Category: CyberSecurityNews
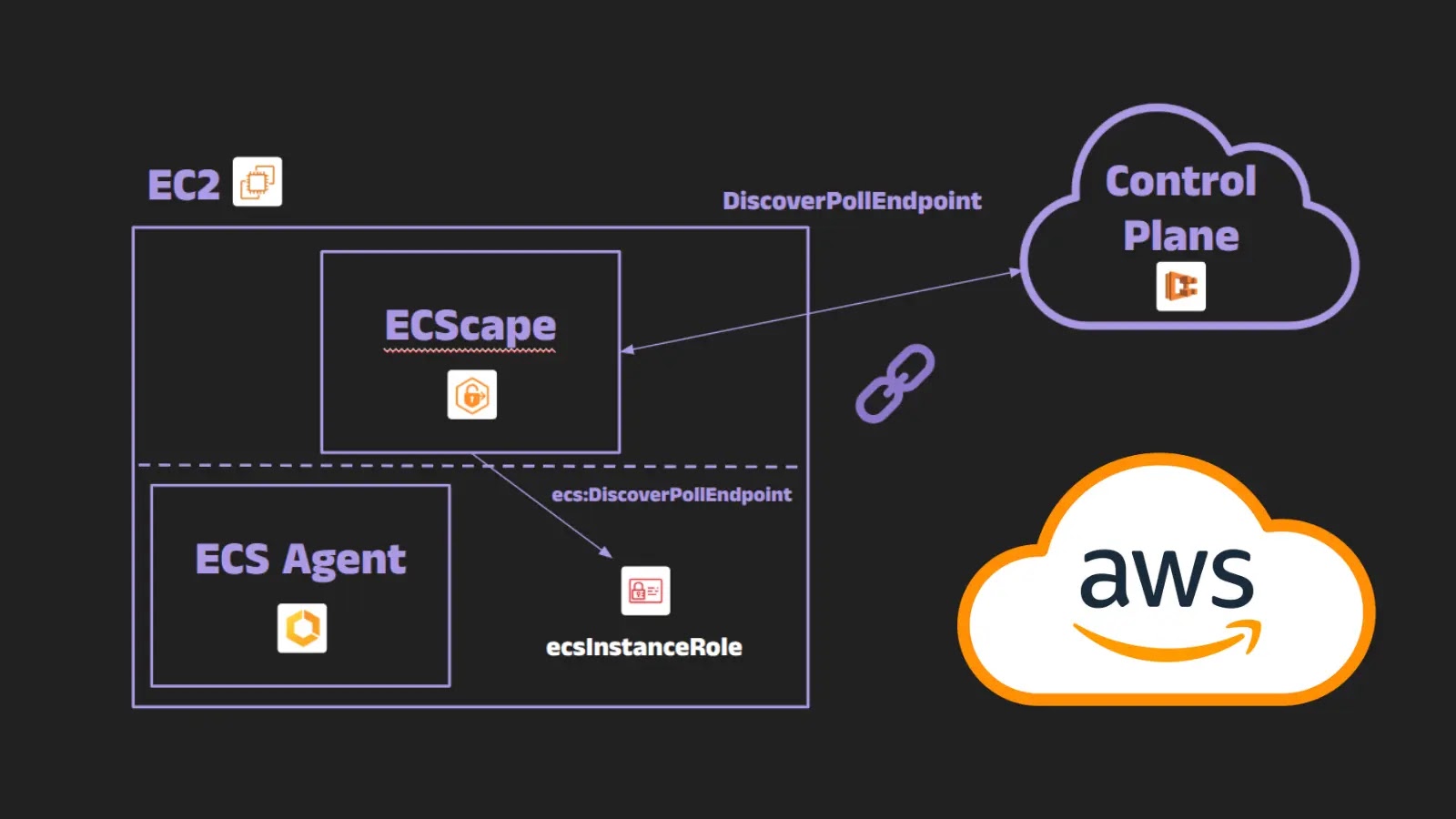
A sophisticated technique dubbed “ECScape” that allows malicious containers running on Amazon Elastic Container Service (ECS) to steal AWS credentials…
Cybersecurity researchers have uncovered a sophisticated malware campaign targeting the Go ecosystem through eleven malicious packages that employ advanced obfuscation…
A sophisticated cybercriminal operation known as GreedyBear has orchestrated one of the most extensive cryptocurrency theft campaigns to date, deploying…
A new and custom firmware for the popular Flipper Zero multi-tool device is reportedly capable of bypassing the rolling code…
CISA has issued an emergency advisory directing all Federal Civilian Executive Branch agencies to mitigate a newly disclosed Microsoft Exchange…
A new and custom firmware for the popular Flipper Zero multi-tool device is reportedly capable of bypassing the rolling code…
People don’t want to guess when they buy something – especially something complex or customizable. They want to feel like…
A sophisticated cybercriminal operation that targeted American tax preparation businesses through spearphishing campaigns has culminated in the extradition of Nigerian…
Cybercriminals have begun exploiting Scalable Vector Graphics (SVG) files as sophisticated attack vectors, transforming seemingly harmless image files into potent…
Two malicious npm packages have emerged as sophisticated weapons targeting WhatsApp developers through a remote-controlled destruction mechanism that can completely…
Cybersecurity firm SonicWall has officially addressed recent concerns about a potential new zero-day vulnerability in its Secure Sockets Layer Virtual…
WhatsApp has successfully dismantled 6.8 million accounts linked to fraudulent activities during the first half of 2024, representing a significant…