Category: CyberSecurityNews
A groundbreaking investigation has pulled back the curtain on one of Russia’s most clandestine intelligence operations, revealing unprecedented details about…
A sophisticated supply chain attack targeting JavaScript developers emerged on Friday, July 18th, 2025, when cybercriminals compromised multiple popular npm…
The breach of Tehran-based security contractor Amnban has ripped the cover off a multi-year espionage program that quietly burrowed into…
Cybersecurity researchers have uncovered a sophisticated attack campaign targeting poorly managed Linux servers through SSH brute force attacks to deploy…
The Lazarus Group’s long-running recruitment lure has resurfaced as “ClickFake Interview”, anchored on the freshly registered waventic[.]com site. Candidates progress…
[London, UK] July 2025 – As cryptocurrency continues its evolution into a mainstream financial asset class, a growing number of…
A sophisticated phishing campaign targeting Web3 developers has emerged, exploiting the growing interest in artificial intelligence platforms to deliver credential-stealing…
Hypervisor security represents a critical foundation for protecting virtualized infrastructure, as a single compromise at the hypervisor level can potentially…
The rise of clandestine “travel agencies” on darknet forums has reshaped the cyber-crime landscape, morphing traditional card-skimming into a full-fledged…
Quality threat intelligence has traditionally been the domain of enterprise-level budgets and premium subscriptions. The kind of fresh, actionable data…
The Cybersecurity and Infrastructure Security Agency (CISA), FBI, Department of Health and Human Services, and Multi-State Information Sharing and Analysis…
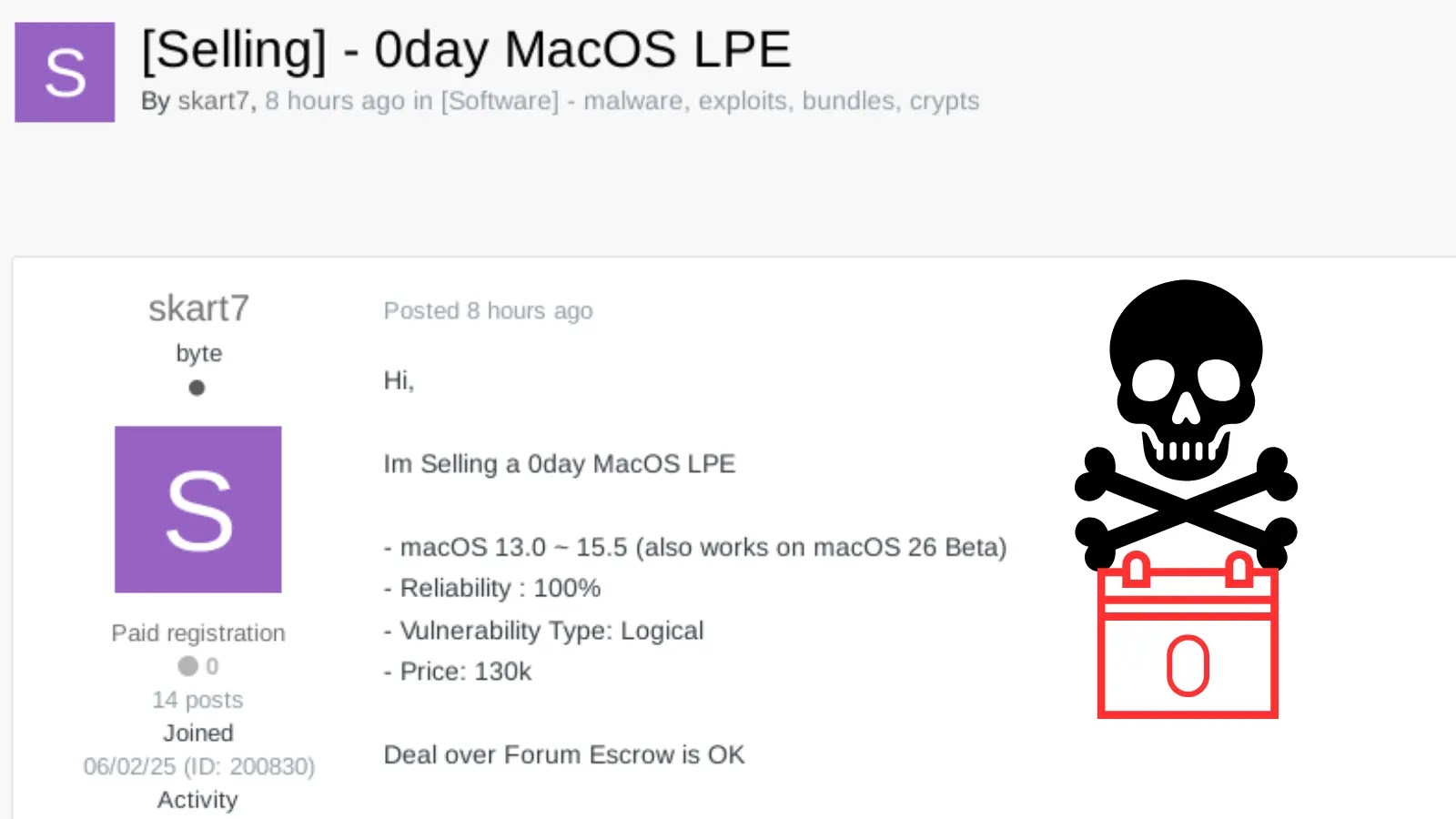
A threat actor known as “skart7” is allegedly offering a zero-day Local Privilege Escalation (LPE) exploit targeting Apple’s macOS operating…