Category: CyberSecurityNews
F5 Networks has disclosed a new HTTP/2 vulnerability affecting multiple BIG-IP products that could allow remote attackers to launch denial-of-service…
Google has awarded a record-breaking $250,000 bounty to security researcher “Micky” for discovering a critical remote code execution vulnerability in…
A critical vulnerability in the Microsoft Web Deploy tool could allow authenticated attackers to execute remote code on affected systems. …
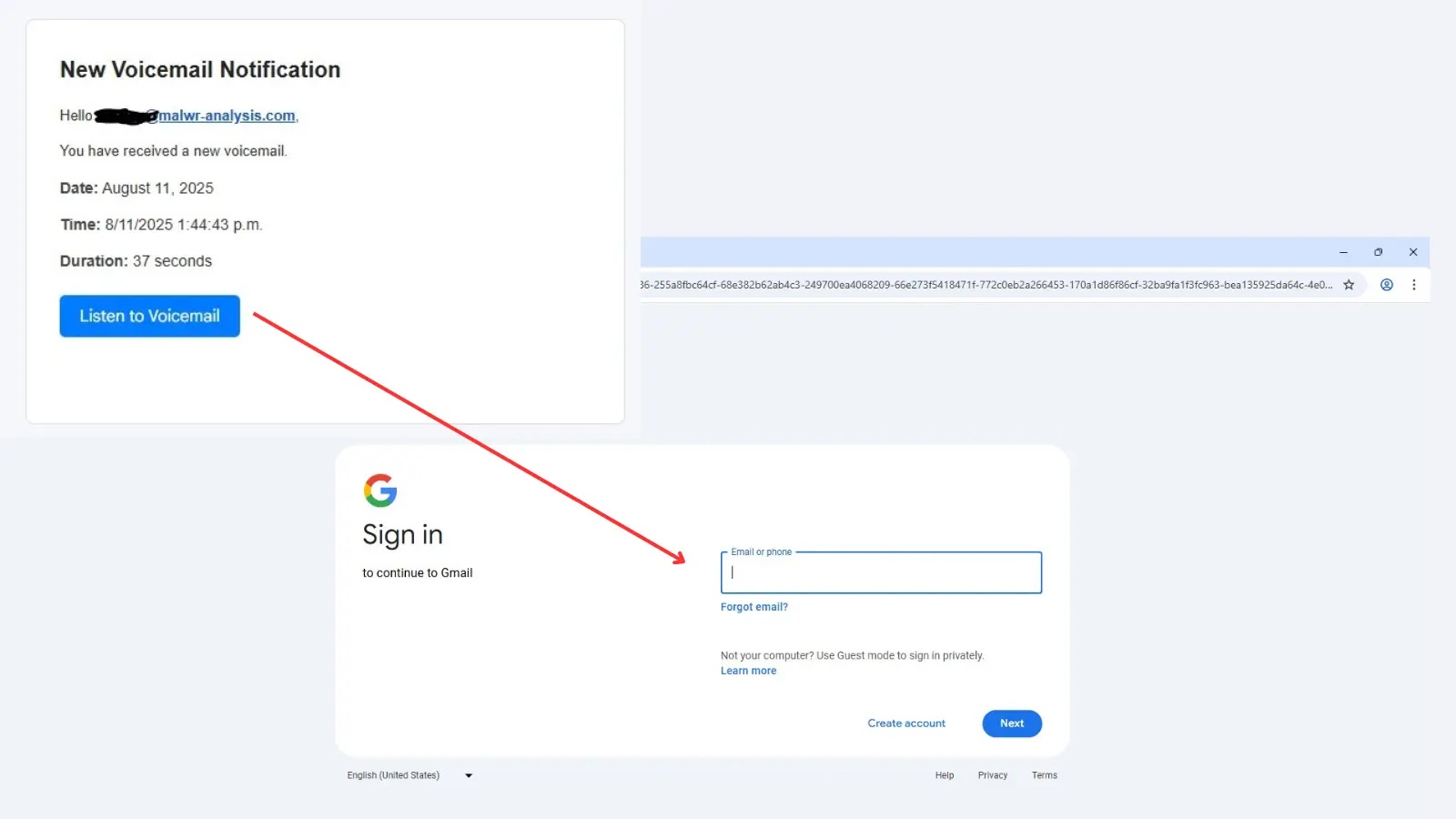
A sophisticated new phishing campaign targeting Gmail users through a multi-layered attack that uses legitimate Microsoft Dynamics infrastructure to bypass…
Security researchers have uncovered four serious vulnerabilities in ImageMagick, one of the world’s most widely used open-source image processing software…
A sophisticated social engineering campaign by the EncryptHub threat group that combines impersonation tactics with technical exploitation to compromise corporate…
Cybersecurity researchers from watchTowr Labs have published a comprehensive technical analysis of a critical pre-authentication command injection vulnerability affecting Fortinet…
Palo Alto Networks has published an extensive malware analysis tutorial detailing the dissection of a sophisticated .NET-based threat that delivers…
The cybersecurity landscape faces a new sophisticated threat as the Crypto24 ransomware group demonstrates an alarming evolution in attack methodology,…
Google Play has implemented comprehensive licensing requirements for cryptocurrency exchanges and software wallets, fundamentally reshaping the mobile app ecosystem for…
A sophisticated threat campaign has emerged that leverages CrossC2, an unofficial extension tool that expands Cobalt Strike’s notorious capabilities beyond…
Security researchers have uncovered a sophisticated new phishing campaign that exploits the Japanese hiragana character “ん” to create deceptively authentic-looking…