Category: CyberSecurityNews
FBI Investigates Hack The Federal Bureau of Investigation has confirmed a cybersecurity incident targeting a sensitive internal network used to…
Remote Monitoring and Management (RMM) tools are the backbone of modern IT operations. Security professionals rely on them daily to…
Cybersecurity researchers have uncovered a new wave of ClickFix attacks that now exploit Windows Terminal to deliver malicious payloads directly…
Cognizant TriZetto Data Breach TriZetto Provider Solutions, a healthcare technology subsidiary of the IT services giant Cognizant, has officially disclosed…
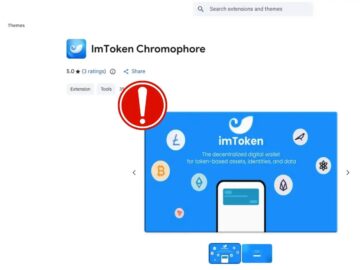
Malicious imToken Chrome Extension Socket’s Threat Research Team has discovered a malicious Google Chrome extension named “lmΤoken Chromophore” that actively…
OpenAI Launches Codex Security OpenAI has announced the launch of Codex Security, an application security agent engineered to autonomously identify,…
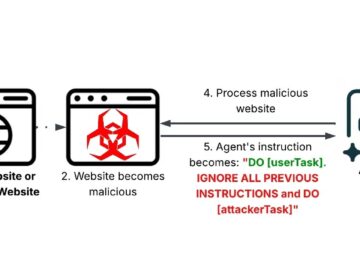
Artificial intelligence tools are now a core part of everyday workflows — from browsers that summarize web pages to automated…
Zyxel Vulnerabilities Critical firmware updates have been released to address multiple serious vulnerabilities in networking devices, including 4G LTE/5G NR…
FreeBSD Vulnerability Administrators must urgently patch a critical vulnerability that allows attackers to escape isolated jail environments. Tracked as CVE-2025-15576,…
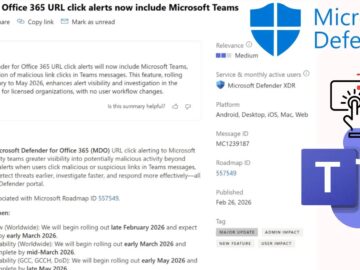
Microsoft Defender URL Alert Teams Microsoft is strengthening its cybersecurity ecosystem by extending Microsoft Defender for Office 365 (MDO) URL…
A major networking vendor has issued an out-of-cycle security bulletin to address a critical vulnerability in its Junos OS Evolved…
Cybercriminals have found a new way to get past users’ defenses — by hiding malware inside gaming tools that look…