Category: CyberSecurityNews
A newly disclosed vulnerability in the widely used ISC Kea DHCP server poses a significant security risk to network infrastructure…
Microsoft Threat Intelligence has released a detailed report exposing a significant evolution in ransomware attacks, pioneered by the financially motivated…
CISA has issued an urgent warning regarding a critical zero-day vulnerability affecting Citrix NetScaler systems, designated as CVE-2025-7775. This memory…
A sophisticated malware campaign has emerged, targeting Indonesia’s most vulnerable digital citizens through a calculated exploitation of trust in the…
Over the past year, the Underground ransomware gang has emerged as a formidable threat to organizations across diverse industries and…
A widespread service issue is impacting Microsoft Teams users globally this Thursday, preventing many from opening embedded Microsoft Office documents…
A sophisticated global cybercrime campaign dubbed “ShadowCaptcha” has emerged as a significant threat to organizations worldwide, leveraging fake Google and…
Apple has issued emergency security updates across its entire ecosystem to address CVE-2025-43300, a critical zero-day vulnerability in the ImageIO framework that…
NVIDIA has issued a critical security bulletin addressing a high-severity vulnerability in its NeMo Curator platform that could allow attackers…
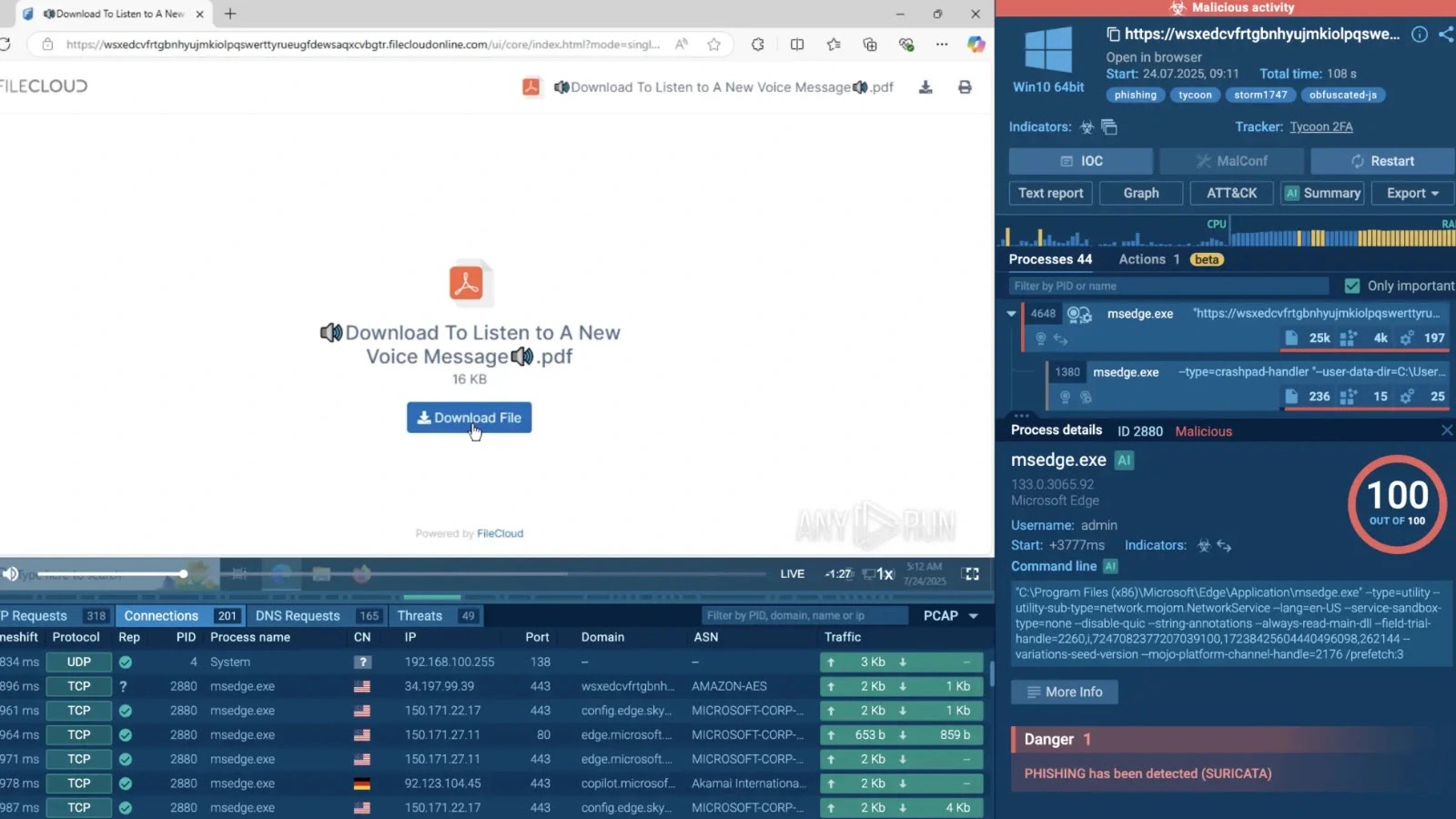
August 2025 has marked a significant evolution in cybercrime tactics, with threat actors deploying increasingly sophisticated phishing frameworks and social…
A critical zero-day remote code execution (RCE) vulnerability, tracked as CVE-2025-7775, is affecting over 28,000 Citrix instances worldwide. The flaw…
A weaponized proof-of-concept exploit has been publicly released targeting CVE-2025-54309, a severe authentication bypass vulnerability affecting CrushFTP file transfer servers. …