Category: CyberSecurityNews
A high-severity Server-Side Request Forgery (SSRF) vulnerability has been identified in the widely used PhpSpreadsheet library, potentially allowing attackers to…
Adversary-in-the-Middle (AiTM) attacks are among the most sophisticated and dangerous phishing techniques in the modern cybersecurity landscape. Unlike traditional phishing…
A sophisticated new Mac malware campaign has emerged, targeting users through a deceptive PDF conversion website that conceals a dangerous…
A sophisticated supply chain attack has compromised the popular Nx build platform, affecting millions of weekly downloads and resulting in…
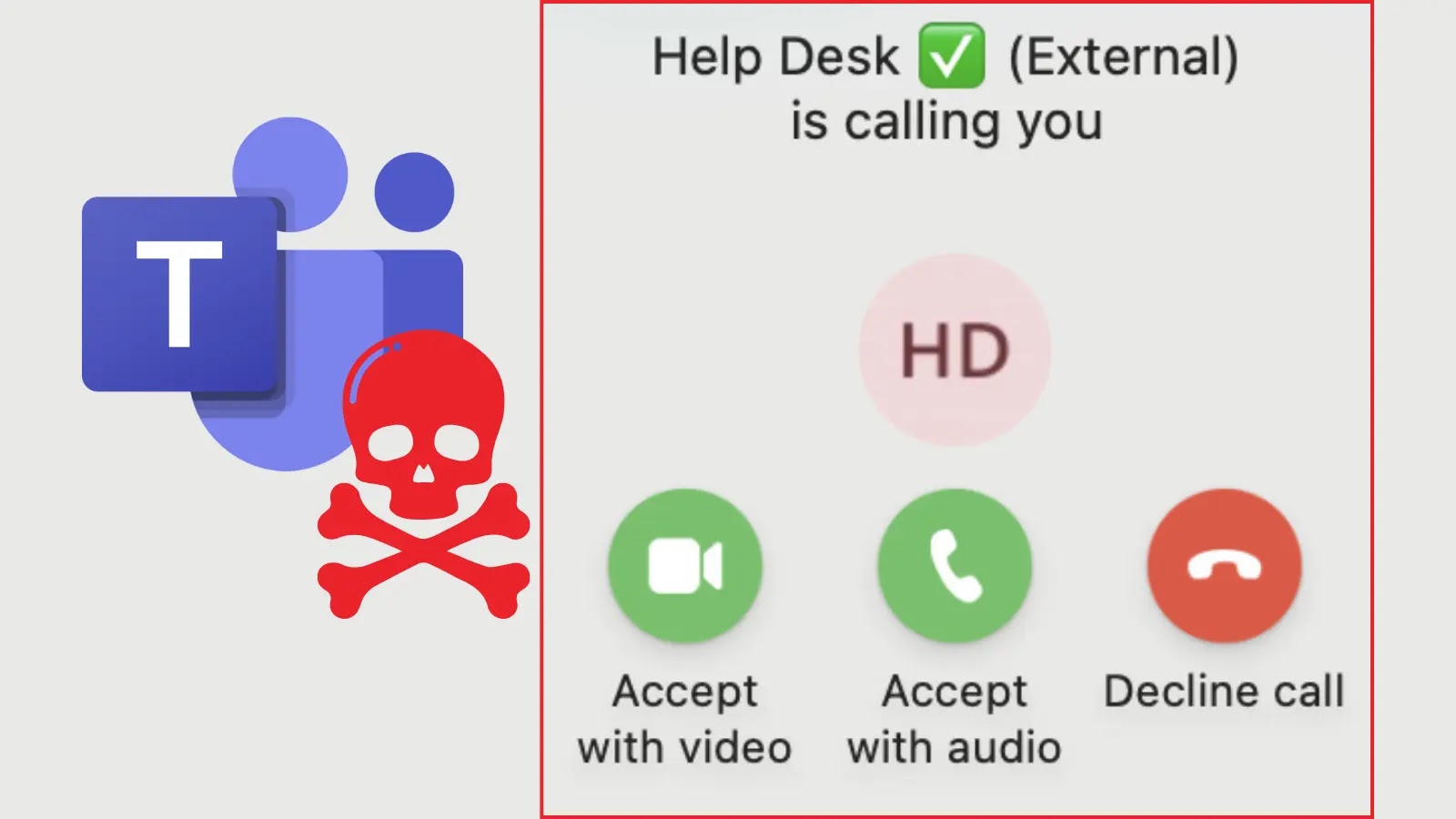
A sophisticated phishing campaign has been identified, where threat actors impersonate IT helpdesk personnel through Teams’ external communication features, exploiting…
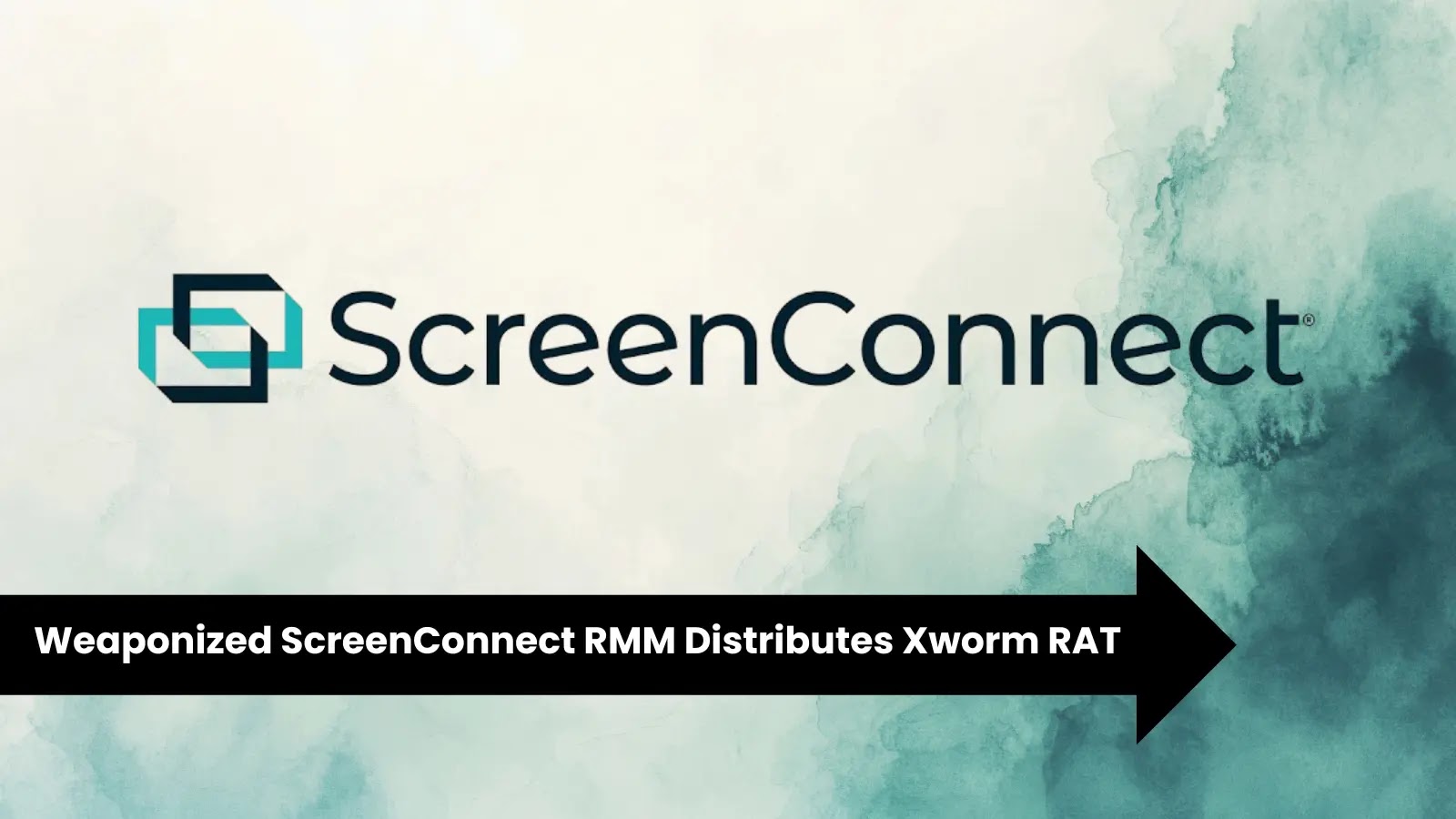
In a sophisticated campaign uncovered during a recent Advanced Continual Threat Hunt (ACTH) by Trustwave’s SpiderLabs team, threat actors weaponized…
The emergence of sophisticated cybercriminal organizations continues to pose significant threats to individuals and institutions worldwide, with the UTG-Q-1000 group…
Anthropic has thwarted multiple sophisticated attempts by cybercriminals to misuse its Claude AI platform, according to a newly released Threat…
Farmers Insurance Exchange and its subsidiaries recently disclosed a significant security incident that compromised personal information of approximately 1.1 million…
South Korean authorities have successfully extradited a Chinese national suspected of orchestrating one of the most sophisticated hacking operations targeting…
Cisco has issued a High-severity security advisory alerting customers to a critical vulnerability in the Intermediate System-to-Intermediate System (IS-IS) feature…
A significant cyberattack disrupted Nevada’s state government network on August 24, forcing all state office branches to shut down operations…