Category: CyberSecurityNews
In August 2025, researchers at George Mason University published a groundbreaking study at the 34th USENIX Security Symposium, introducing OneFlip,…
The cybersecurity landscape has been significantly impacted by the discovery and active exploitation of two critical zero-day vulnerabilities in WinRAR,…
Google has disclosed a critical zero-day vulnerability in the V8 JavaScript engine used by Chrome, tracked as CVE-2025-5419. Before a…
Major French retail chain Auchan announced on August 21, 2025, that it suffered a significant cybersecurity incident resulting in the…
A comprehensive analysis of the top 10 social media platforms reveals that X (formerly Twitter) stands out as the most…
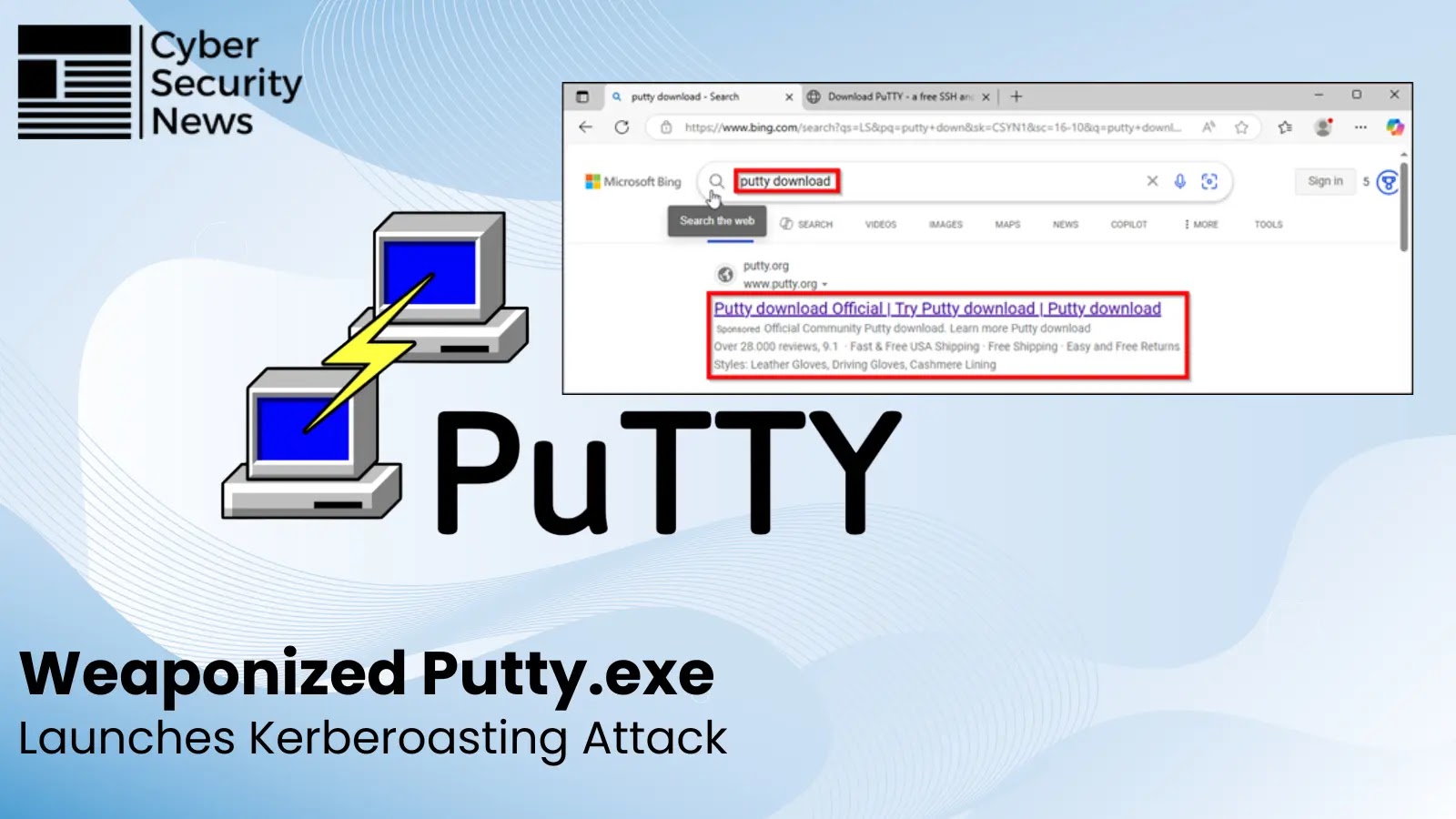
A malvertising campaign using sponsored results on Microsoft’s search platform delivered a weaponized PuTTY that established persistence, enabled hands-on keyboard…
Android droppers have evolved from niche installers for heavyweight banking Trojans into universal delivery frameworks, capable of deploying even rudimentary…
A stealthy espionage campaign emerged in early 2025 targeting diplomats and government entities in Southeast Asia and beyond. At the…
A massive coordinated scanning campaign targeting Microsoft Remote Desktop Protocol (RDP) services, with threat actors deploying over 30,000 unique IP…
A critical security vulnerability has been discovered in Zendesk’s Android SDK implementation that allows attackers to perform mass account takeovers…
A novel adaptation of the ClickFix social engineering technique has been identified, leveraging invisible prompt injection to weaponize AI summarization…
A sophisticated Android malware campaign has resurfaced, exploiting deceptive websites that perfectly mimic legitimate Google Play Store application pages to…