Category: CyberSecurityNews
Every type of organization—whether it’s a multinational giant with thousands of employees or a single tech enthusiast running a homelab—needs…
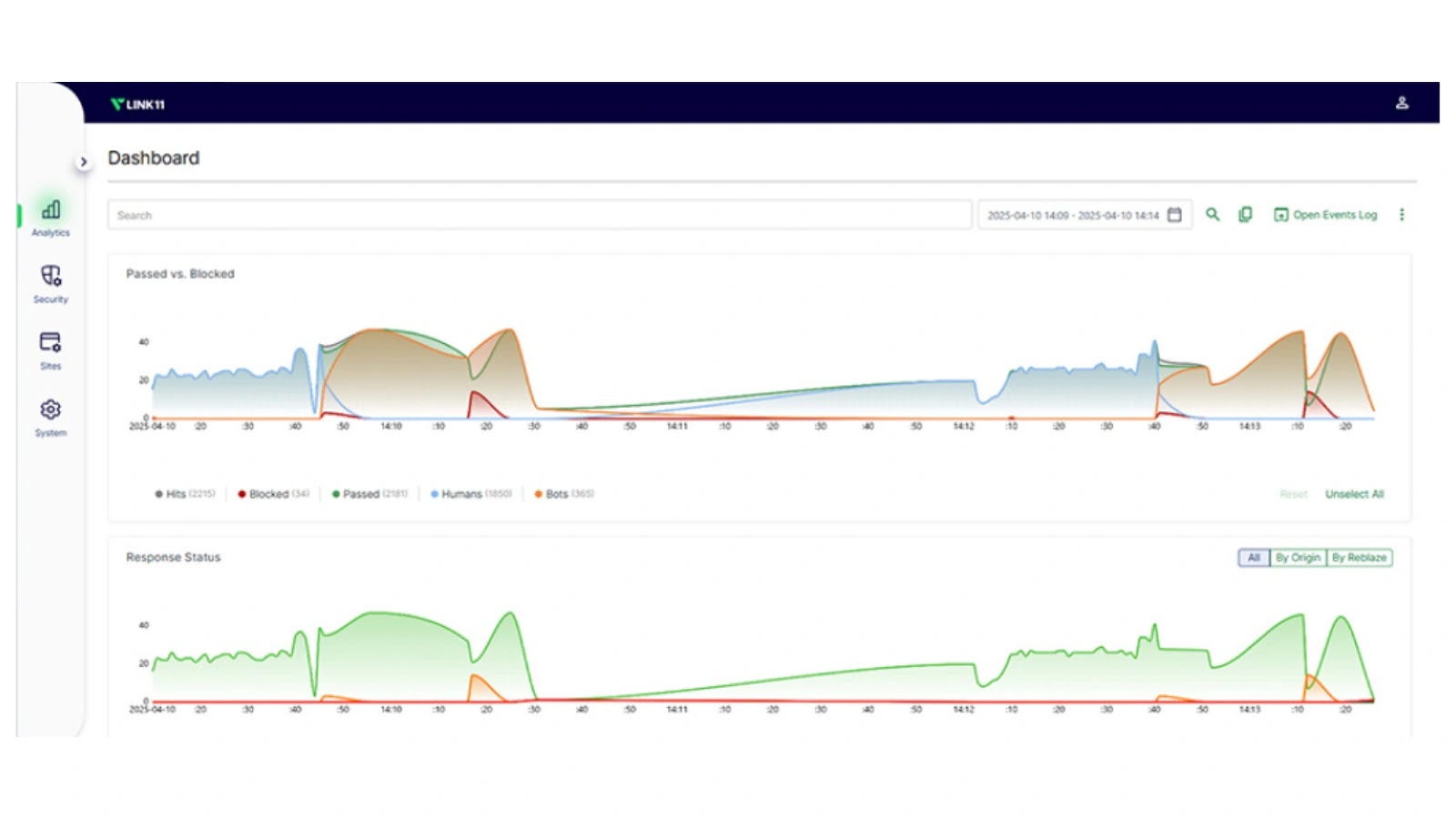
Link11, a Germany-based global IT security provider, has released insights into the evolving cybersecurity threat landscape and announced the capabilities…
Git 2.51.0 has been officially released after an accelerated 8-week development cycle, introducing significant performance improvements and security enhancements that…
Okta has announced the launch of the Auth0 Customer Detection Catalog, a comprehensive open-source repository designed to enhance proactive threat…
Microsoft’s comprehensive suite of online services, including the central Office.com portal, is currently experiencing a significant and widespread outage, leaving…
An alleged threat actor has listed a Windows Zero-Day Remote Code Execution (RCE) exploit for sale, claiming it targets fully…
