Category: CyberSecurityNews
Since mid-2022, Chinese military-industrial networks have reportedly been the target of highly sophisticated cyber intrusions attributed to US intelligence agencies….
Mozilla has issued an urgent security alert to its developer community following the detection of a sophisticated phishing campaign specifically…
A critical security vulnerability affecting multiple FUJIFILM printer models could allow attackers to trigger denial-of-service (DoS) conditions through malicious network…
Researchers exploited CVE-2025-38001—a previously unknown Use-After-Free (UAF) vulnerability in the Linux HFSC queuing discipline—to compromise all Google kernelCTF instances (LTS,…
In recent weeks, cybersecurity teams have observed a surge in malicious campaigns exploiting Windows shortcut (LNK) files to deliver sophisticated…
Cybersecurity researchers have uncovered a groundbreaking pattern that could revolutionize how organizations prepare for emerging threats. A comprehensive analysis reveals…
The largest cryptocurrency hack ever recorded involved the theft of 127,426 BTC from Chinese mining pool LuBian in December 2020. …
A novel lateral movement technique that exploits BitLocker’s Component Object Model (COM) functionality to execute malicious code on target systems….
A critical HashiCorp security vulnerability affecting Vault Community Edition and Enterprise versions could allow privileged operators to execute arbitrary code…
A severe vulnerability in the popular AI-powered code editor Cursor IDE, dubbed “CurXecute,” allows attackers to execute arbitrary code on…
A sophisticated new wave of cyberattacks attributed to North Korea’s notorious APT37 (Reaper) group is leveraging advanced malware hidden within…
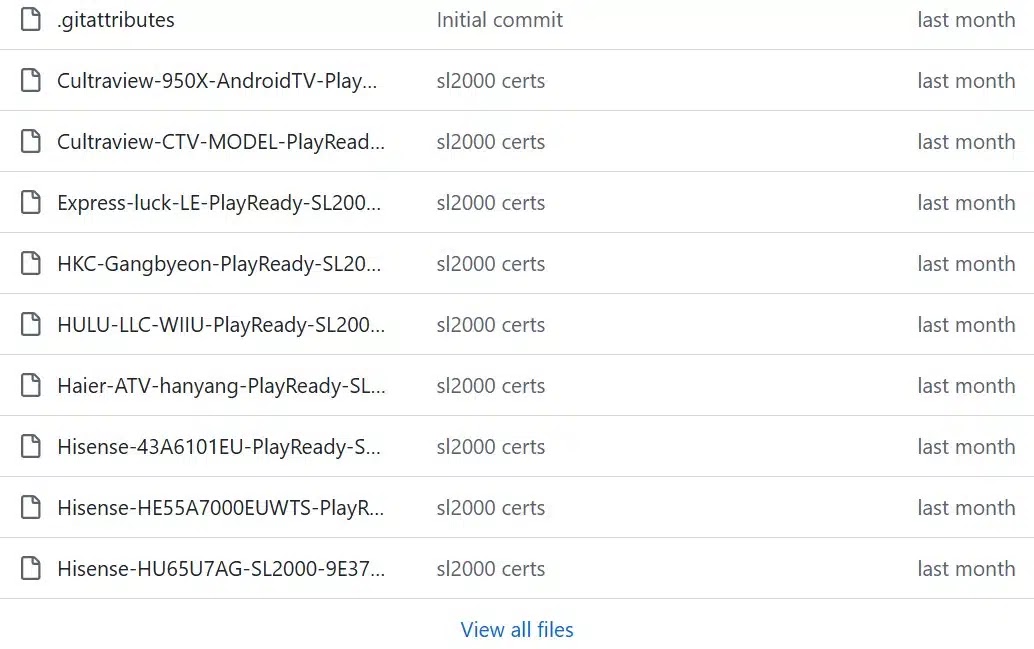
A significant security breach has compromised Microsoft’s PlayReady Digital Rights Management (DRM) system, exposing critical certificates that protect premium streaming…