Category: CyberSecurityNews
CISA issued four comprehensive Industrial Control Systems (ICS) advisories on August 19, 2025, highlighting serious vulnerabilities affecting critical infrastructure sectors…
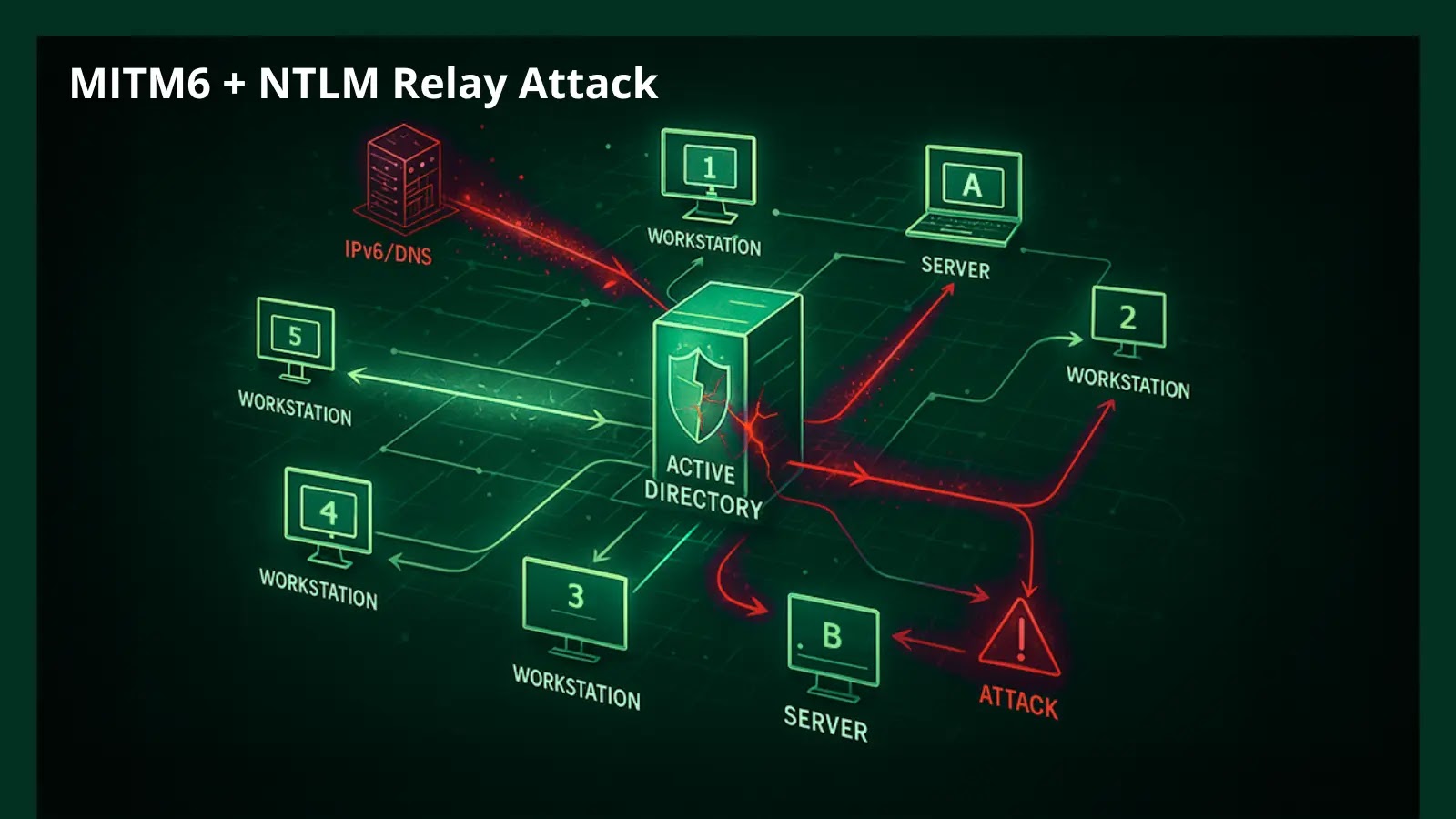
A sophisticated attack chain that combines MITM6 with NTLM relay techniques to achieve full Active Directory domain compromise. The attack…
A critical security vulnerability has been discovered in Microsoft’s VS Code Remote-SSH extension that allows attackers to execute malicious code…
A Russian state-sponsored cyber espionage group designated as Static Tundra has been actively exploiting a seven-year-old vulnerability in Cisco networking…
