Category: CyberSecurityNews
DarkCloud Stealer has recently emerged as a potent threat targeting financial organizations through convincing phishing campaigns. Adversaries employ weaponized RAR…
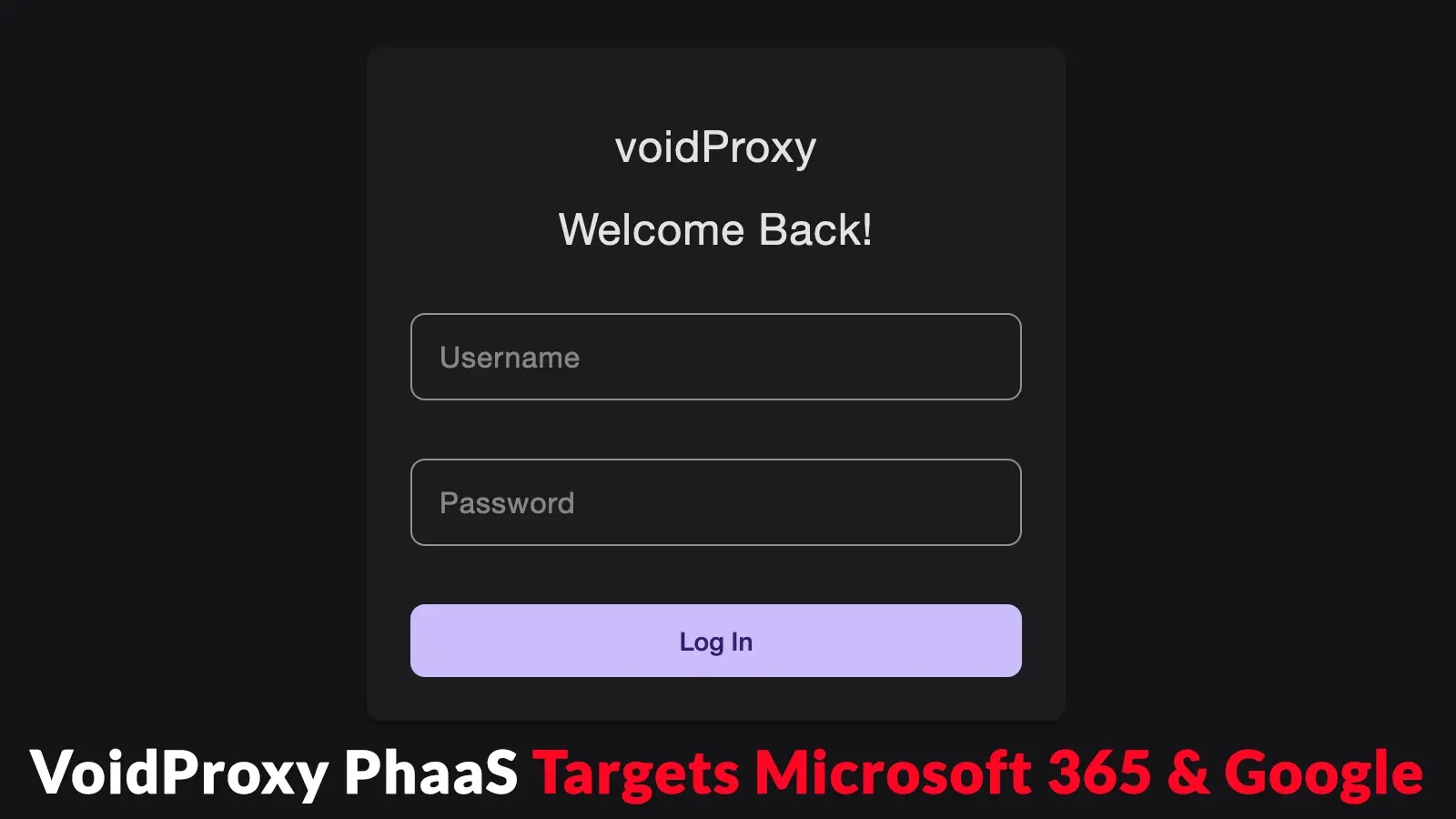
In recent months, security teams have observed a significant increase in sophisticated phishing campaigns leveraging a newly discovered Phishing-as-a-Service (PhaaS)…
Microsoft has issued an official reminder that support for Windows 11 version 23H2 Home and Pro editions is set to…
A critical vulnerability affecting FlowiseAI’s Flowise platform has been disclosed, revealing a severe authentication bypass flaw that allows attackers to…
