Category: CyberSecurityNews
HackerOne has confirmed it was among the companies affected by a recent data breach that provided unauthorized access to its…
Microsoft has released patches for two significant vulnerabilities in Microsoft Office that could allow attackers to execute malicious code on…
Sophos has resolved an authentication bypass vulnerability in its AP6 Series Wireless Access Points that could allow attackers to gain…
A critical vulnerability CVE-2025-42922 has been discovered in SAP NetWeaver that allows an authenticated, low-privileged attacker to execute arbitrary code…
Microsoft has addressed two significant elevation of privilege vulnerabilities affecting its Windows BitLocker encryption feature. The flaws, tracked as CVE-2025-54911…
Workday has confirmed it suffered a data breach after a security incident involving a third-party application that compromised customer information….
Google has issued an urgent security update for the Chrome browser on Windows, Mac, and Linux, addressing a critical vulnerability…
Cybersecurity researchers have observed the emergence of a novel Android banking trojan, RatOn in recent months that seamlessly combines remote…
A widespread issue with Microsoft’s anti-spam filtering service is preventing some Exchange Online and Microsoft Teams users from opening URLs,…
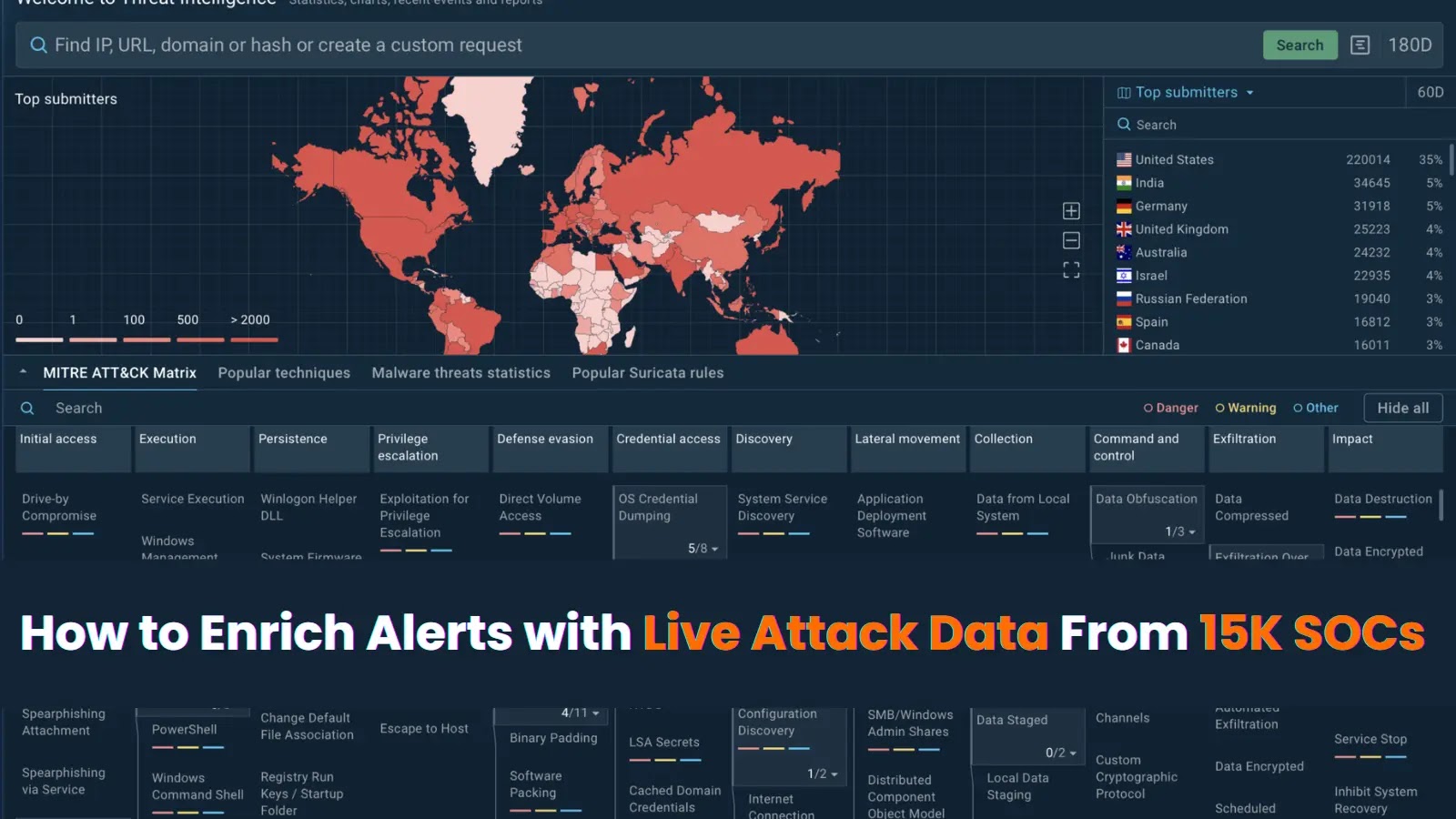
Every SOC analyst knows the frustration. Your SIEM generates hundreds, sometimes thousands of alerts daily. Each alert demands attention, but…
Ivanti has released security updates to address two high-severity vulnerabilities in its Endpoint Manager (EPM) software that could allow remote…
A new wave of phishing attacks purporting to originate from South Korea’s National Tax Service has emerged, leveraging familiar electronic…