emerged in late November, using a novel combination of DNS misconfiguration and hijacked networking devices…
A sophisticated attack technique called LNK Stomping has emerged as a critical threat to Windows security, exploiting a fundamental flaw…