Category: CyberSecurityNews
Microsoft is investigating a significant Exchange Online service disruption that is preventing users in North and South America from accessing…
Microsoft to enhance security for its Teams platform by automatically warning users about malicious links in chat messages. The new…
To ensure the security of sensitive internet data, it takes more than encryption; it requires clear principles, careful design, and…
In early May 2025, cybersecurity researchers began tracking a novel Remote Access Trojan (RAT) targeting Chinese-speaking users via phishing sites…
Four Kenyan filmmakers became victims of sophisticated surveillance when FlexiSPY spyware was covertly installed on their devices while in police…
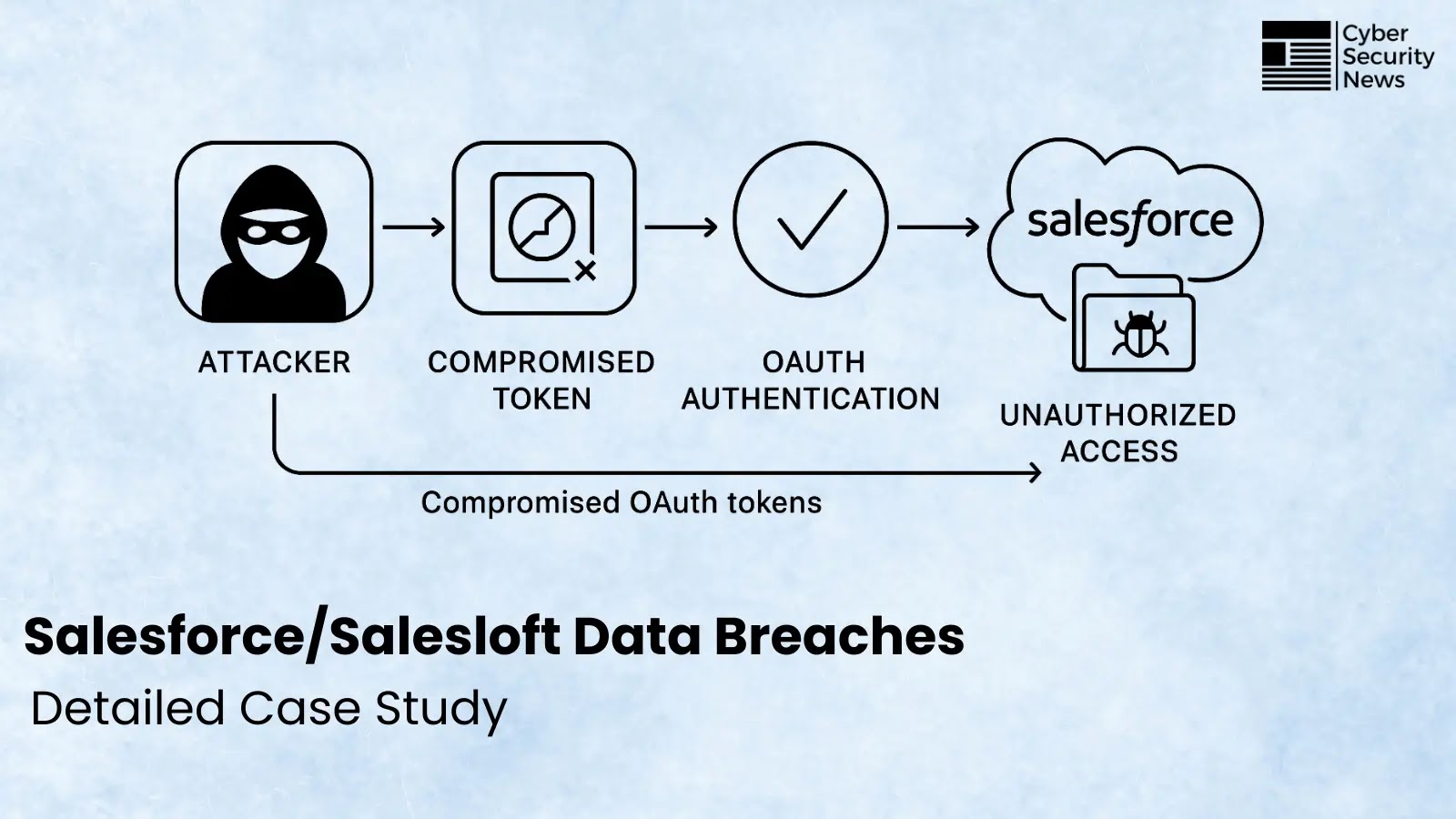
The Salesloft Drift data breaches of August 2025 stand as one of the most significant supply chain attacks in SaaS…