Two critical vulnerabilities have been discovered in the Linux Common Unix Printing System (CUPS), exposing millions of systems to remote…
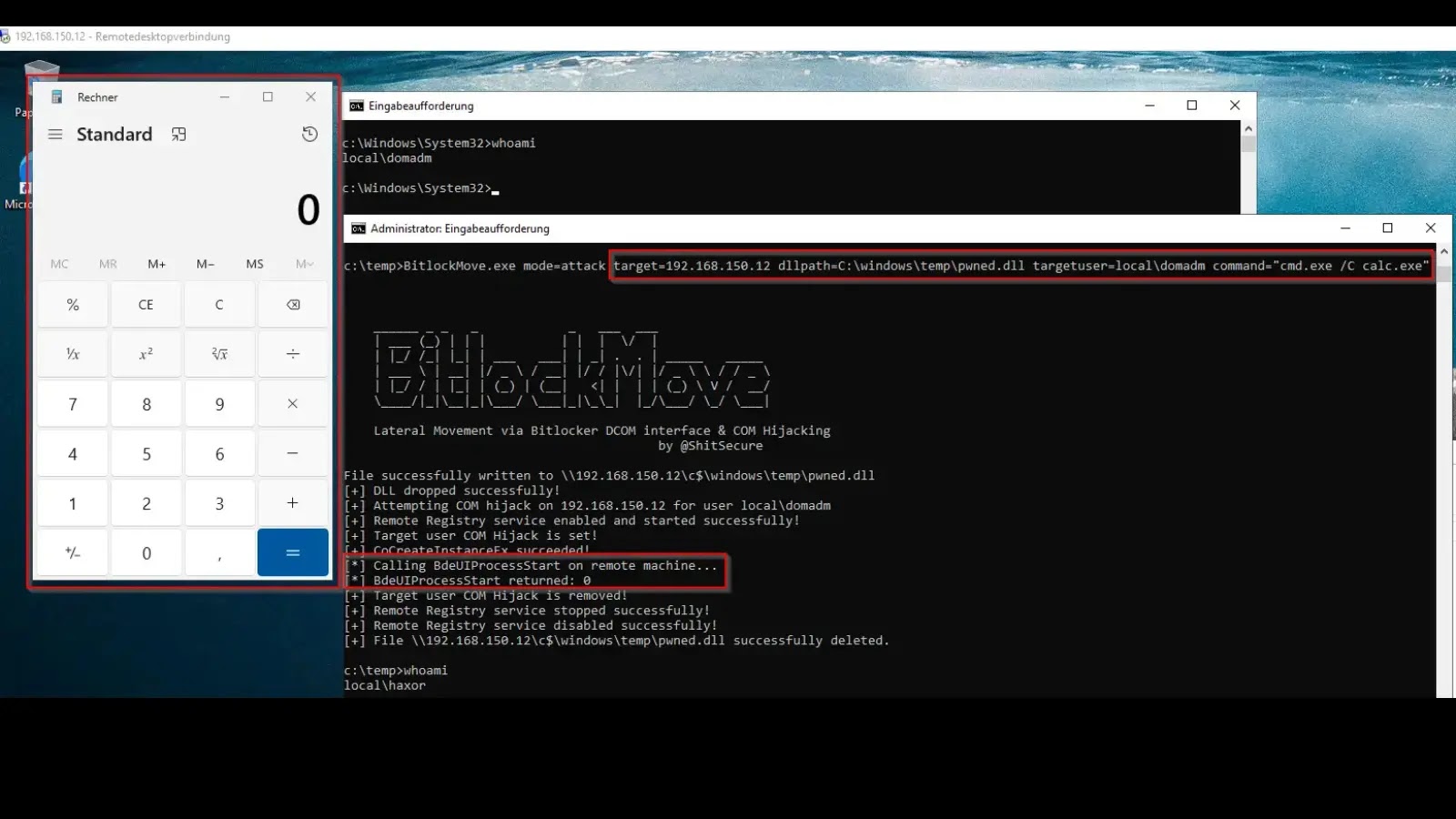
A new proof-of-concept (PoC) tool named BitlockMove demonstrates a novel lateral movement technique that leverages BitLocker’s Distributed Component Object Model…
The Federal Bureau of Investigation (FBI) has released a flash alert detailing the activities of two cybercriminal groups, UNC6040 and…
A sophisticated malvertising campaign has emerged, exploiting GitHub repositories through dangling commits to distribute malware via fake GitHub Desktop clients….
