Category: CyberSecurityNews
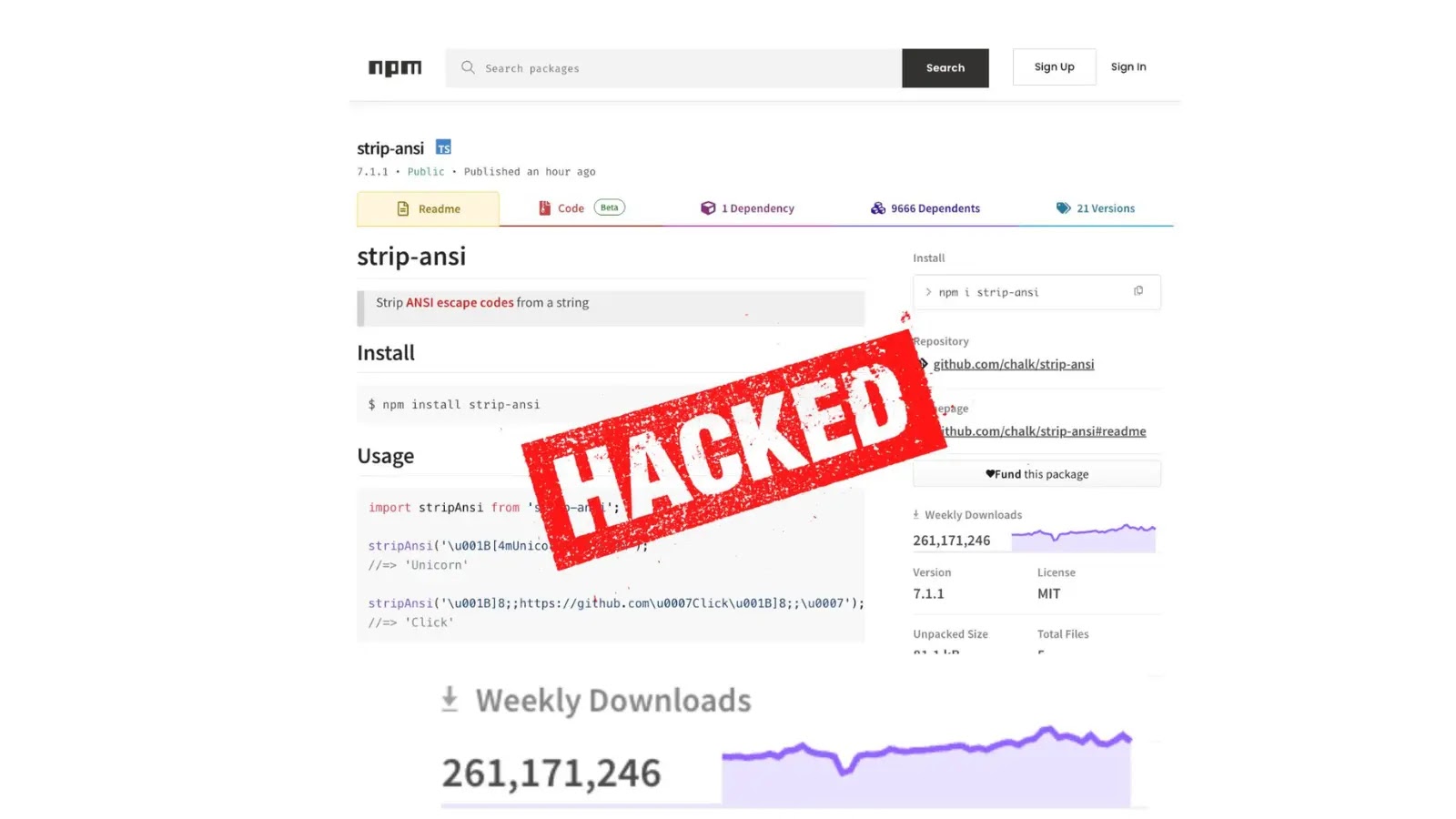
In the largest supply chain attack, hackers compromised 18 popular npm packages, which together account for over two billion downloads…
A significant security flaw has been discovered in pgAdmin, the widely used open-source administration and development platform for PostgreSQL databases….
A severe vulnerability in Windows Defender’s update process allows attackers with administrator privileges to disable the security service and manipulate…
A critical security vulnerability has been discovered in Progress OpenEdge, a platform for developing and deploying business applications. The flaw,…
Qualys has confirmed it was impacted by a widespread supply chain attack that targeted the Salesloft Drift marketing platform, resulting…
A massive data breach in early September 2025 attributed to a cyber actor known simply as “Kim” laid bare an…
In Caracas this week, President Nicolás Maduro unveiled the Huawei Mate X6 gifted by China’s Xi Jinping, declaring the device…
Security researchers first observed LunaLock in early September 2025, a sophisticated ransomware strain targeting independent illustrators and digital artists. Leveraging…
A sophisticated cybercriminal campaign has emerged, exploiting Amazon’s Simple Email Service (SES) to orchestrate large-scale phishing operations capable of delivering…
A sophisticated cybercriminal campaign has emerged, exploiting Amazon’s Simple Email Service (SES) to orchestrate large-scale phishing operations capable of delivering…
Cybersecurity researchers have demonstrated a sophisticated technique for bypassing Web Application Firewalls (WAFs) using JavaScript injection combined with HTTP parameter…
A proof-of-concept (PoC) exploit has been released for a critical remote code execution (RCE) vulnerability in ImageMagick 7’s MagickCore subsystem, specifically affecting…