A novel speculative execution attack named VMSCAPE allows a malicious virtual machine (VM) to breach its security boundaries and steal…
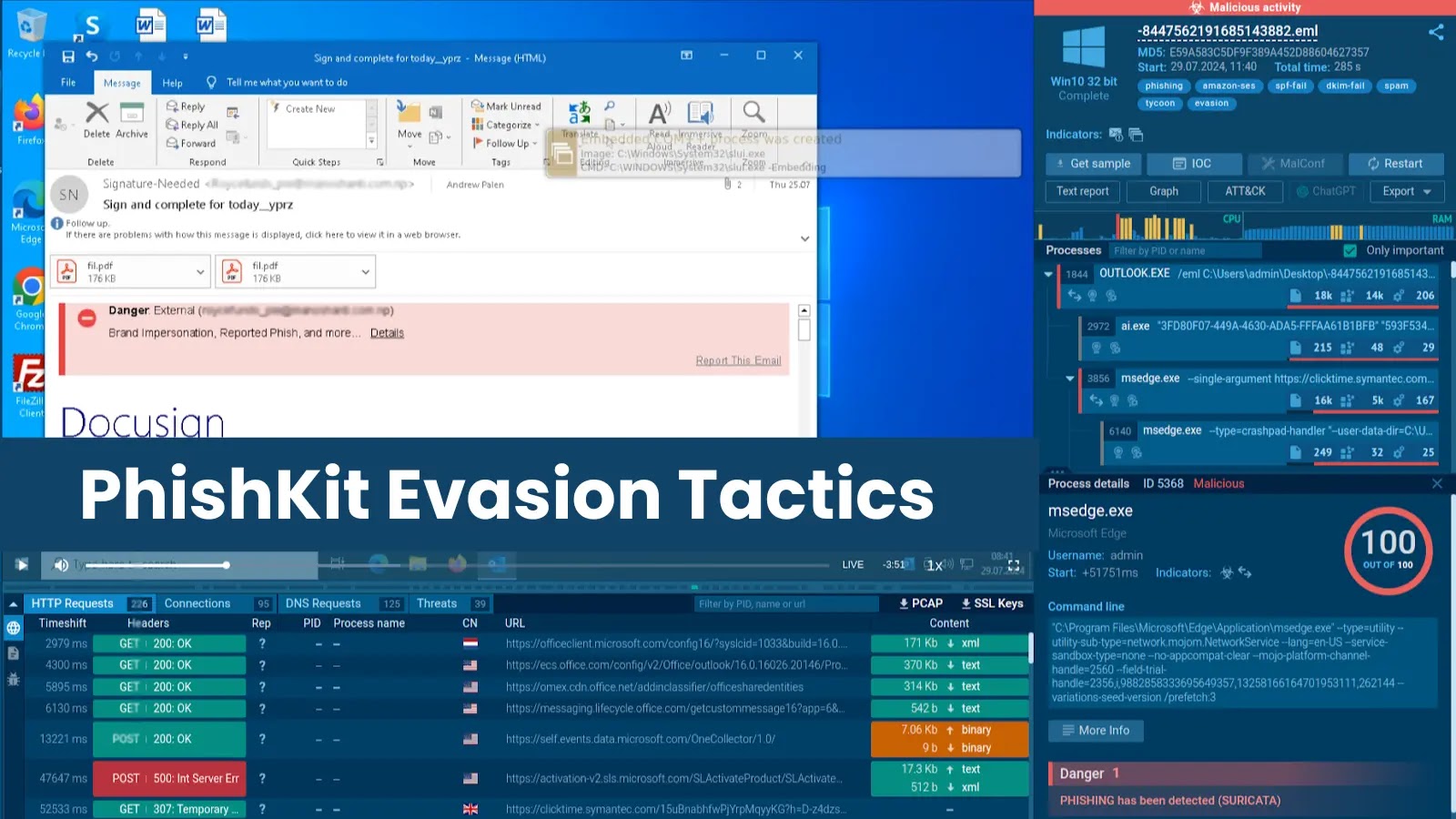
Cyber attackers constantly refine their evasion methods. That’s what makes threats, including phishing, increasingly hard to detect and investigate. Kits…
In early May 2025, security teams began observing a sudden rise in post-exploitation activity leveraging an open-source command-and-control framework known…
In early March 2025, security teams first observed an unprecedented L7 DDoS botnet targeting web applications across multiple sectors. The…
A previously unknown advanced persistent threat (APT) group has unleashed a new fileless malware framework, dubbed EggStreme, in a highly…
Cornwell Quality Tools has disclosed a significant data breach that compromised the sensitive information of nearly 104,000 individuals. The incident…