Category: CyberSecurityNews
The threat landscape for e-commerce websites has once again shifted with the emergence of a sophisticated Magecart-style attack campaign, characterized…
Since mid-2024, cybercriminals have leveraged a subscription-based phishing platform known as RaccoonO365 to harvest Microsoft 365 credentials at scale. Emerging…
Syteca, a global cybersecurity provider, introduced the latest release of its platform, continuing the mission to help organizations reduce insider…
A sophisticated mobile ad fraud operation dubbed “SlopAds” has infiltrated Google Play Store with 224 malicious applications that collectively amassed…
A decade-old Unicode vulnerability known as BiDi Swap allows attackers to spoof URLs for sophisticated phishing attacks. By exploiting how…
The PureHVNC remote administration tool (RAT) has emerged as a sophisticated component of the Pure malware family, gaining prominence in…
The digital advertising ecosystem has become a prime hunting ground for cybercriminals, who are increasingly exploiting advertising technology companies to…
In recent weeks, cybersecurity researchers have observed the emergence of XillenStealer, a Python-based information stealer publicly hosted on GitHub and…
A critical vulnerability has been discovered in WatchGuard’s Firebox firewalls, which could allow a remote, unauthenticated attacker to execute arbitrary…
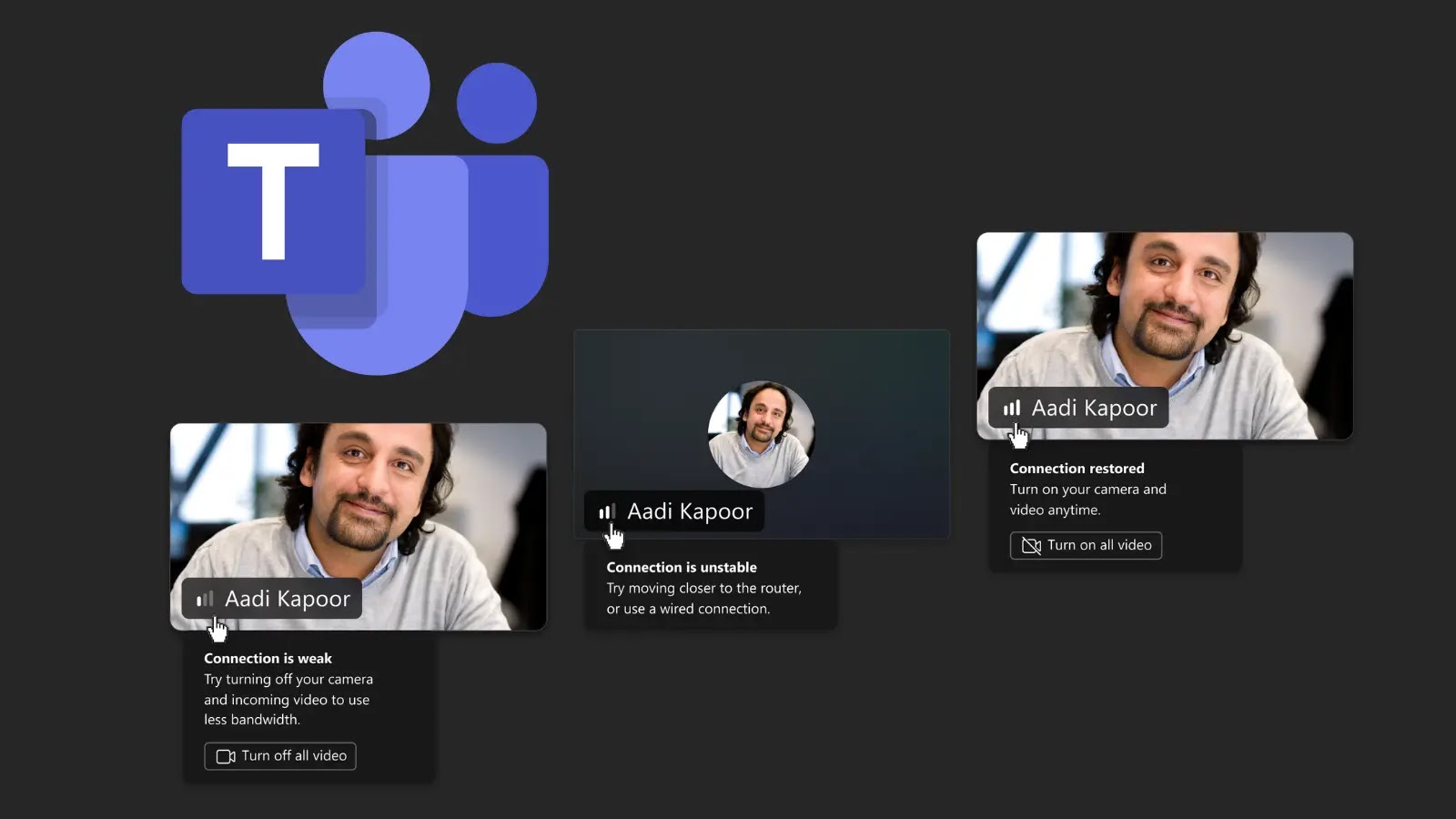
Microsoft is set to roll out a new feature for its Teams platform called the Network Strength Indicator, designed to…
The cybersecurity landscape has witnessed an unprecedented surge in API-focused attacks during the first half of 2025, with threat actors…
A medium-severity vulnerability has been discovered in the official Kubernetes C# client, which could allow an attacker to intercept and…