A critical security vulnerability has been discovered in Apache Tika’s PDF parser module that could enable attackers to access sensitive…
Google Cloud has unveiled a comprehensive suite of security enhancements at its Security Summit 2025, marking a significant evolution in…
A sophisticated new malware loader called QuirkyLoader has emerged as a significant cybersecurity threat, actively distributing well-known infostealers and remote…
Japan experienced a significant surge in ransomware attacks during the first half of 2025, with incidents increasing by approximately 1.4…
Apple yesterday released emergency security updates for iOS and iPadOS to patch a critical zero-day vulnerability in its core Image…
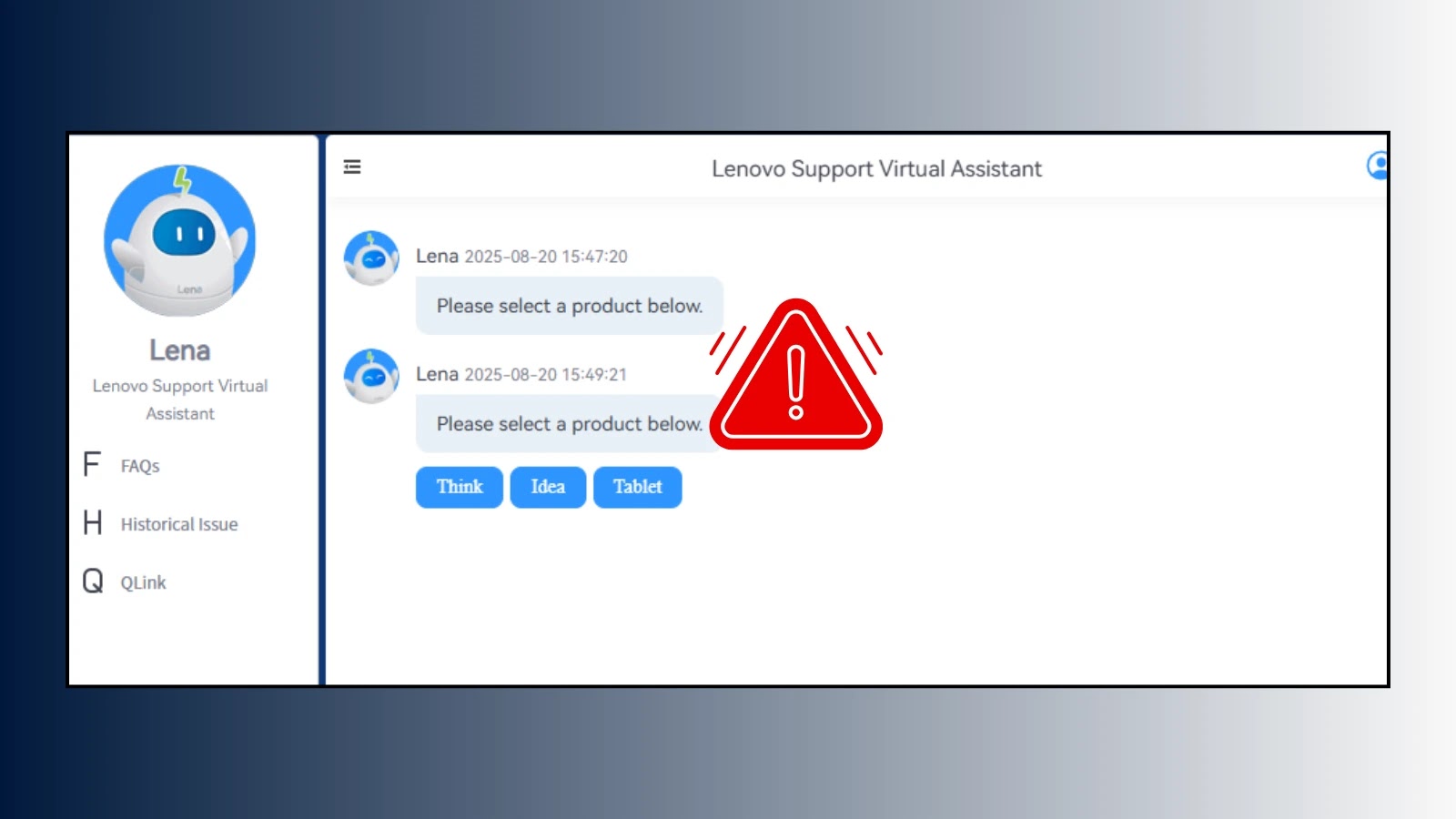
A critical security flaw in Lenovo’s AI chatbot “Lena” has been discovered that allows attackers to execute malicious scripts on…
Attackers have leveled up. Powered by AI and professional-grade toolkits, today’s social engineering scams are nearly impossible to tell apart…
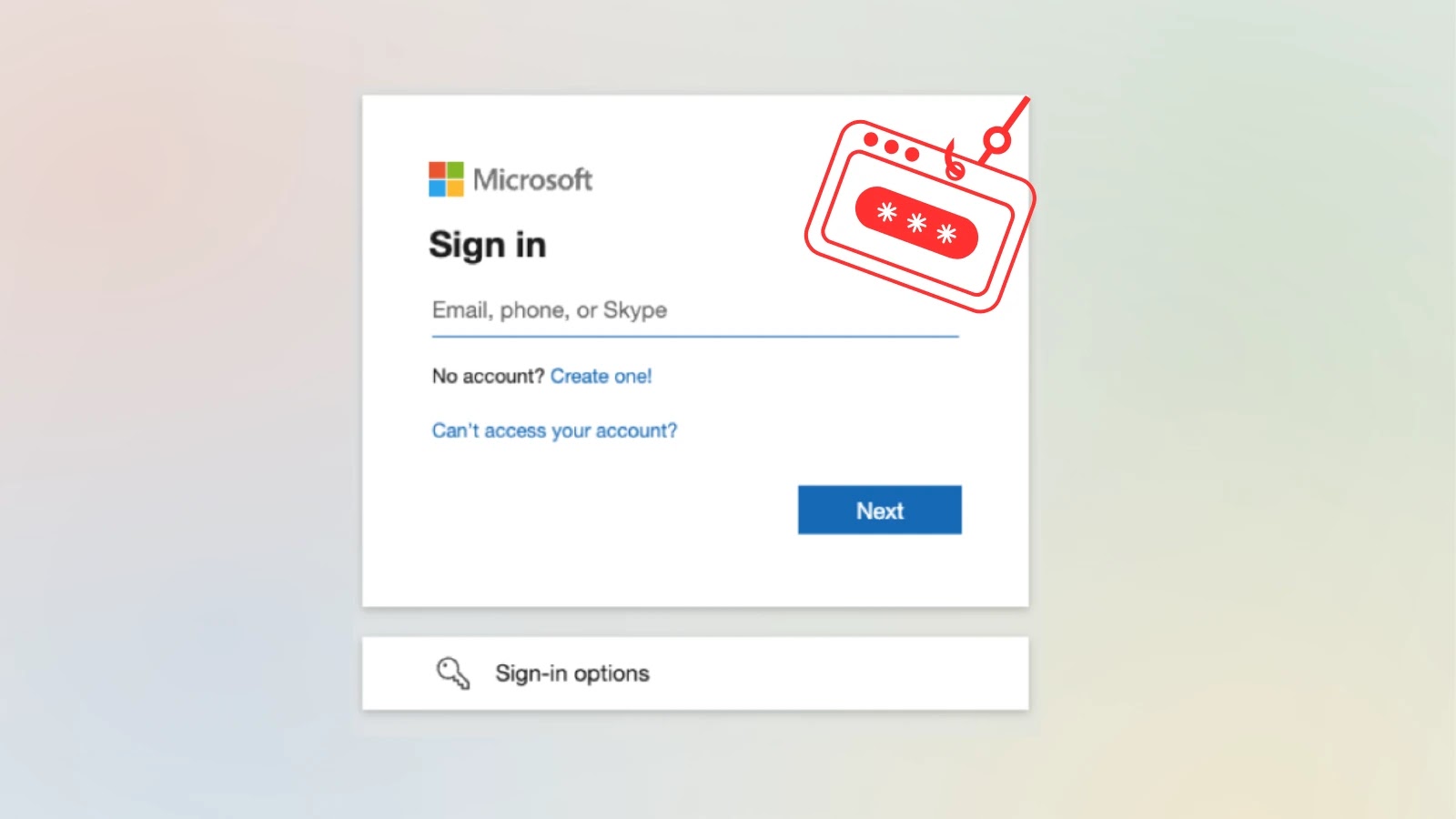
A novel and highly tricky phishing campaign is actively stealing Microsoft 365 credentials by exploiting Microsoft’s own Active Directory Federation…