Category: CyberSecurityNews
A new cyber-attack, dubbed “Grokking,” is exploiting features on the social media platform X to spread malicious links on a…
Microsoft has officially acknowledged a significant bug in recent Windows security updates that is causing application installation and repair failures…
A significant outage of Google services, including its search engine, Gmail, and YouTube, has affected users across Turkey and several…
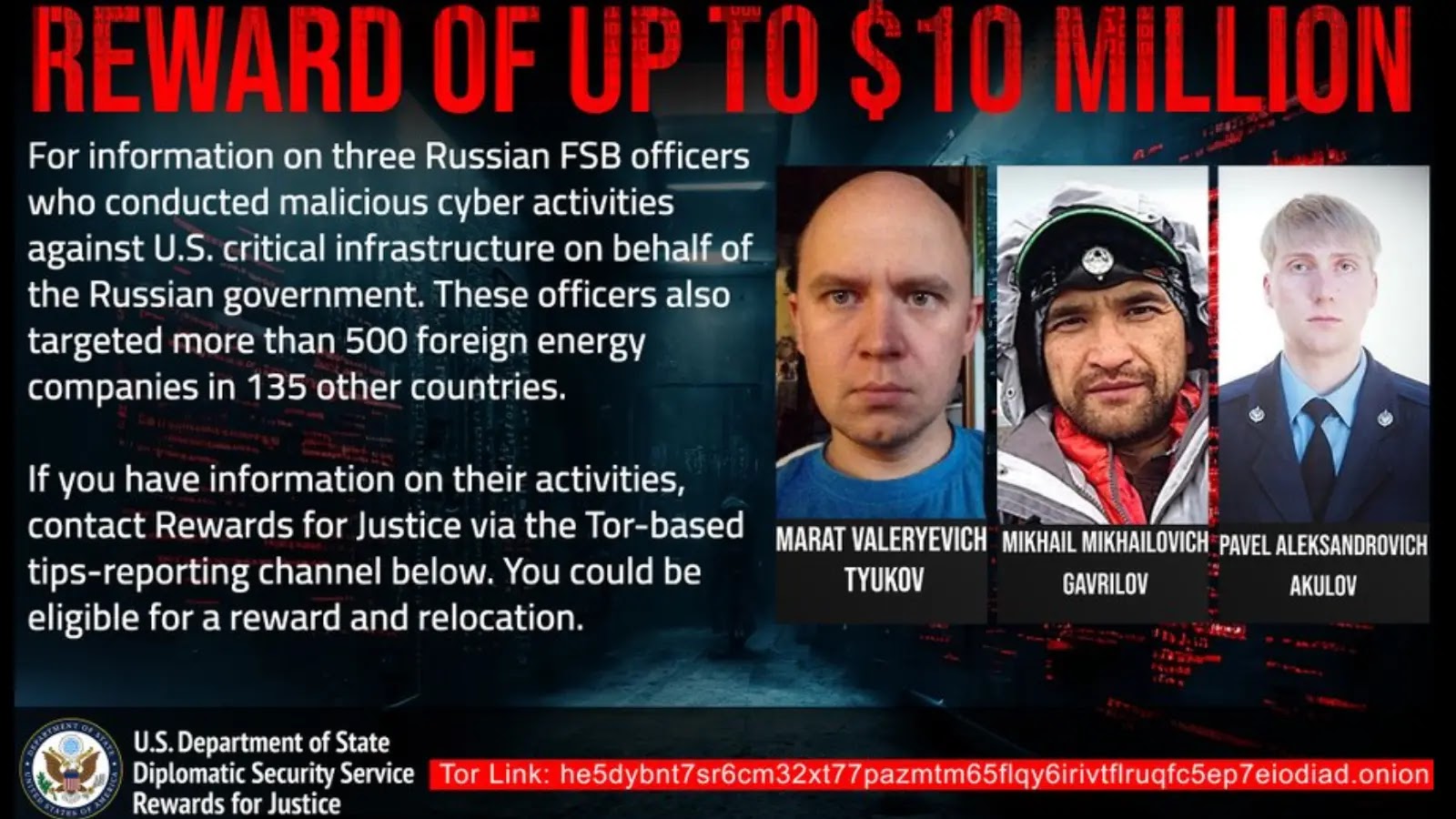
The United States government has announced a reward of up to $10 million for information leading to the identification or…
Emerging quietly in mid-2025, the XWorm backdoor has evolved into a deceptively sophisticated threat that preys on both user confidence…
A sprawling network of illicit Internet Protocol Television (IPTV) services has been discovered, operating across more than 1,100 domains and…
Over the past several years, a concerted campaign by Chinese state-sponsored Advanced Persistent Threat (APT) groups has exploited critical vulnerabilities…
A sophisticated phishing campaign targeting PayPal’s massive user base has emerged, utilizing deceptive “Set up your account profile” emails to…
Cybersecurity researchers have uncovered a critical vulnerability in the artificial intelligence supply chain that enables attackers to achieve remote code…
A comprehensive security investigation has uncovered a disturbing reality in the artificial intelligence infrastructure landscape: more than 1,100 instances of…
The U.S. District Court for the District of Columbia has ordered Google to share critical search data with competitors while…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory warning about a critical vulnerability in SunPower PVS6…