Category: CyberSecurityNews
AI-powered cybersecurity tools can be turned against themselves through prompt injection attacks, allowing adversaries to hijack automated agents and gain…
Cloudflare has confirmed a data breach where a sophisticated threat actor accessed and stole customer data from the company’s Salesforce…
A sophisticated spear-phishing campaign has emerged targeting senior executives and C-suite personnel across multiple industries, leveraging Microsoft OneDrive as the…
A critical security vulnerability discovered in ESPHome’s web server component has exposed thousands of smart home devices to unauthorized access,…
Google has officially debunked widespread reports claiming the company issued a major security warning to Gmail users, clarifying that such…
A sophisticated spear-phishing campaign orchestrated by Iranian-aligned operators has been identified targeting diplomatic missions worldwide through a compromised Ministry of…
Commercial surveillance vendors have evolved from niche technology suppliers into a sophisticated multi-billion-dollar ecosystem that poses unprecedented threats to journalists,…
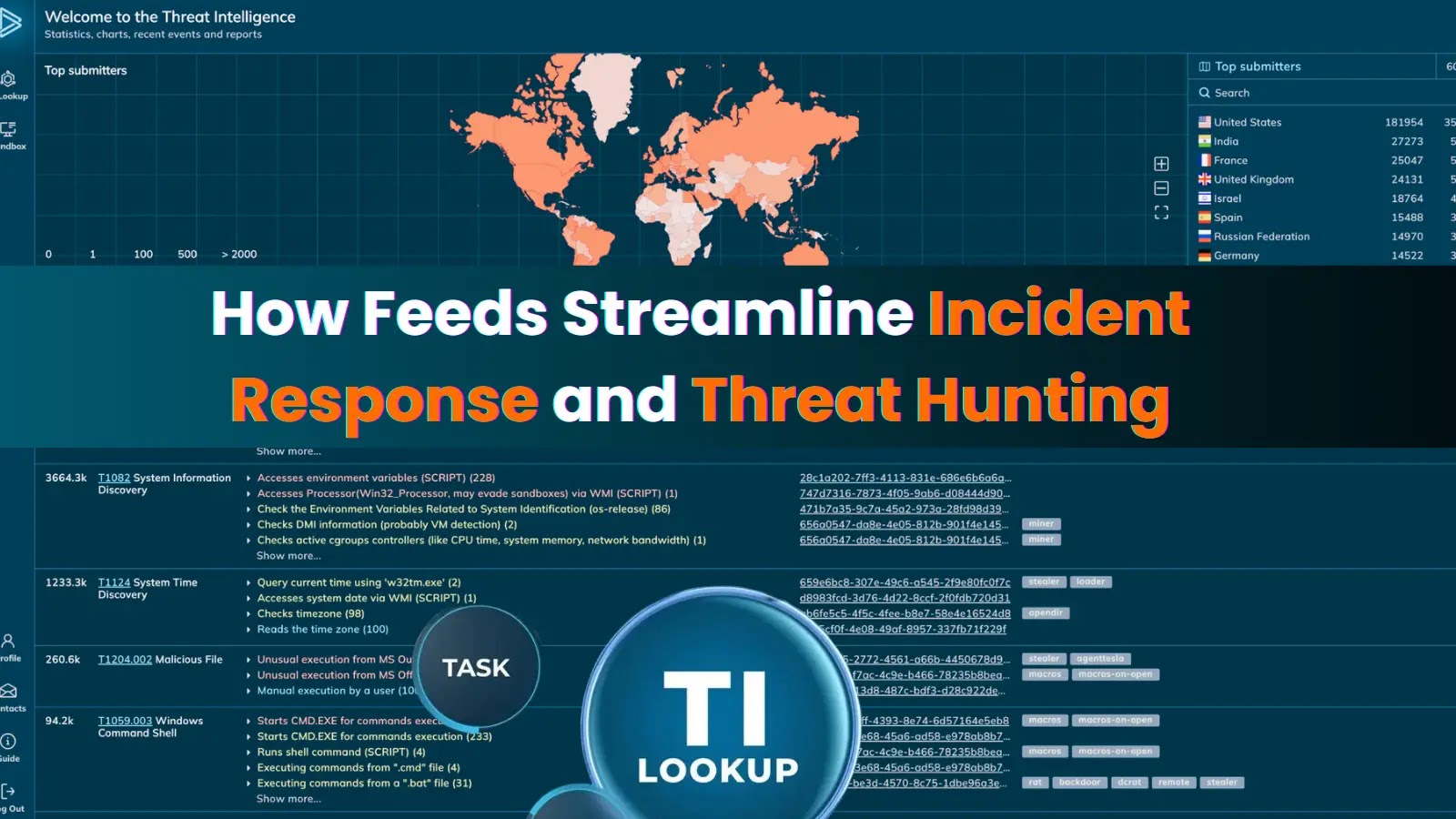
When you’re in a SOC, speed is everything. The earlier you detect and confirm an intrusion, the faster you can…
A sophisticated network of Ukrainian-based autonomous systems has emerged as a significant cybersecurity threat, orchestrating large-scale brute-force and password-spraying attacks…
A newly discovered WhatsApp scam has begun circulating on messaging platforms, exploiting the popular device linking feature to seize full…
Luxury automaker Jaguar Land Rover (JLR) has been forced to halt production at its Halewood plant and shut down its…
Palo Alto Networks has confirmed that it was affected by a supply chain attack, resulting in the theft of customer…