A significant security vulnerability has been discovered in Microsoft’s Copilot for M365 that allowed users, including potential malicious insiders, to…
Cybercriminals are increasingly exploiting generative artificial intelligence platforms to orchestrate sophisticated phishing campaigns that pose unprecedented challenges to traditional security…
A sophisticated new malware strain targeting Linux environments has emerged, demonstrating advanced evasion capabilities that challenge traditional endpoint detection and…
The cybersecurity landscape continues to witness sophisticated threat actors developing increasingly complex attack methodologies to infiltrate organizational networks and steal…
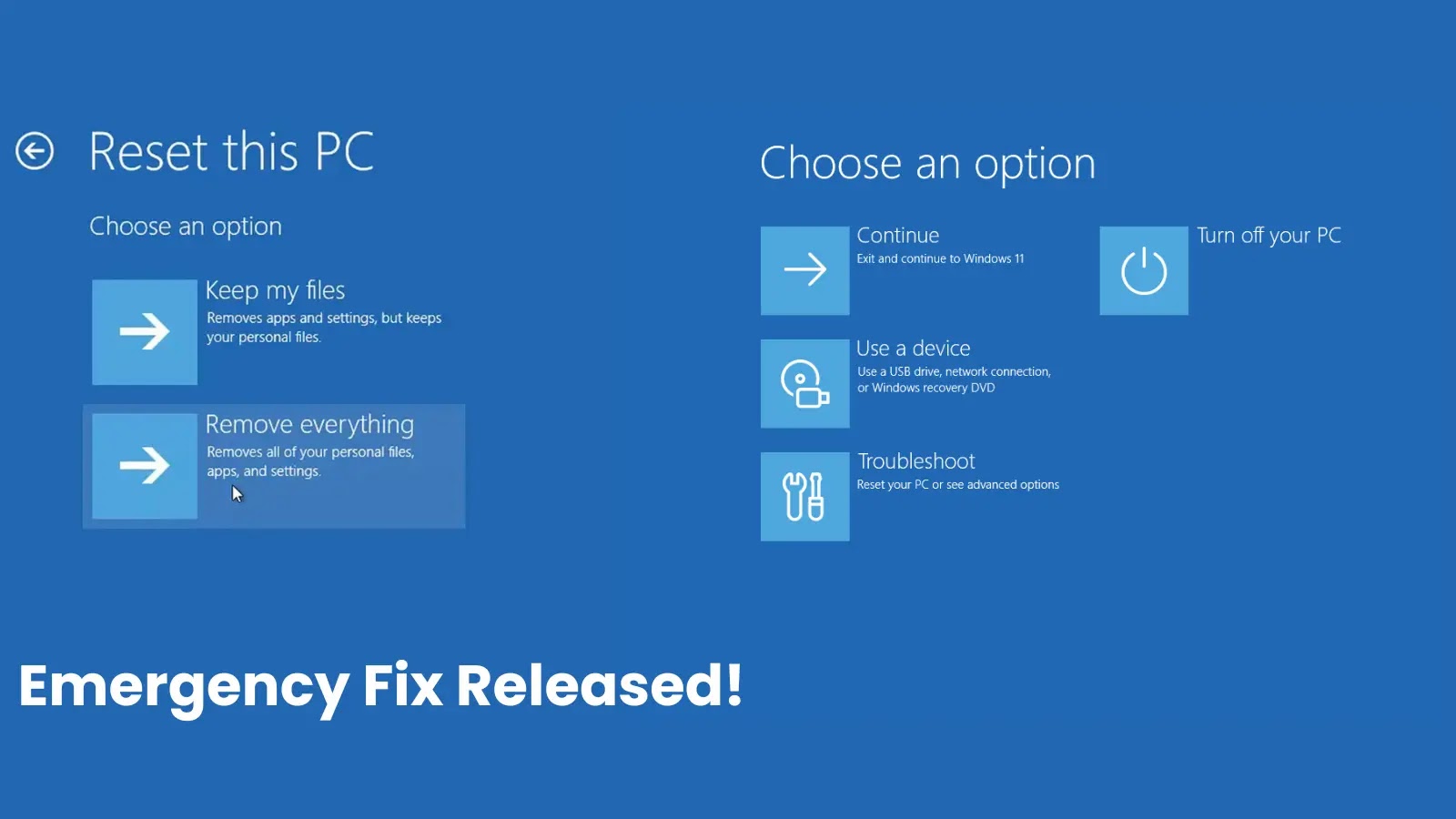
Microsoft has issued critical out-of-band updates on August 19, 2025, to address a significant issue affecting Windows reset and recovery…
A sophisticated campaign uncovered where adversaries are exploiting CVE-2023-46604, a critical remote code execution vulnerability in Apache ActiveMQ, to compromise…