Category: CyberSecurityNews
A stored cross-site scripting (XSS) flaw identified in IPFire 2.29’s web-based firewall interface (firewall.cgi). Tracked as CVE-2025-50975, the vulnerability allows…
CISA released three significant Industrial Control Systems (ICS) advisories on August 26, 2025, alerting organizations to critical vulnerabilities affecting widely-deployed…
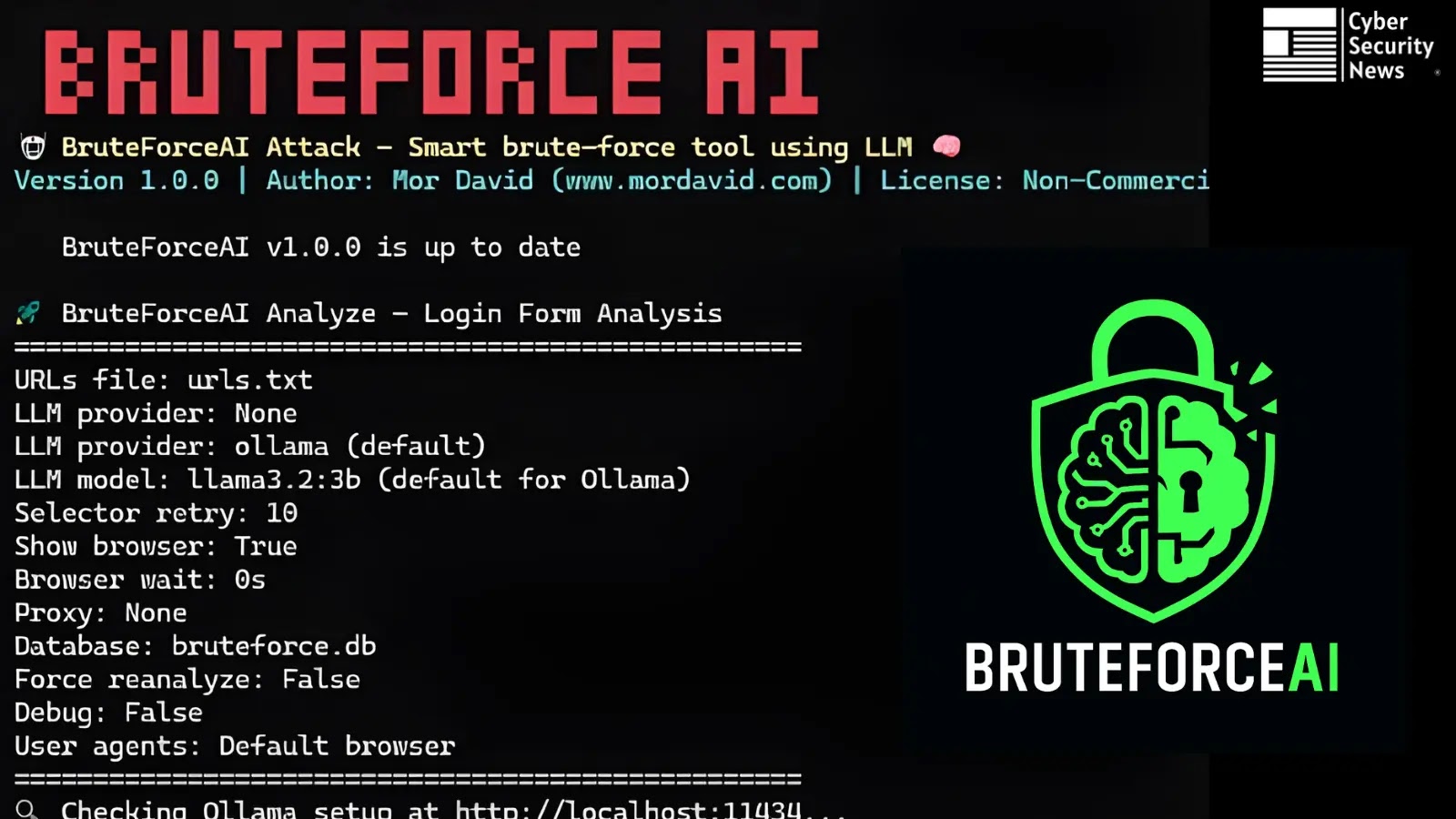
BruteForceAI, an innovative penetration testing framework developed by Mor David, integrates large language models (LLMs) with browser automation to autonomously…
A newly observed variant of the Zip Slip vulnerability has emerged, enabling threat actors to exploit path traversal flaws in…
Spotify today rolled out a native direct messaging feature, Messages, for both Free and Premium users aged 16+ in select…
In recent weeks, a sophisticated phishing operation known as the ZipLine campaign has targeted U.S.-based manufacturing firms, leveraging supply-chain criticality…
A whistleblower disclosure filed today alleges that the Department of Government Efficiency (DOGE) within the Social Security Administration (SSA) covertly…
A newly identified ransomware strain named Cephalus has emerged as a sophisticated threat, targeting organizations through compromised Remote Desktop Protocol…
Google has released an emergency security update for Chrome to address a critical use-after-free vulnerability (CVE-2025-9478) in the ANGLE graphics…
A sophisticated data exfiltration campaign targeting corporate Salesforce instances has exposed sensitive information from multiple organizations through compromised OAuth tokens…
A sophisticated new variant of the Hook Android banking trojan has emerged with unprecedented capabilities that position it among the…
China-based threat actor Mustang Panda has emerged as one of the most sophisticated cyber espionage groups operating in the current…