Category: CyberSecurityNews
A newly introduced feature in ChatGPT that allows it to connect with personal data applications can be exploited by attackers…
A sudden and definitive statement emerged from the “Scattered LAPSUS$ Hunters 4.0” Telegram channel on September 8, signaling an abrupt…
New AI-powered penetration testing framework Villager combines Kali Linux toolsets with DeepSeek AI models to fully automate cyber attack workflows….
The notorious APT-C-24 threat actor group, commonly known as Sidewinder or Rattlesnake, has evolved its attack methodology by deploying sophisticated…
Since its first appearance earlier this year, the ToneShell backdoor has demonstrated a remarkable capacity for adaptation, toyed with by…
Samsung has released its September 2025 security update, addressing a critical zero-day vulnerability that is being actively exploited in the…
Within mere hours of its public unveiling, the K2 Think model experienced a critical compromise that has sent ripples throughout…
In late July 2025, a series of ransomware samples surfaced on VirusTotal under filenames referencing the notorious Petya and NotPetya…
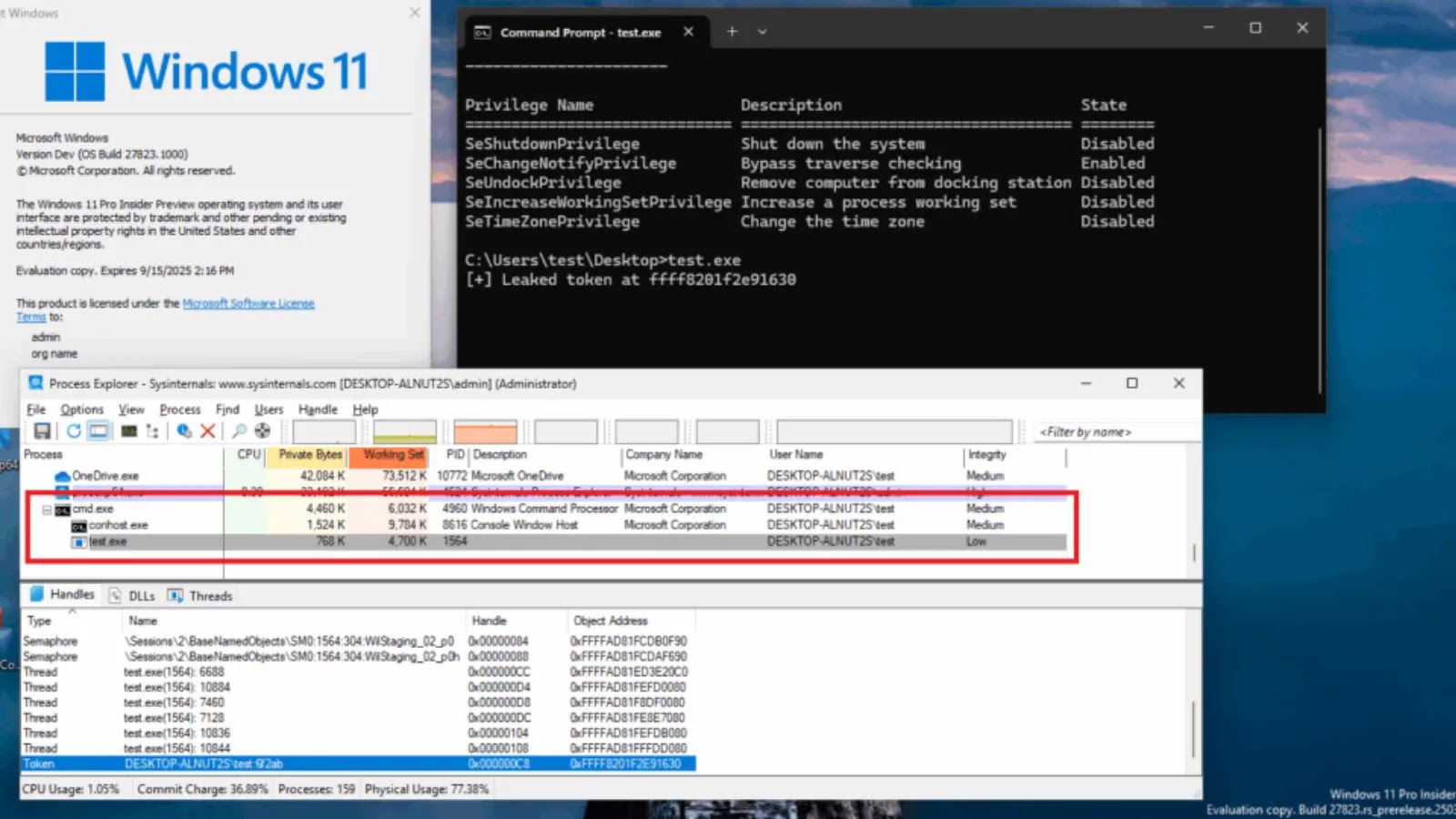
A new kernel address leak vulnerability has been discovered in the latest versions of Windows 11 (24H2) and Windows Server…
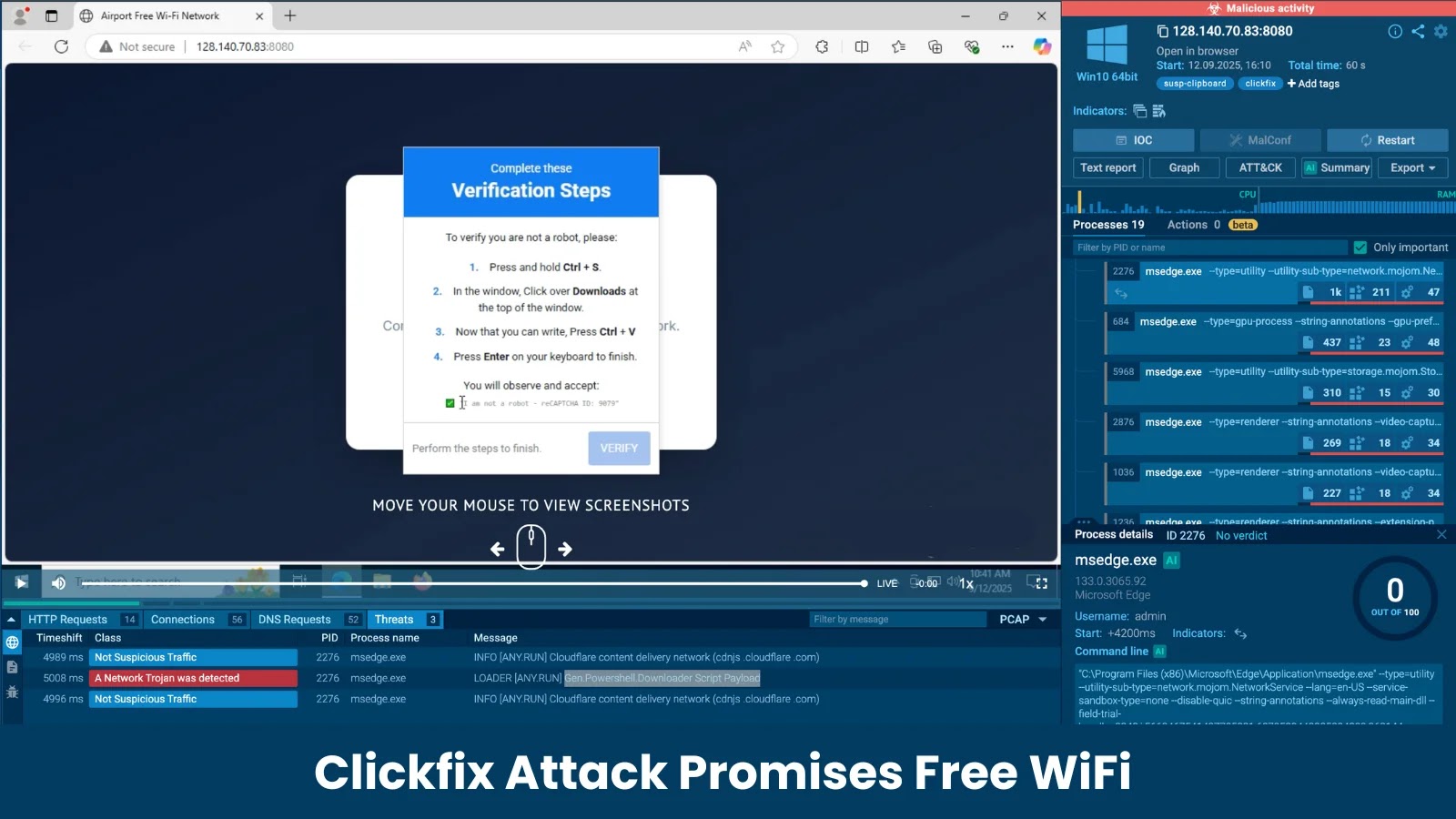
The Cybersecuritynews researcher team uncovered a sophisticated social engineering campaign that is exploiting the public’s need for free internet access,…
A new, sophisticated malware campaign has been uncovered that leverages Microsoft’s Azure Functions for its command-and-control (C2) infrastructure, a novel…
Microsoft has addressed four elevation of privilege vulnerabilities in its Windows Defender Firewall service, all rated as “Important” in severity….