A sophisticated malware campaign has emerged that leverages artificial intelligence to create deceptively legitimate applications, marking a significant evolution in…
A sophisticated backdoor malware known as Backdoor.WIN32.Buterat has emerged as a significant threat to enterprise networks, demonstrating advanced persistence techniques…
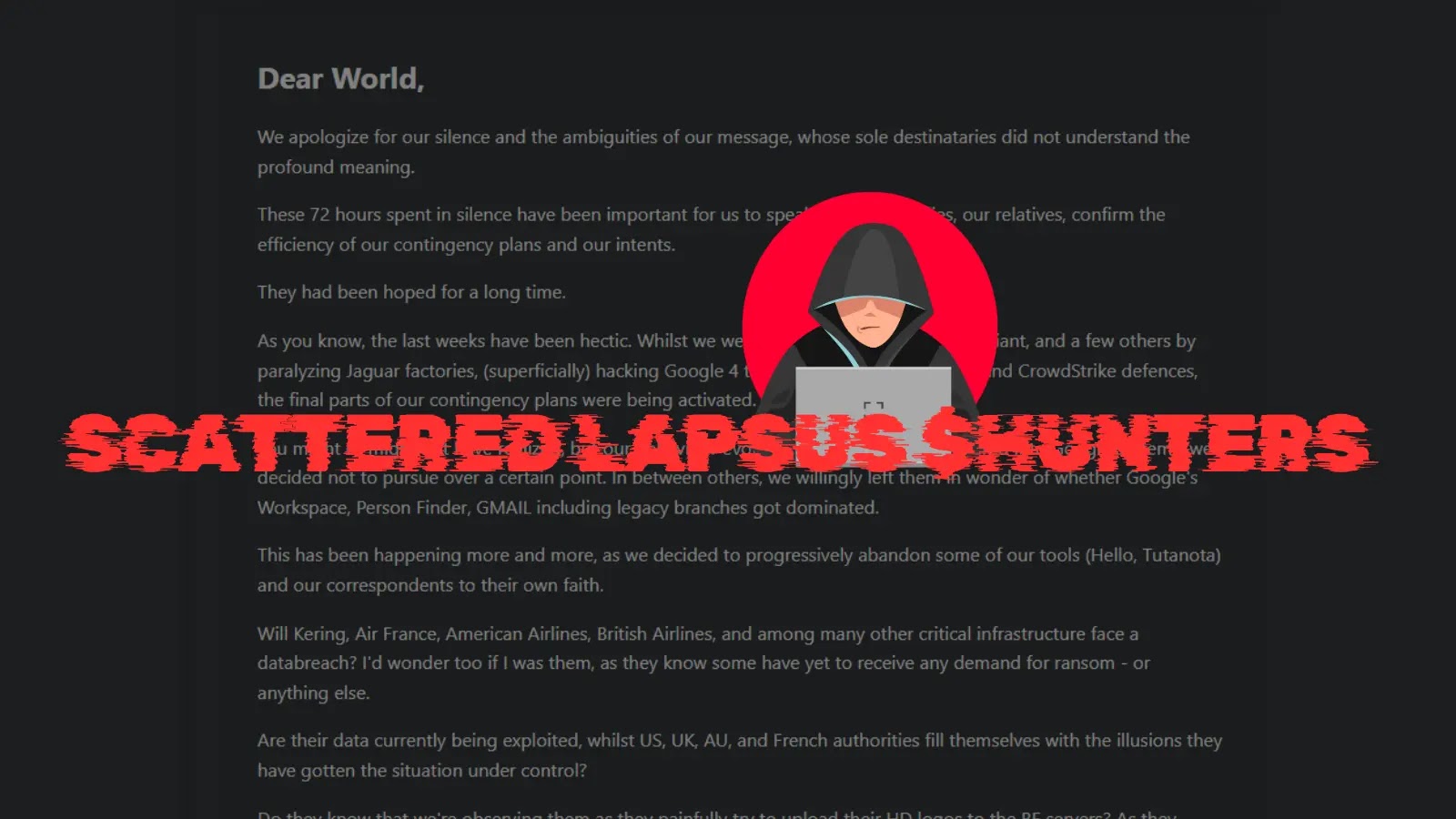
The well-known group of cybercriminals called Scattered Lapsus$ Hunters released a surprising farewell statement on BreachForums. This manifesto, a mix…
Cybersecurity researchers have uncovered a sophisticated malware campaign that exploits SVG (Scalable Vector Graphics) files and email attachments to distribute…